Browser-Based Threat Report: Dec. 18
Browser-Based Threat Report
Week of December 18th, 2023
ConcealBrowse is leveraged by teams across the world to combat weaponized URLs and Browser-Based Threats. The technology is constantly analyzing suspicious web artifacts to identify risks in the form of drive-by attacks, phishing portals, and other threats that materialize while browsing.
At Conceal, your digital safety is our utmost priority. Our weekly threat report for the week of December 18th, 2023, unveils critical insights into the ever-evolving landscape of online threats.
The following report highlights recently detected sites that were deemed suspicious:
_____________
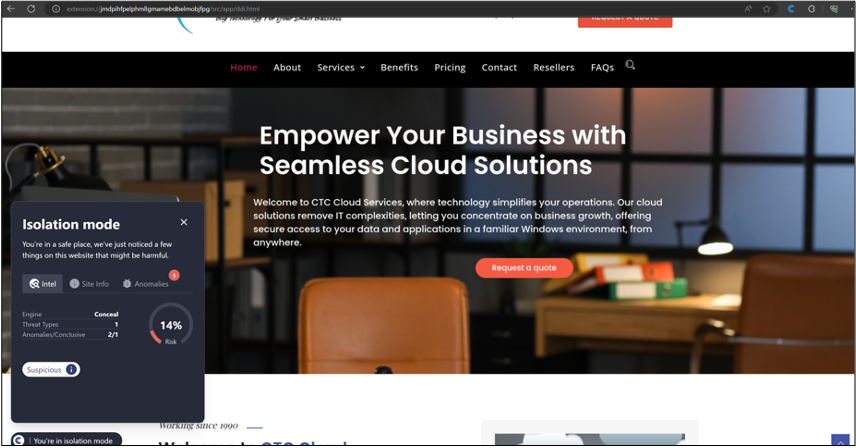
SHA-256: c3c3f907fd925366cc657147828696deaf0494bff7d5d9b39d62bb6b5e4e5cf2

This URL was detected by ConcealBrowse on December 15th, 2023, and assigned a 14% risk score due to suspicion. The URL was first classified by 2 security vendors in September of 2019 as malicious and phishing. This URL has a long history of delivering a compromised and suspicious page and to date has been annotated by 5 vendors as such.
Upon further investigation, there are multiple reasons why this site is continuously flagged. First, the site itself is a WordPress site, which without proper configuration, has numerous vulnerabilities by default, from compromised themes to insecure plugin integrations. That aside, the page is also delivered from an IP address that has historically delivered Trojans (most recently on December 12th) as well as Potentially unwanted Programs (PuPs) and Potentially unwanted Applications (PuAs). This exemplifies the dangers of shared hosting which could lead to the demise of the webpage in question, and further, the endpoints connecting to it.
_____________
SHA-256: 29ee53339a87040fd5b852e2d8542e9498812fb3fd689c25a4b3b4cf492220ce
This URL was detected by ConcealBrowse on December 14th, 2023. The URL in question was first identified December 13th, 2023 as delivering malware and a phishing webpage by 4 security vendors. 6 additional security vendors have since deemed the page as dangerous, totaling 10 vendors to date.
Spoofed websites, like the one delivered by the URL in question, are popular during this time of the year as the adversaries know there will be increased visitors. This site replicates the USPS homepage and even subpages. After a few minutes on the page, it is obviously spoofed with broken links. Conceal’s Sherpa AI engine detected multiple anomalies, identifying this site as malicious. The spoofed site was isolated with ConcealBrowse due to its intention of collecting credit card information from the unassuming, allowing users to add items such as stamps to their cart and proceed to a checkout screen.

_____________
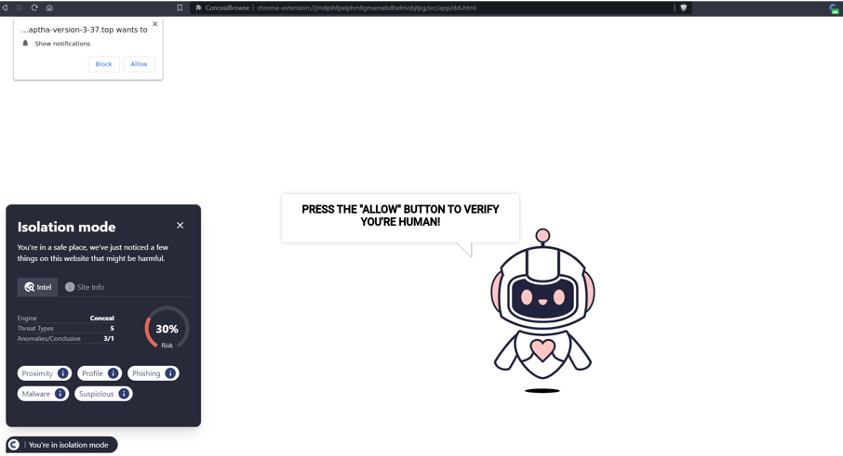
SHA-256: 60d387d2967c2e63a962333387768228a9d2b379829ebc3670ae6d4788f052e0
SHA-256: f248e02fe1c54a766640b8f2257b18d2f496a8642bac1b03ec52e26e2fbc6e93
The URL was detected by ConcealBrowse first on November 4th, and subsequently on December 14th, 2023. It was first submitted to various CTI feeds January 15th, 2022, with its final URL just recently submitted December 19th, 2023. The original URL and final URL have been classified as malicious and phishing by 5 total security vendors. This highlights the domain’s ability to continuously circumvent traditional security mechanisms.
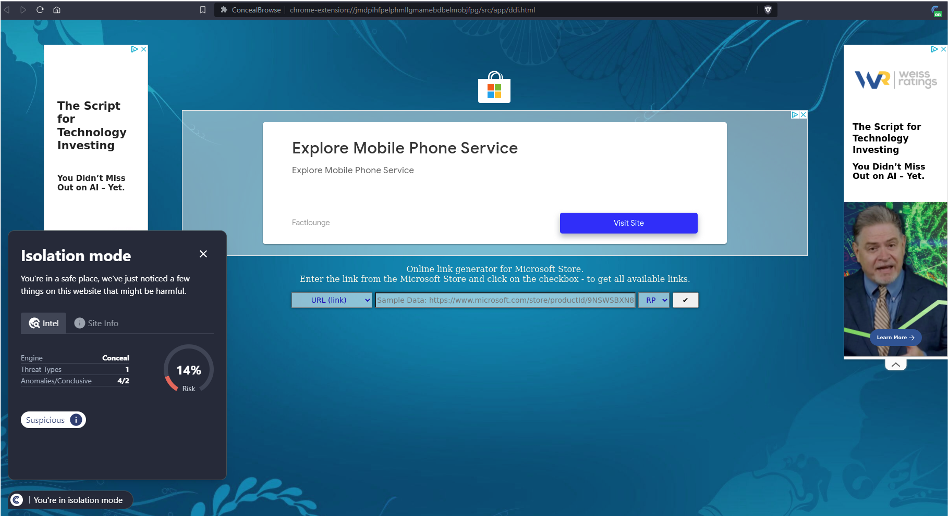
The URL above has multiple final URL’s that have been used in malvertisement campaigns historically. As seen below, once a user clicks on the malicious advertisement, their browser displays warning messages, stating they have outdated drivers. This tactic is used to scare end users into downloading malicious drivers to their endpoint. Although the URL today leads to a parked domain, meaning the adversaries are no longer using their website, they could easily commence this attack even though the domain is on a few DNS blocklists. They would be successful against those without informed DNS providers, however, would not be successful against those with ConcealBrowse.

_____________
Valuable Outcomes
ConcealBrowse offers comprehensive protection against many sophisticated cyber threats, as recent threat reports exemplify. Our advanced threat detection capabilities have successfully flagged and quarantined malicious web pages, preventing users from falling victim to various cyber-attacks. Conceal remains dedicated to upholding the integrity of online interactions, constantly refining our detection algorithms and threat identification protocols to ensure proactive protection against emerging cyber threats. By integrating cutting-edge technology and a robust security infrastructure, we empower users to navigate the digital landscape with confidence, knowing that their online activities are shielded from potential harm.
Join the Conceal Community and claim your FREE ConcealBrowse licenses!
Join the Conceal Community today and fortify your online security for free! Don’t miss the chance to benefit from our advanced threat protection and stay one step ahead of cybercriminals. Experience peace of mind while browsing the internet, knowing that ConcealBrowse is your shield against the ever-evolving threat landscape. Take the proactive step towards a safer online experience – get your free ConcealBrowse license now and join a community committed to safeguarding your digital world.
Sign up for the Conceal Community and claim your free licenses by completing the form below.