Browser-Based Threat Report: Feb 26
Browser-Based Threat Report
Week of February 26th, 2024
ConcealBrowse is leveraged by teams across the world to combat weaponized URLs. The technology is constantly analyzing suspicious web artifacts to identify risks in the form of drive-by attacks, phishing portals, and other threats that materialize while browsing.
At Conceal, your digital safety is our utmost priority. Our weekly threat report for the week of February 26th, 2024, unveils critical insights into the ever-evolving landscape of online threats.
The following report highlights recently detected sites that were deemed suspicious:
_____________
SHA-256: 0a76274e99e285c9d7e18d094e71ea6fca1b0274e30c28492a24218e53c61cb3
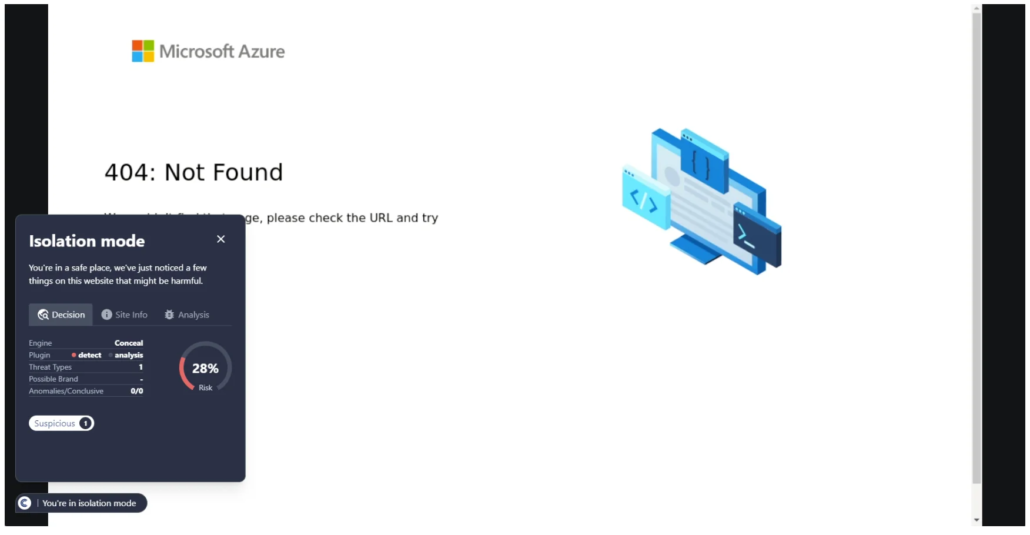
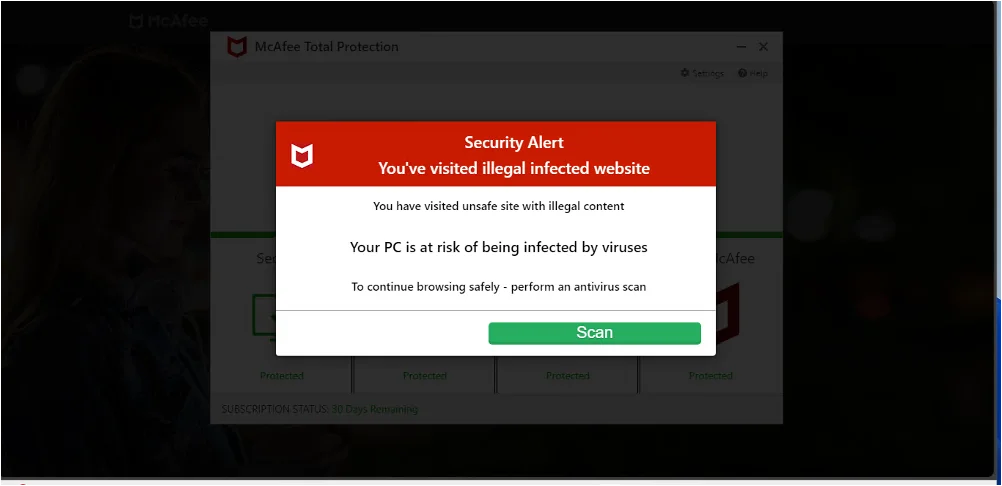
Screenshot of page where Microsoft tech support scam was found
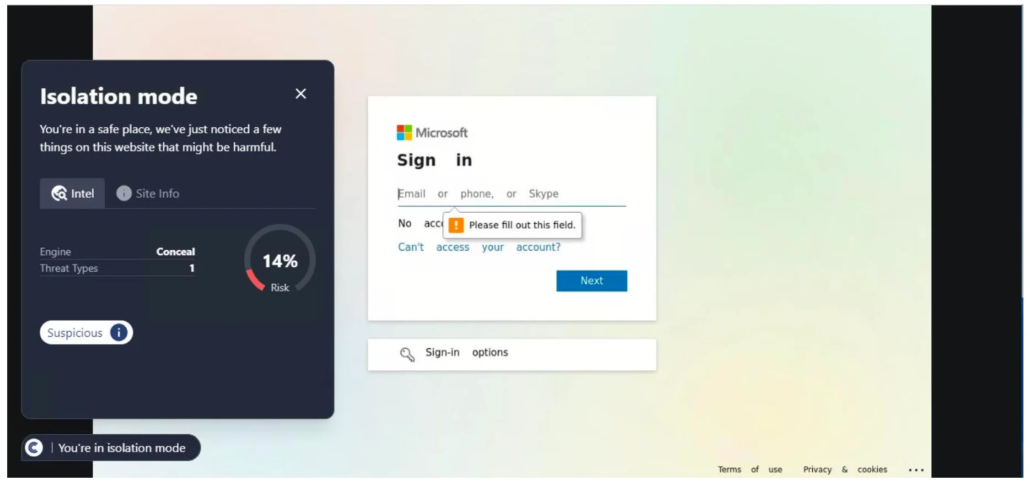
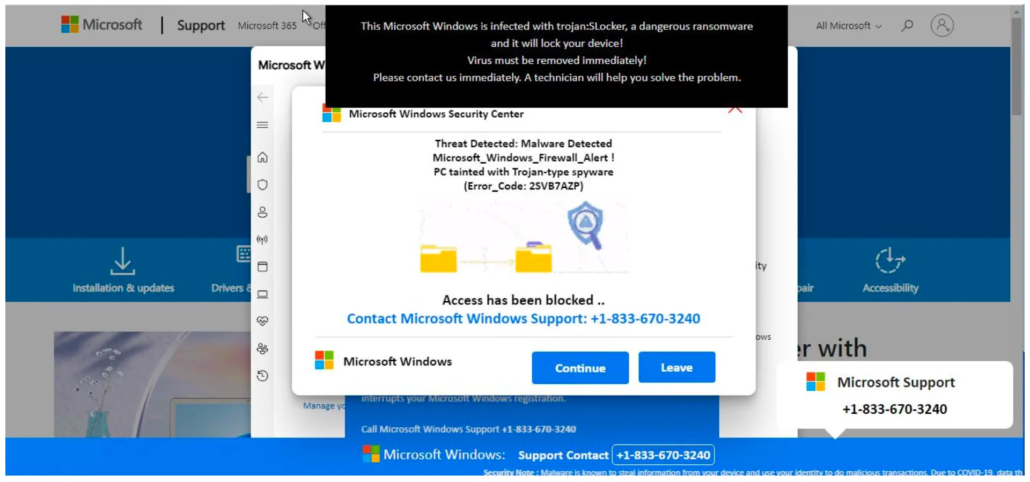
This URL was first detected by ConcealBrowse on February 21st; the same day other security vendors started reporting on it. Initially, only five security vendors marked the page as malicious, but currently there are 15 vendors flagging the page. ConcealBrowse successfully intervened with a 28% risk assessment due to suspicious activity.
When ConcealBrowse first intervened, this page was a Microsoft tech support scam. Malicious actors utilize Azure’s web application services to create Microsoft-branded pages that appear trustworthy. Although the page has since been removed from Microsoft, ConcealBrowse caught the malicious behavior prior to Microsoft intervening. Users are protected in real-time even before the owners of the domain can respond to reports of platform abuse.
Conceal Recommendation: Sites like these can be tricky to detect early, due to their trusted domain names and IP addresses to evade filtering technologies. Live analysis through ConcealBrowse is the best way to protect users in these scenarios.
_____________
SHA-256: 174a9247c762be452a13f29ab15c2648577ffe8b9f6245dbc23abe6fe8171034
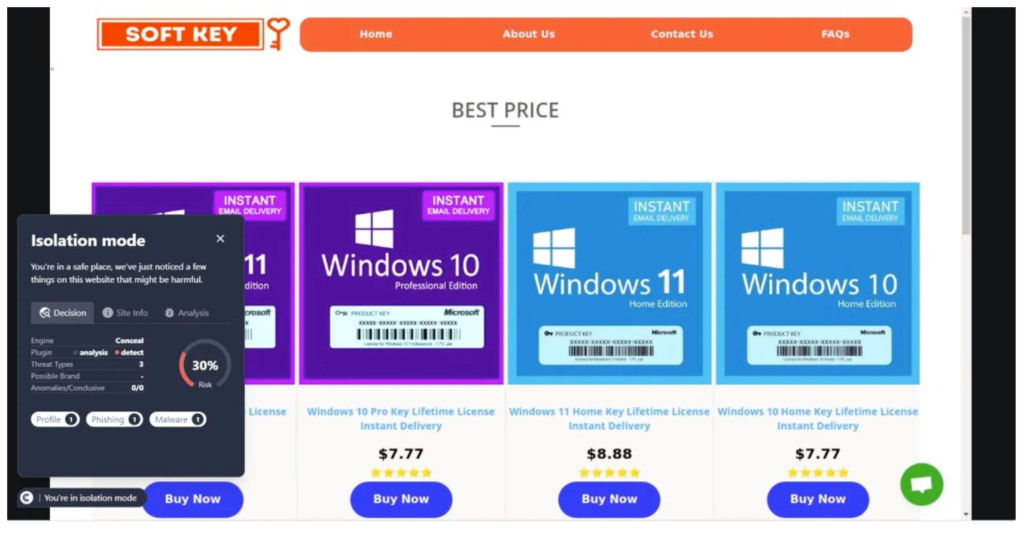
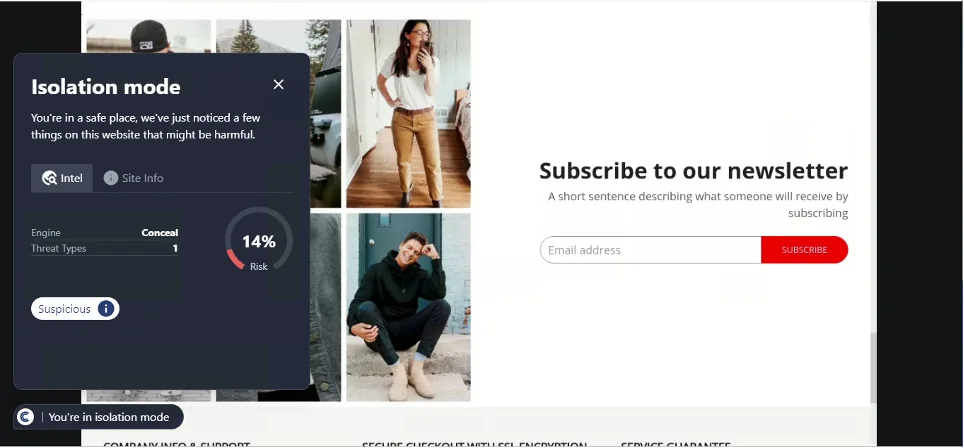
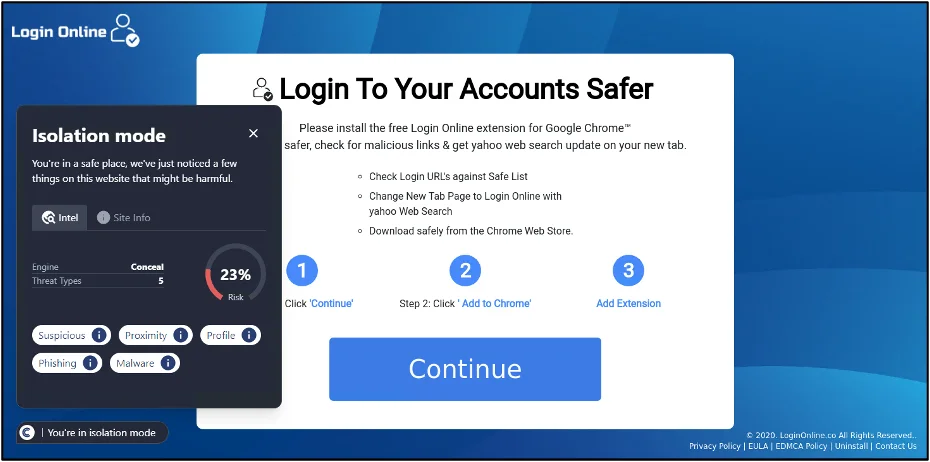
screenshot of an illegitimate keygen site
This URL was first detected by ConcealBrowse on February 23rd and is not yet reported by any other security vendors. The page was given a 30% risk assessment, with ConcealBrowse citing possible phishing and malware.
This webpage has multiple indicators of selling an illegitimate product. Although this site may give the user a valid product key for Windows products, these keys are usually procured illegitimately and can be revoked at any point. Therefore, it is not safe to purchase keys from sites such as these, as doing so may cause interruptions in business flow and result in financial loss for the user.
Conceal Recommendation: This site should be considered an emerging threat and has not existed long enough for other security vendors to do a full analysis and publish their findings. Real-time analysis through ConcealBrowse detects novel techniques used by adversaries in order to disrupt these threats.
_____________
SHA-256: 69b441c662289adb832efcf1379f7841923b5f27d428c1bee4f11deef55b559c
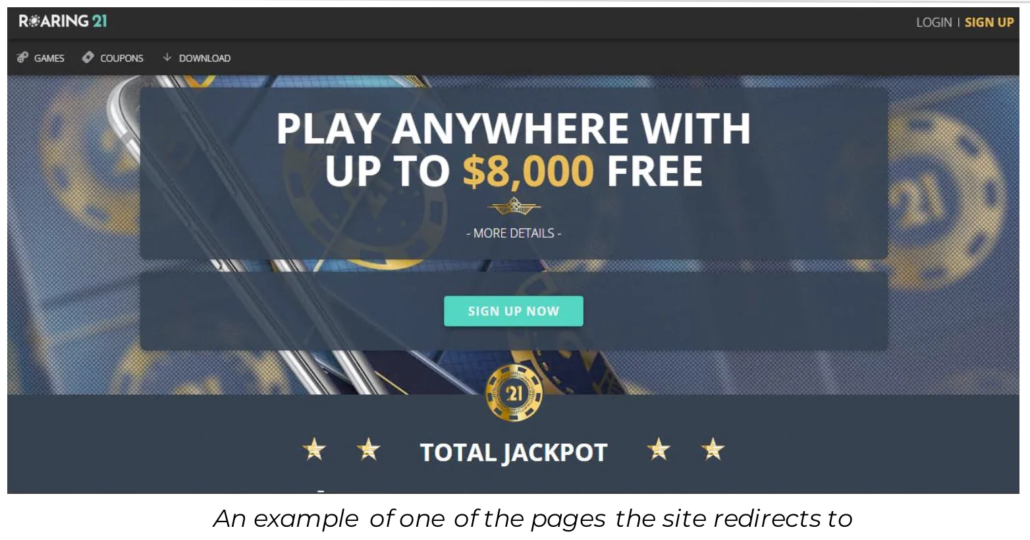
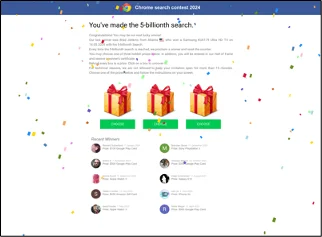
Screenshot of prize scam site
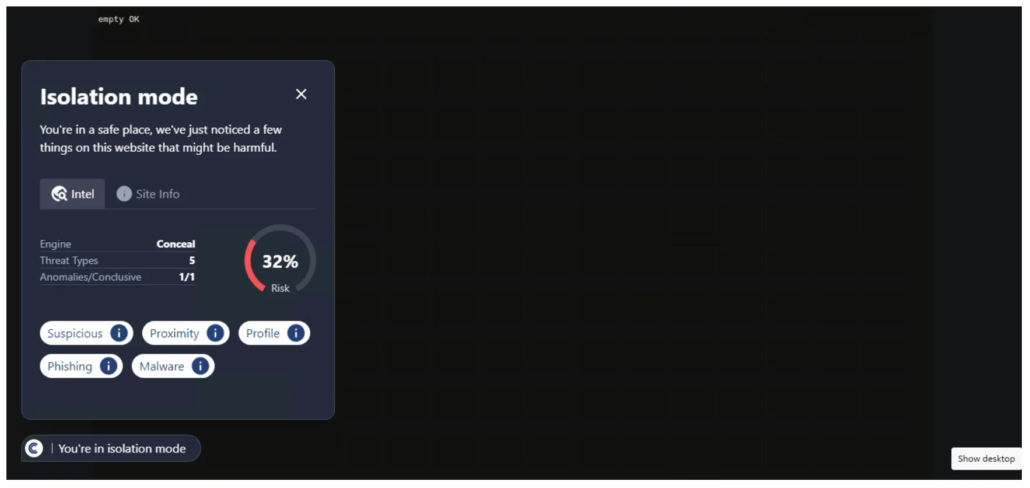
This URL was first detected by ConcealBrowse on February 20th. 10 security vendors flagged the page on that same date, with currently 9 reporting the page for spyware and phishing activity. ConcealBrowse successfully intervened, giving the page a 28% risk score and blocking the page from user access.
This website redirects to multiple different pages, most of which are involved in prize scams. Prize scams tell the victim that they have won, or have the potential to win, a large amount of money. The page asks for personal information such as their phone number and email address. This information can then be used to steal more information or create more personalized attacks. Due to the level of malicious activity detected, ConcealBrowse intervened to block the page rather than put it into isolation, preventing users from entering their information or viewing the site.
Conceal Recommendation: Balance out your defense-in-depth strategy to proactively detect suspicious web pages with technologies like ConcealBrowse that provide real-time analysis.
_____________
Valuable Outcomes
As this recent threat reports exemplify, ConcealBrowse offers comprehensive protection against many sophisticated cyber threats. Our advanced threat detection capabilities have successfully flagged and quarantined malicious web pages, preventing users from falling victim to various cyber-attacks. Conceal remains dedicated to upholding the integrity of online interactions, constantly refining our detection algorithms and threat identification protocols to ensure proactive protection against emerging cyber threats. By integrating cutting-edge technology and a robust security infrastructure, we empower users to confidently navigate the digital landscape, knowing that their online activities are shielded from potential harm.
Join the Conceal Community and claim your FREE ConcealBrowse licenses!
Join the Conceal Community today and fortify your online security for free! Don’t miss the chance to benefit from our advanced threat protection and stay one step ahead of cybercriminals. Experience peace of mind while browsing the internet, knowing that ConcealBrowse is your shield against the ever-evolving threat landscape. Take the proactive step towards a safer online experience – get your free ConcealBrowse license now and join a community committed to safeguarding your digital world.
Sign up for the Conceal Community and claim your free licenses by completing the form below.