Use Case: How Conceal Stopped a Compromised Email Luring Our Team with an Urgent RFP Deadline
Overview
ConcealBrowse effectively neutralized a sophisticated phishing attack initiated through a compromised partner’s email by detecting and preventing credential theft disguised as an RFP request.
Background
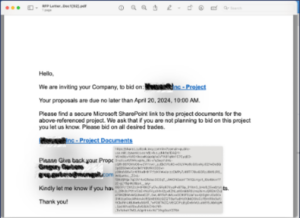
In a recent security incident, ConcealBrowse successfully thwarted a sophisticated phishing attack that began with the compromise of a partner’s email account. The attackers sent a highly convincing and well-crafted email to our sales team, targeting their interest in responding to an RFP.
The Initial Email
The email passed grammatical checks flawlessly, enhancing its perceived legitimacy. Since the email came from a legitimate contact, it was not flagged as potentially malicious.
To further build trust, the email’s attachment looked legitimate and offered a link to what looked like a legitimate OneDrive link, purportedly sharing relevant documents.
Further Trust Built
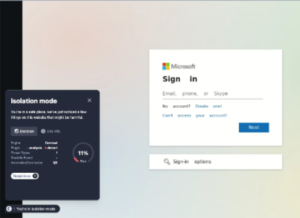
A mimicked standard Cloudflare CAPTCHA verification page allayed any doubts that the link or email could have been compromised or illegitimate.
The ConcealBrowse Detection
The included OneDrive link cleverly bypassed typical suspicion thanks to its commonplace nature in business communications.
However, thanks to ConcealBrowse’s robust phishing detection capabilities, the malicious intent was identified and neutralized before any damage could occur, showcasing the effectiveness of our cybersecurity measures in protecting sensitive information.
The Conceal Advantage
The successful interception of a sophisticated phishing attempt by ConcealBrowse highlights its vital role in modern cybersecurity. As threats grow more cunning, ConcealBrowse’s advanced detection capabilities are essential for protecting sensitive information and ensuring business integrity, proving that robust cybersecurity investment is not just beneficial, but necessary.