Browser-Based Threat Report: Feb 19
Browser-Based Threat Report
Week of February 19th, 2024
ConcealBrowse is leveraged by teams across the world to combat weaponized URLs. The technology is constantly analyzing suspicious web artifacts to identify risks in the form of drive-by attacks, phishing portals, and other threats that materialize while browsing.
At Conceal, your digital safety is our utmost priority. Our weekly threat report for the week of February 19th, 2024, unveils critical insights into the ever-evolving landscape of online threats.
The following report highlights recently detected sites that were deemed suspicious:
_____________
SHA-256: 0bc4f970d3b424ee02ece78df2e610974b72fb09e964fb6da8964056077d0ee2
screenshot of credential phishing page
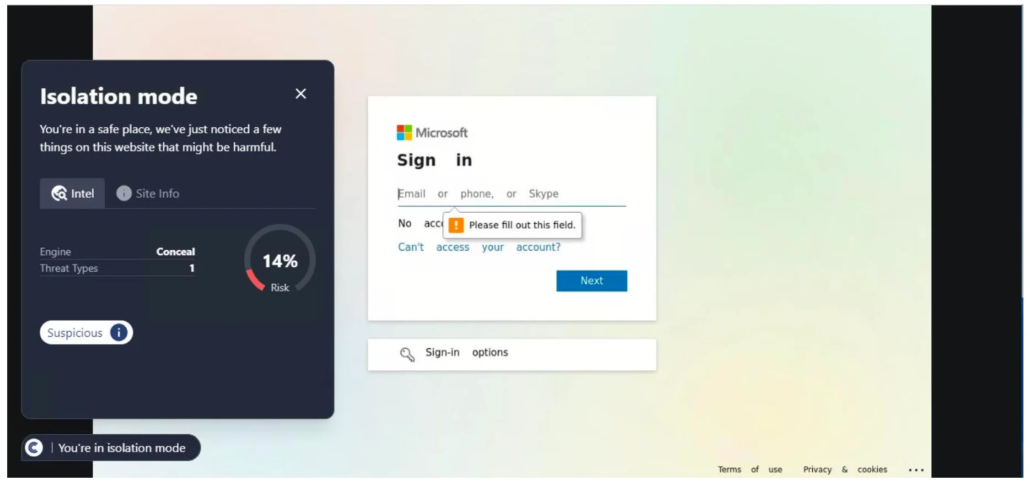
This URL was first detected by ConcealBrowse on February 16th, the same day that other security vendors started reporting on it. It was initially detected by 10 security vendors, and sixteen are now reporting the page as malicious. ConcealBrowse successfully intervened with a 14% risk assessment.
This is a classic example of credential phishing. The site copies the exact format of the Microsoft single sign on page to steal credentials from unsuspecting users. To make the page more believable, attackers will verify that the email address is valid before proceeding to ask a password. This makes it harder to check the page for legitimacy, which is why it is crucial to have protection in place that blocks user input such as ConcealBrowse.
Conceal Recommendation: Detection of phishing sites is not enough, you need to actively block users from entering credentials into suspected credential theft sites like you can do with the Isolation feature in C0ncealBrowse.
_____________
SHA-256: 52c1e7a2c36be28c42455fe1572d7d7918c3180cad99a2b82daa2a38a7e7bb23
An example of the pop-ups found connected to this page
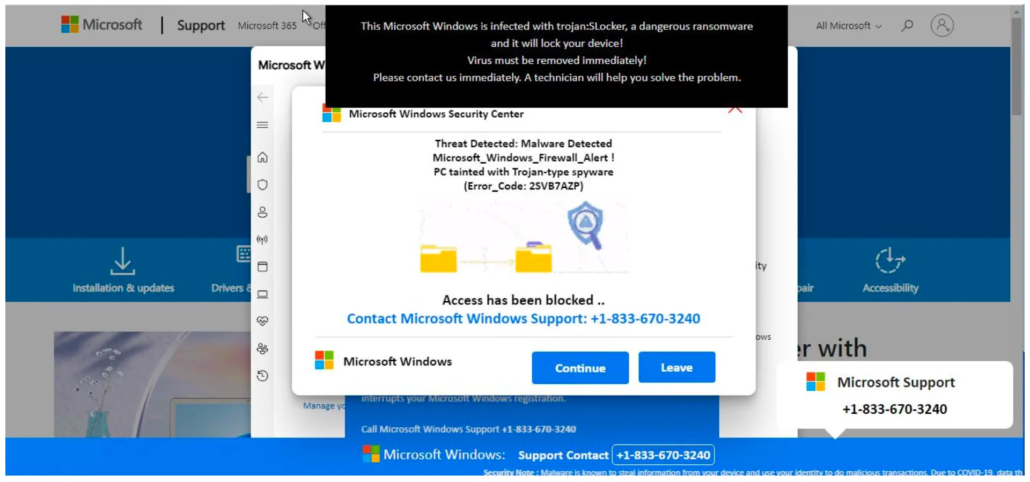
This URL was detected by ConcealBrowse on February 16th with a 28% risk assessment. It was first detected by one security vendor on February 7th and currently is detected by two vendors. ConcealBrowse intervened due to phishing and suspicious activity.
While the page is currently blank, the IP address is connected to multiple instances of malicious pop-ups. These pop-ups often imitate Microsoft, and demand that the user call a phone number to fix it. These scams often tell the user to download remote access software onto their computer, resulting in both a financial loss and the theft of personal information.
Conceal Recommendation: Block the IP address and the URL using ConcealBrowse and monitor software being downloaded onto company machines. Additionally, Users should inform their IT team whenever they are prompted to conduct an action. Remember, any vendor contact should be routed through the IT team
_____________
SHA-256: 3938c63e8b782001c4b451b439634c1380b1e262d919e11ba7374862835d83e4
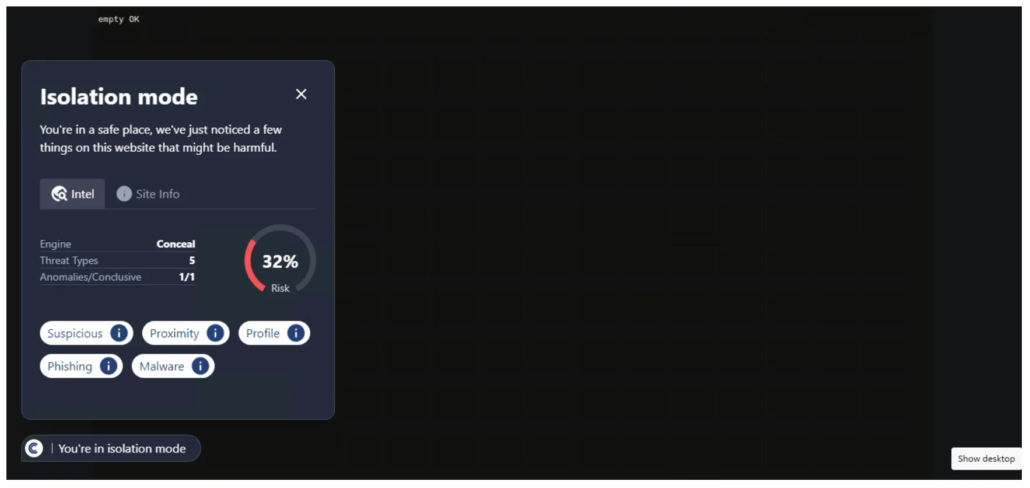
This URL was detected by ConcealBrowse on February 13th. It was first detected by one security vendor on January 9th, and there are currently four security vendors reporting this page for malicious activity. ConcealBrowse intervened with a 32% risk assessment due to malware and proximity to malicious IP addresses.
The IP address connected to this page was recently flagged for hosting a form of ransomware through a malicious popup. Users would click on the popup, and the executable file would download to their computer. Ransomware can be devastating, especially in cases where computers are connected to each other on a network and the malicious software can spread. Although the page is now down, ConcealBrowse still intervened to protect users in the future if the site becomes active again.
Conceal Recommendation: Rely on active defense solutions such as ConcealBrowse. When ConcealBrowse intervenes on a page, all download attempts are blocked to protect users from malware such as this. Live analysis of the site allows for early intervention and prevents malicious downloads.
_____________
Valuable Outcomes
As this recent threat reports exemplify, ConcealBrowse offers comprehensive protection against many sophisticated cyber threats. Our advanced threat detection capabilities have successfully flagged and quarantined malicious web pages, preventing users from falling victim to various cyber-attacks. Conceal remains dedicated to upholding the integrity of online interactions, constantly refining our detection algorithms and threat identification protocols to ensure proactive protection against emerging cyber threats. By integrating cutting-edge technology and a robust security infrastructure, we empower users to confidently navigate the digital landscape, knowing that their online activities are shielded from potential harm.
Join the Conceal Community and claim your FREE ConcealBrowse licenses!
Join the Conceal Community today and fortify your online security for free! Don’t miss the chance to benefit from our advanced threat protection and stay one step ahead of cybercriminals. Experience peace of mind while browsing the internet, knowing that ConcealBrowse is your shield against the ever-evolving threat landscape. Take the proactive step towards a safer online experience – get your free ConcealBrowse license now and join a community committed to safeguarding your digital world.
Sign up for the Conceal Community and claim your free licenses by completing the form below.





