Navigating the Web Safely: Understanding Social Engineering and Browser Security
In the vast and interconnected world of the internet, our reliance on browsers to explore, work, and socialize is undeniable. However, this convenience comes with its share of risks, especially from social engineering attacks that exploit human psychology rather than technological vulnerabilities. Understanding social engineering and its implications for browser security is crucial for secure web browsing.
What is Social Engineering?
Social engineering is a sophisticated manipulation technique that exploits human errors to gain private information, access, or valuables. Instead of relying on brute-force attacks or software vulnerabilities, social engineers manipulate individuals into breaking standard security procedures. NIST defines it as “The act of deceiving an individual into revealing sensitive information, obtaining unauthorized access, or committing fraud by associating with the individual to gain confidence and trust.”
The Threat to Browser Security
When it comes to browser security, social engineering attacks often take the form of phishing scams, baiting, pretexting, or quid pro quo offers. These attacks are designed to trick users into willingly handing over sensitive information or downloading malware.
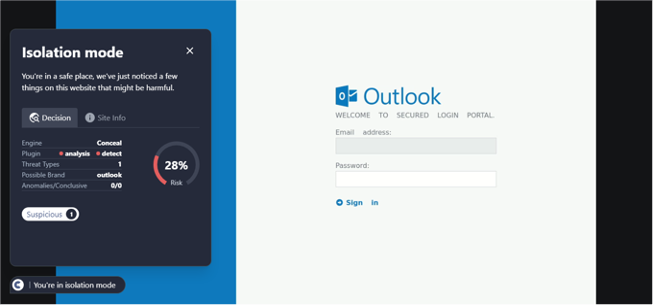
Phishing Scams
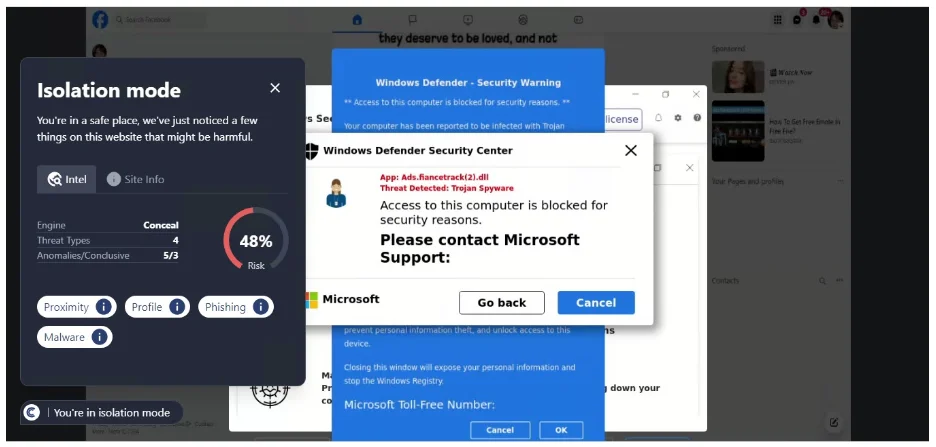
Phishing scams are one of the most common forms of social engineering. They involve attackers disguising themselves as trustworthy entities to lure individuals into providing sensitive data. This could be through an email that mimics the appearance of a legitimate company, directing the user to a fraudulent website that can capture login credentials or personal information. To learn more about phishing, check out our recent whitepaper here.
Baiting and Pretexting
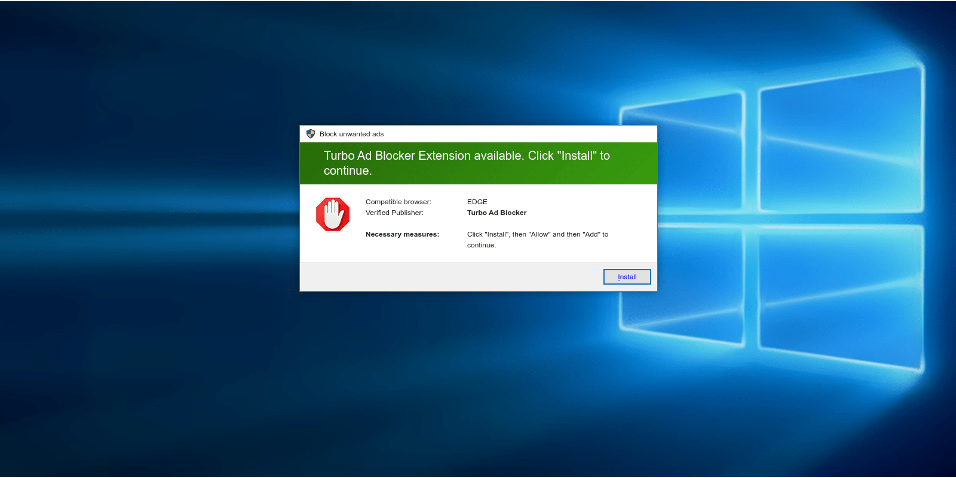
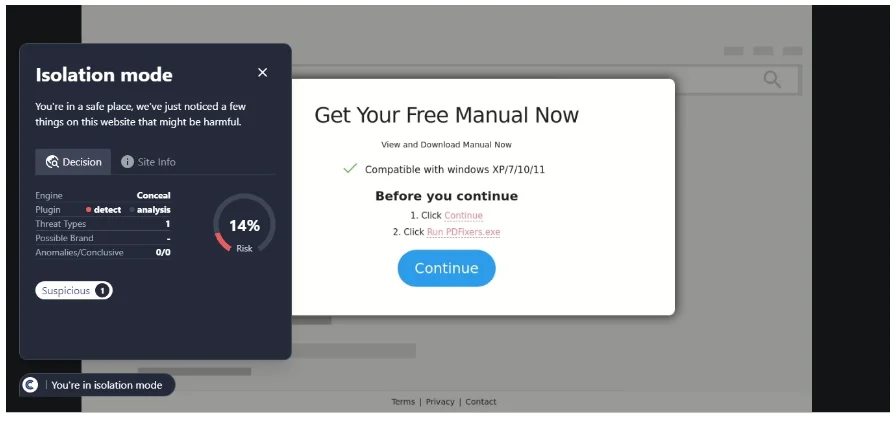
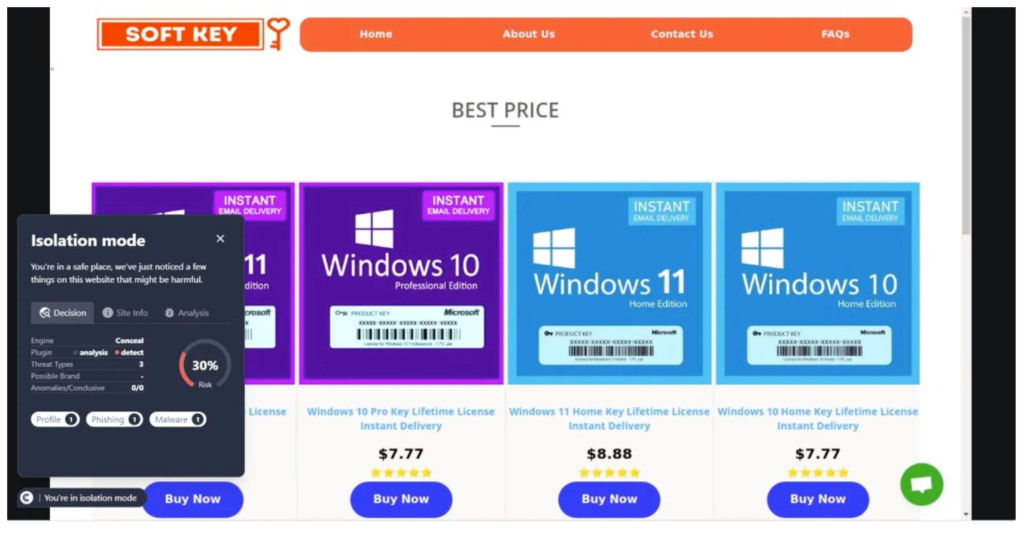
Baiting involves offering something enticing to the victim in exchange for information or access, such as the promise of free software download that is actually malware. Pretexting, on the other hand, involves creating a fabricated scenario to steal victims’ personal information. The attacker may pretend to need the information to confirm the victim’s identity, tricking them into divulging confidential details.
Quid Pro Quo
Quid pro quo attacks promise a benefit in exchange for information. This could be as simple as an attacker posing as a tech support agent offering to fix a non-existent problem on the user’s computer in exchange for remote access or sensitive information.
Maximizing Browser Security for Secure Web Browsing
To protect against social engineering threats, it’s essential to enhance your browser security with a mix of technical measures and vigilant practices.
Stay Informed
The first step towards secure web browsing is awareness. Stay informed about the latest social engineering tactics as attackers constantly refine their methods. Understanding the types of social engineering attacks can help you spot and avoid them.
Think Before You Click
Avoid clicking on links in unsolicited emails or messages. If an offer seems too good to be true, it probably is. Verify the legitimacy of any request by contacting the company directly through a known, official channel.
Use Multi-Factor Authentication
Multi-factor authentication adds an extra layer of security by requiring two or more verification methods to access your accounts. Even if a social engineer gains your password, this can prevent unauthorized access.
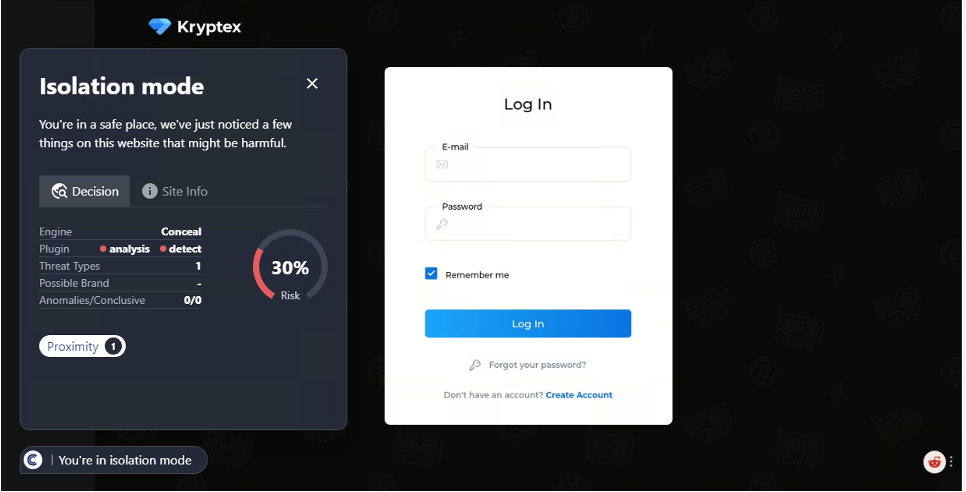
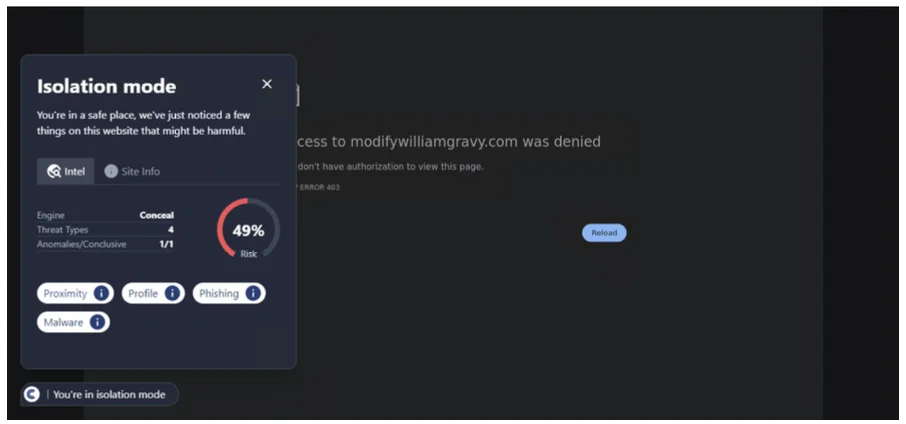
Invest in Browser Security
An additional, potent layer of defense in the quest for secure web browsing is the investment in a specialized browser security plugin, such as ConcealBrowse. These plugins are designed to enhance your browsing experience by providing real-time protection against a variety of online threats, including those stemming from social engineering tactics.
Conclusion
Social engineering poses a significant threat to browser security and secure web browsing, exploiting human vulnerabilities rather than technical ones. By staying informed, practicing vigilance, and employing robust security measures, you can significantly reduce the risk of falling victim to these manipulative attacks. Remember, in the battle for online security, knowledge and caution are your best defenses.