How ConcealBrowse Helps MSPs and MSSPs Expand Services and Increase Revenue
As an MSP or MSSP, your primary responsibility is to deliver top-notch security solutions to your clients while driving revenue and operational efficiency. The growing demand for cybersecurity solutions and the increasing sophistication of cyber threats make this task even more challenging. We are here to alleviate these challenges at the edge. Enter ConcealBrowse, an AI-powered browser security solution designed to enhance your service offerings and expand your business.
The Challenge
Phishing attacks and social engineering are among the top concerns for MSPs and MSSPs. These attacks exploit human psychology, making them difficult to counter with traditional educational measures and outdated detection systems. The fragmented and encrypted nature of the internet further complicates the protection of client assets.
The Solution
ConcealBrowse addresses these challenges head-on. By providing a secure, zero trust browsing experience, it actively blocks phishing links and counters social engineering tactics. Here’s how:
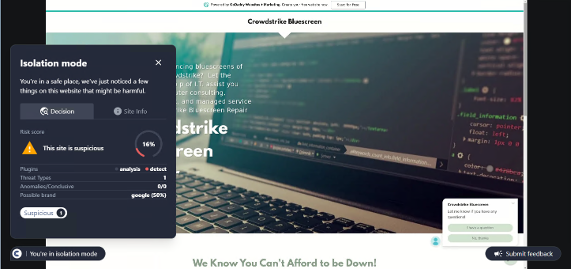
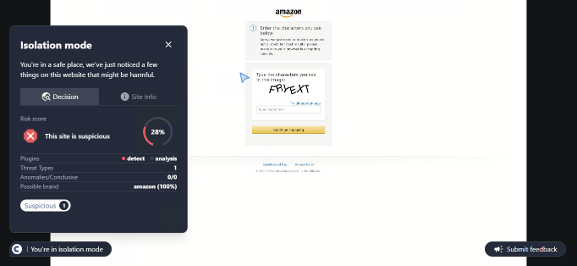
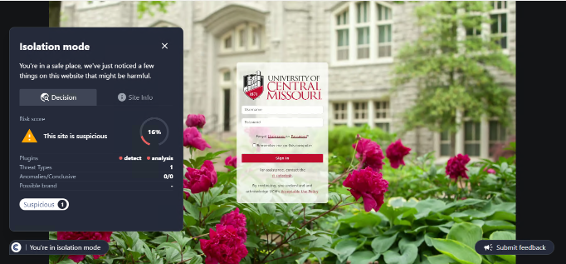
- AI-Powered Phishing Detection: ConcealBrowse leverages AI to detect and block phishing attempts in real time. This sophisticated detection mechanism adapts to rapidly evolving cyber threats, offering a robust defense against new and emerging attack vectors.
- Real-Time Threat Analysis: ConcealBrowse disrupts cyber threats early in the attack sequence. This proactive approach significantly reduces the risks of data theft, cyber extortion, and security breaches.
- User Privacy: ConcealBrowse is designed with user privacy in mind. It’s a lightweight extension that does not upload or retain sensitive browsing history, ensuring that your clients’ privacy is respected.
Business Outcomes
Implementing ConcealBrowse can lead to significant business outcomes for MSPs and MSSPs:
- New Revenue Streams: Bundle ConcealBrowse into your security services to generate new revenue and deliver innovative cybersecurity solutions.
- Enhanced Client Protection: By providing edge protection, you assure your clients that they are safeguarded against ransomware and credential theft.
- Operational Efficiency: Reduces the complexity of managing browser security, saving you time and money while allowing you to focus on delivering superior services.
- Proactive Threat Mitigation: Ensures potentially malicious activities are contained before they become significant issues, leading to faster and more effective threat mitigation.
Conclusion
In today’s rapidly evolving threat landscape, MSPs and MSSPs need advanced tools to stay ahead of cybercriminals. ConcealBrowse offers a comprehensive solution that enhances your service offerings, simplifies management, and provides peace of mind. Embrace ConcealBrowse to expand your cybersecurity services and safeguard your clients against the ever-present threat of phishing and social engineering attacks.
Join the Conceal Community:
Take your security to the next level by joining the Conceal community. Enjoy exclusive benefits and stay ahead of cyber threats. Learn more.