Browser-Based Threat Report: October 14
Browser-Based Threat Report
Week of October 14th, 2024
ConcealBrowse is leveraged by teams across the world to combat against weaponized URLs. The technology is constantly analyzing suspicious web artifacts to identify risk in the form of drive-by attacks, phishing portals, and other threats that materialize while browsing.
At Conceal, your digital safety is our utmost priority. Our weekly threat report for the week of October 14th, 2024, unveils critical insights into the ever-evolving landscape of online threats.
The following report highlights recently detected sites that were deemed suspicious:
_____________
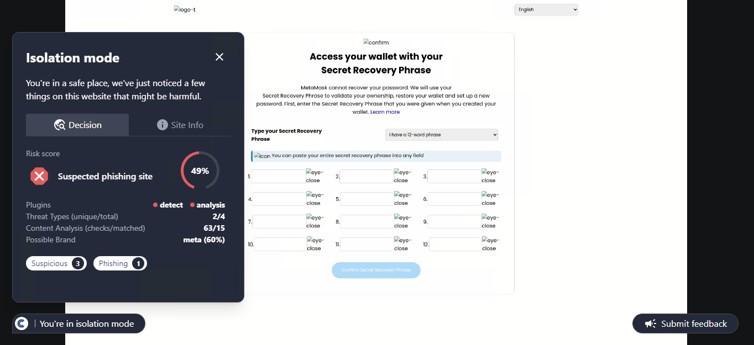
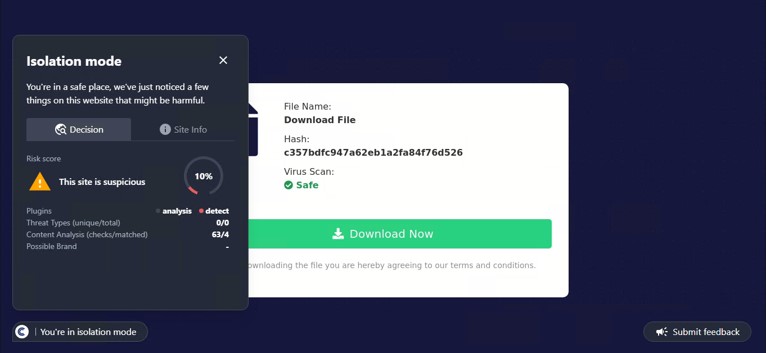
SHA-256: a6135e5df4af90e31a68c035fa029422f9d8d55495420f81b5992fd155fb862b
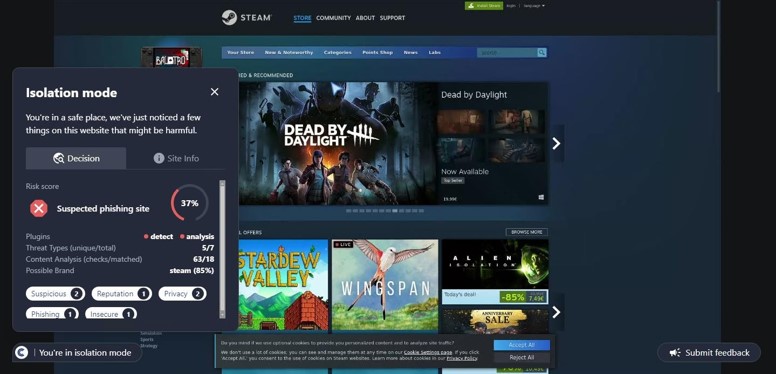
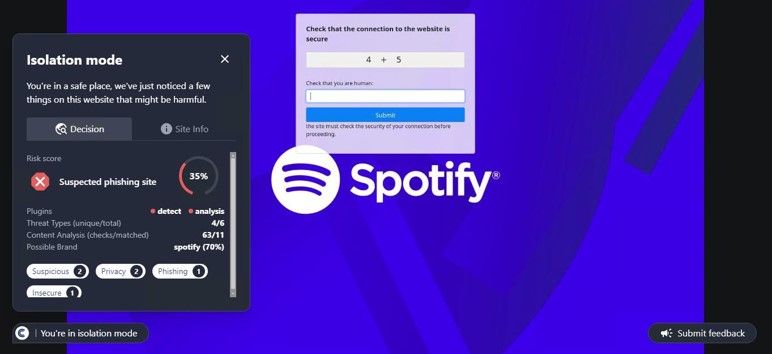
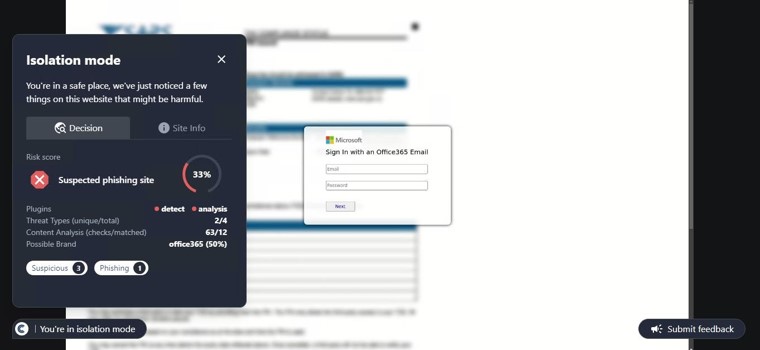
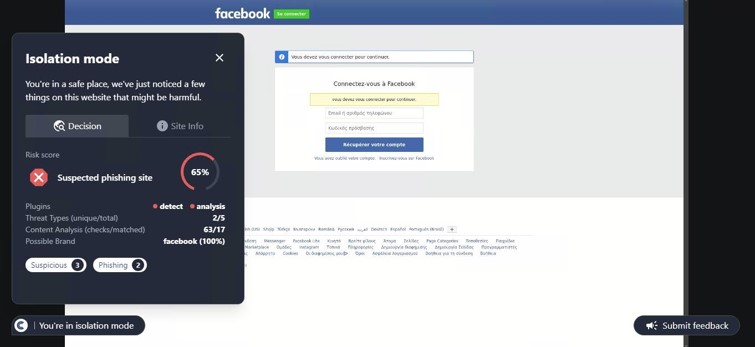
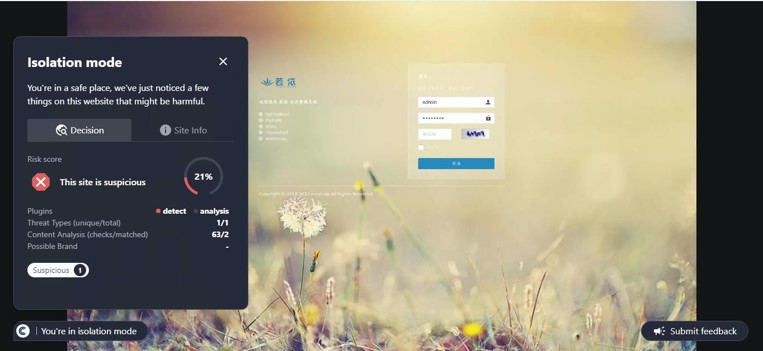
This site was first detected by ConcealBrowse on October 7th, the day after security vendors began reporting. It is currently detected by 16 vendors for phishing activity. ConcealBrowse intervened with a 37% risk assessment, citing the brand impersonation and poor site reputation.
This is a phishing page impersonating an online store brand, putting the victim at risk for theft of both their store library and payment information. The page is crafted with heavy discounts on several items, designed to entice the user to enter their credentials without verifying its authenticity. These credentials contain access to the entire library of previously purchased games from the user, allowing malicious actors to change the password and keep the library for themselves. ConcealBrowse’s intervention recognizes brand impersonation and isolates suspicious websites to keep users protected.
_____________
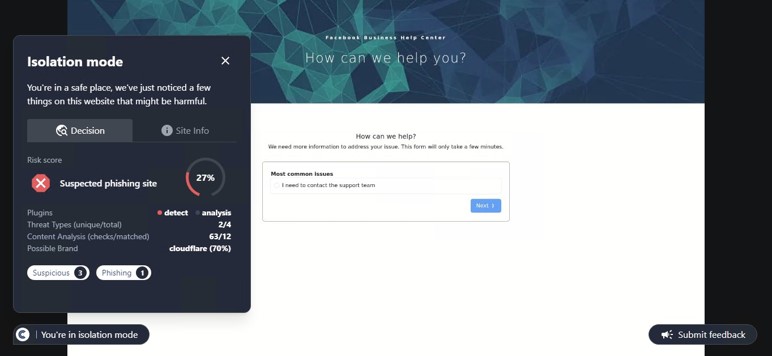
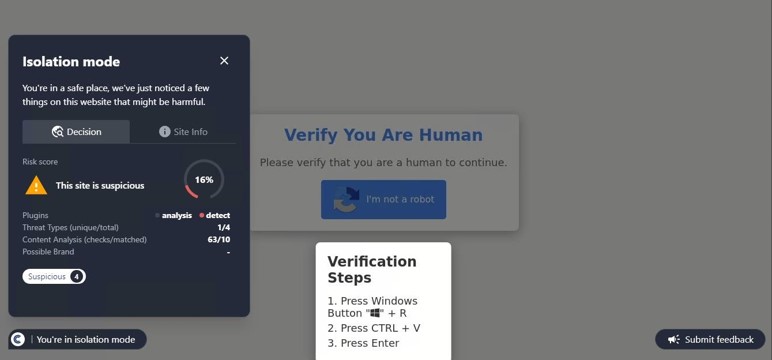
SHA-256: ca405cf8fb76648d0ffea23f61077e390d47bea0238b125d7de3512b3e64210f
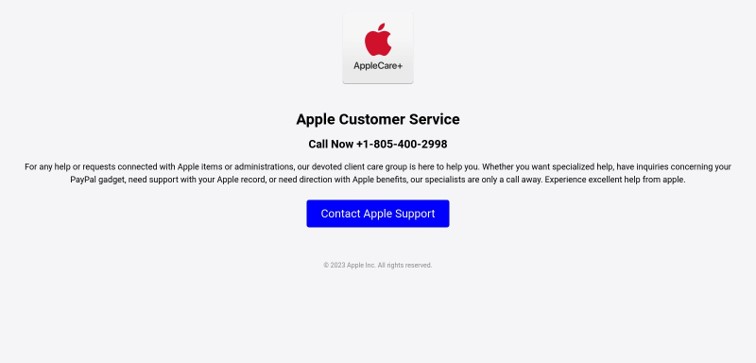
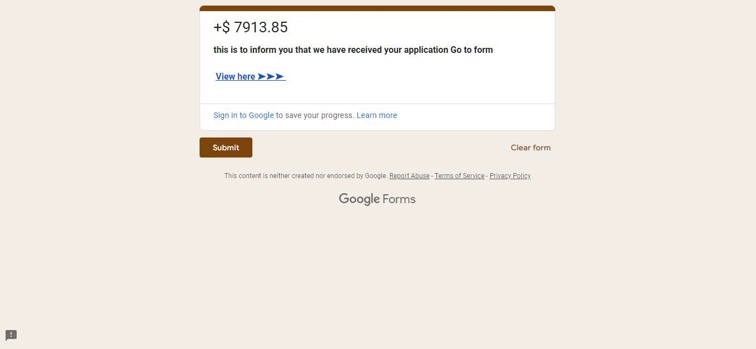
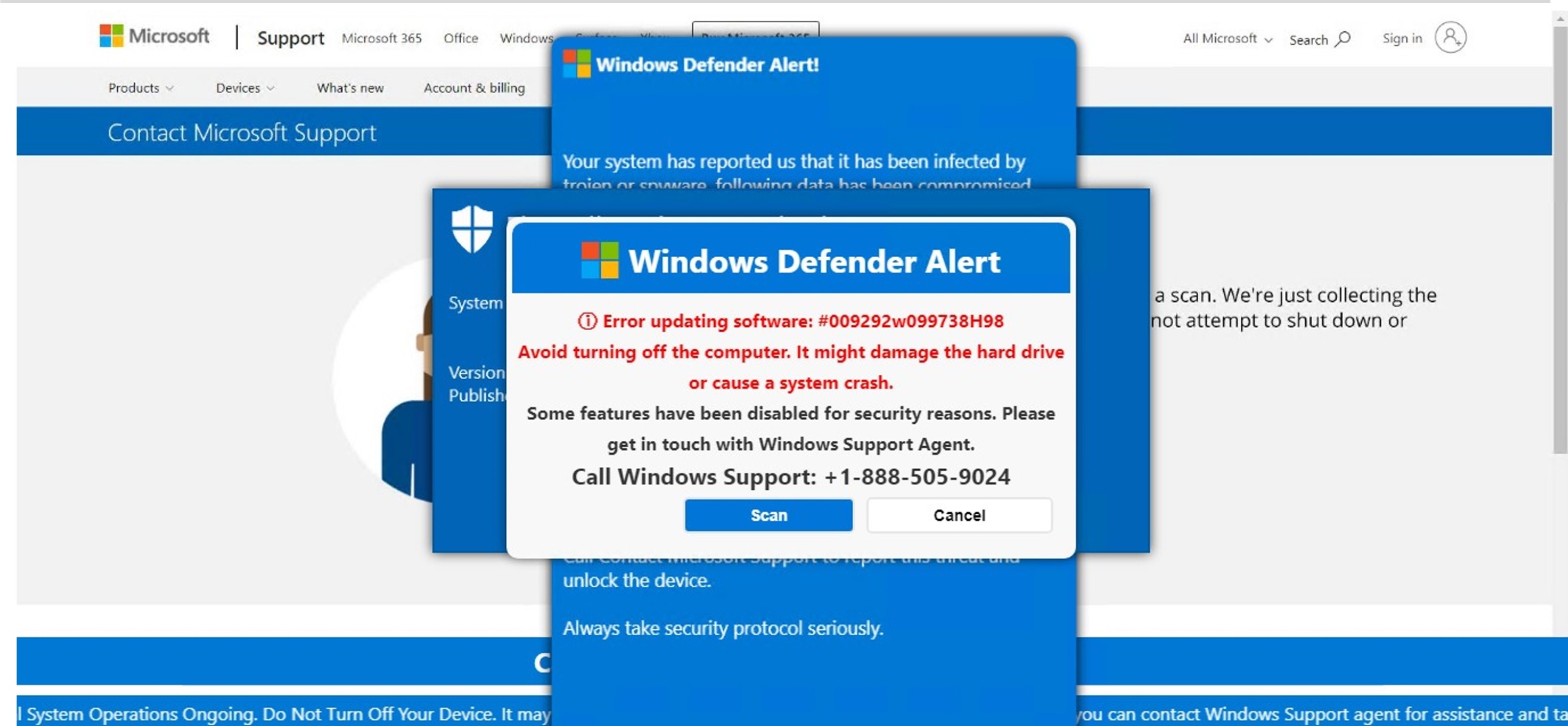
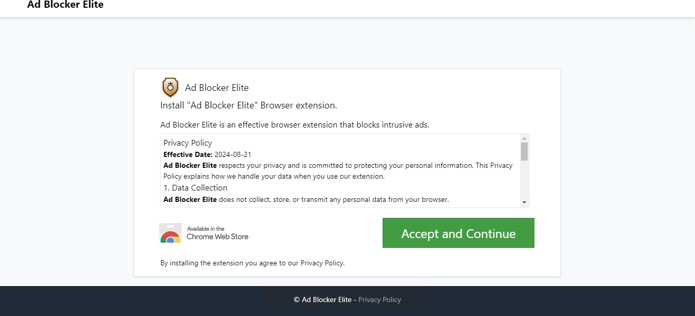
This site is hosting a fraudulent customer support page. Often, these sites are accompanied by alarming messages alerting the user that their account has been locked, or a payment has not properly processed. The purpose of these alerts is to prompt immediate action from the user before they can verify if the activity is legitimate. Once the user contacts the support number, malicious actors will use Social Engineering methods to attempt to steal credentials, financial information, or other sensitive data. ConcealBrowse’s intervention recognizes deceptive pages, warning users before they proceed and keeping their data protected.
_____________
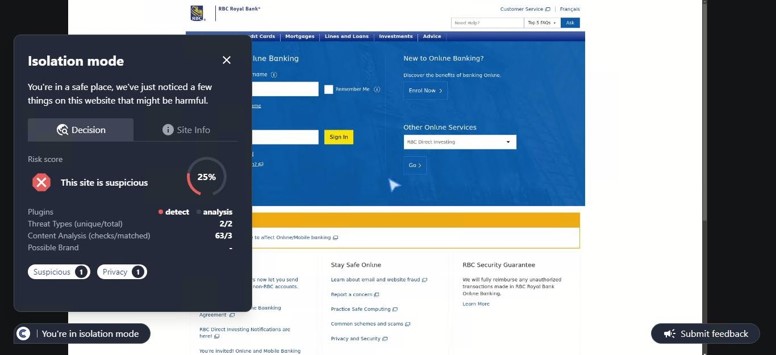
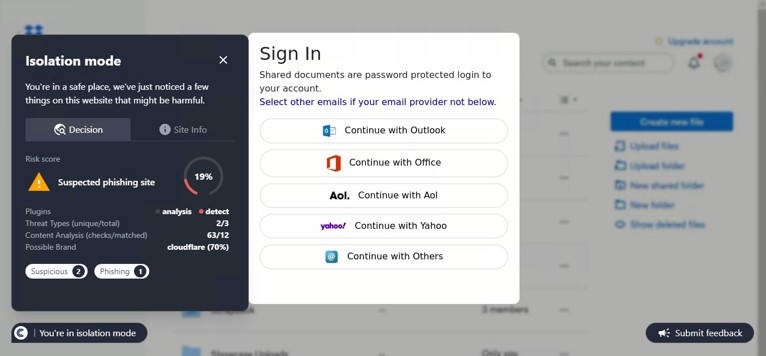
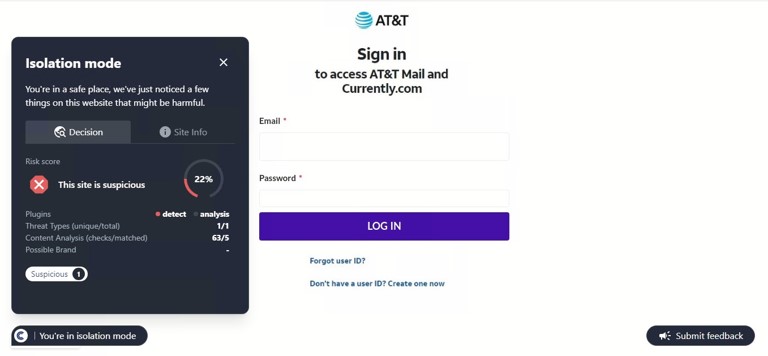
SHA-256: c8201752d7b2854798427e1ae65f919494c8ef7c76862bc69c111fc206ea83a1
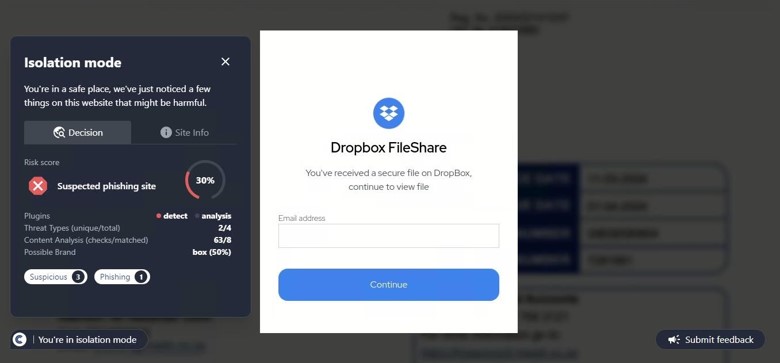
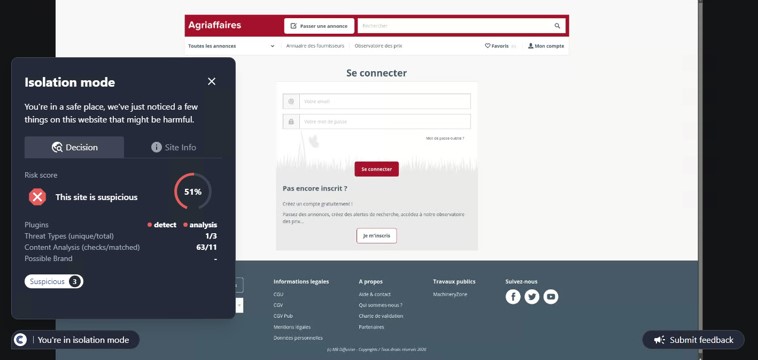
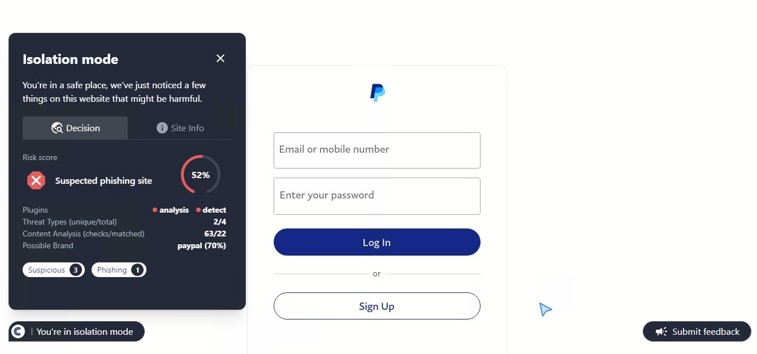
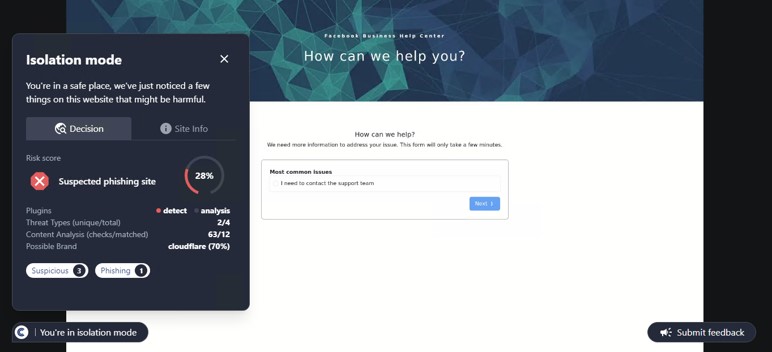
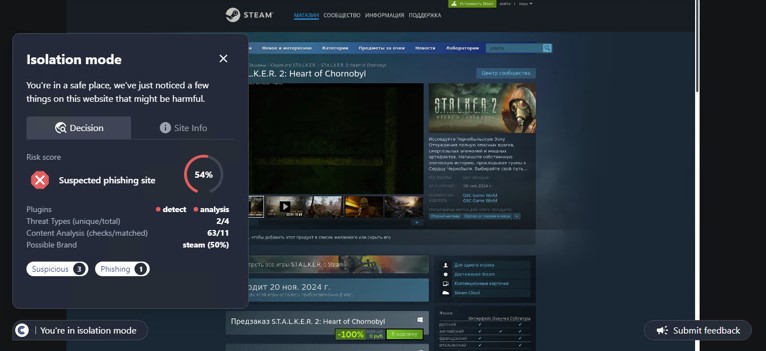
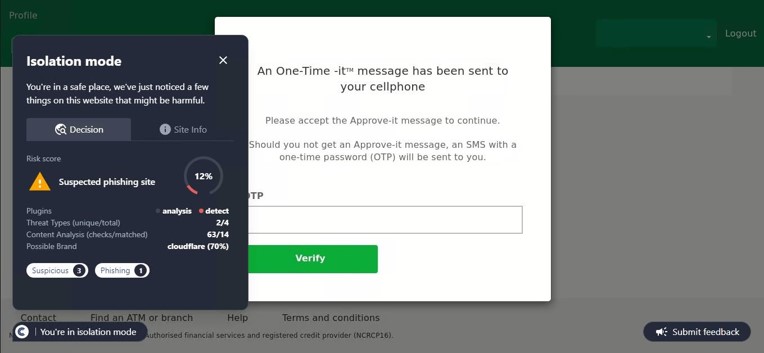
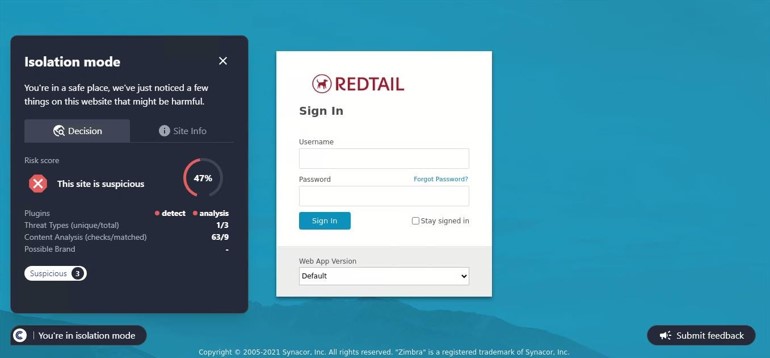
This site was detected by ConcealBrowse on October 11th, a few months after initial flags by security vendors. There are eighteen vendors flagging the page due to malicious activity and phishing. ConcealBrowse intervened with a 30% risk score, citing a possible brand impersonation and phishing attempt.
Instead of immediately asking for a password, this phishing page initially requests only the email address of the potential victim. This information is often used to verify that only the intended target can access the final phishing page as a way to evade detection by security vendors. In this case, the email is used to customize the final login page, making it appear more realistic. ConcealBrowse’s intervention blocks all keyboard input, making it impossible for a user to enter their email address or interact with the fraudulent login.
_____________
Valuable Outcomes
As this recent threat reports exemplify, ConcealBrowse offers comprehensive protection against many sophisticated cyber threats. Our advanced threat detection capabilities have successfully flagged and quarantined malicious web pages, preventing users from falling victim to various cyber-attacks. Conceal remains dedicated to upholding the integrity of online interactions, constantly refining our detection algorithms and threat identification protocols to ensure proactive protection against emerging cyber threats. By integrating cutting-edge technology and a robust security infrastructure, we empower users to confidently navigate the digital landscape, knowing that their online activities are shielded from potential harm.
Join the Conceal Community and claim your FREE ConcealBrowse licenses!
Join the Conceal Community today and fortify your online security for free! Don’t miss the chance to benefit from our advanced threat protection and stay one step ahead of cybercriminals. Experience peace of mind while browsing the internet, knowing that ConcealBrowse is your shield against the ever-evolving threat landscape. Take the proactive step towards a safer online experience – get your free ConcealBrowse license now and join a community committed to safeguarding your digital world.