Browser-Based Threat Report: ConcealBrowse Thwarts Sophisticated Spear Phishing Attack Targeting Conceal CEO
ConcealBrowse’s Advanced Protection Overcomes Traditional Anti-Phishing Tool Limitations
In a recent spear phishing attack, cybercriminals targeted Conceal’s CEO, Gordon Lawson, bypassing Microsoft 365’s strict anti-phishing protection. This was a highly-targeted attack utilizing advanced techniques to evade detection, but ConcealBrowse effectively protected against the threat by analyzing metadata about the URL used in the attack even though it wasn’t flagged as malicious in traditional intelligence sources.
Bypassing Anti-Phishing Protections
The attackers utilized several techniques intended to defeat common anti-phishing protections:
1. The phishing email contained a screenshot of a typical Microsoft sharing screen linked to an obfuscated URL, operated by a legitimate company, Constant Contact, with a strong reputation.
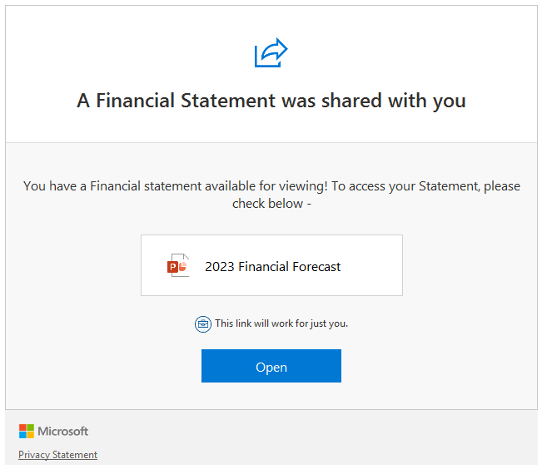
2. The email body contained significant whitespace followed by seemingly legitimate content, which helped it defeat the email-based phishing detection algorithms.
3. The threat actor passed encoded metadata and a URL through a redirect page, which behaved differently on the first visit vs. Subsequent ones. In some cases after the first visit, the victim would be redirected a legitimate Microsoft login page. To defeat sandboxing and similar protections, a captcha was used on the first visit. These steps were aimed at reducing the chances of the malicious site being detected and flagged by automated analytical tools.
Targeted Attack Characteristics
Several indicators suggest this was a targeted attack:
- Compromised sender account: The sender’s reputation, as determined by DKIM, SPF, and Composite authentication, was associated with Microsoft. However, the display name and recipient address raised suspicions, implying the attack originated from a compromised email account.
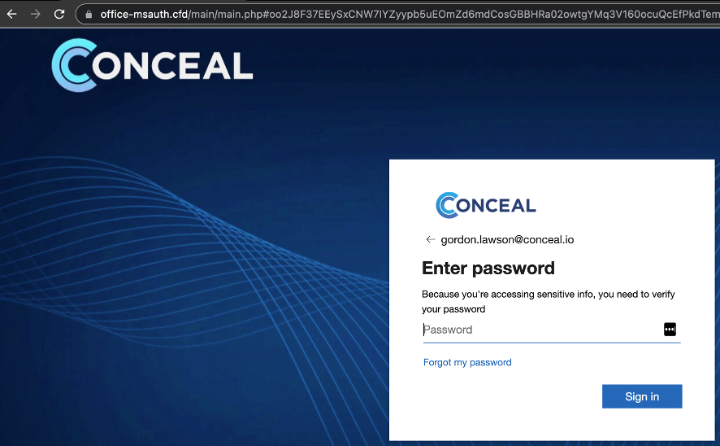
- Customized login page: The phishing email redirected users to a convincing Microsoft login prompt that included the Conceal logo and almost exactly mimicked the real Microsoft authorization page.
ConcealBrowse’s Protection Against the Attack
ConcealBrowse’s advanced security measures effectively protected against the spear phishing attack by focusing on metadata analysis of the URL used in the attack. Even though traditional intelligence sources had not flagged the URL as malicious, ConcealBrowse identified potential risks based on the following indicators:
Domain registration: The recently registered domain prompted ConcealBrowse to isolate the session to protect users. This proactive approach ensured that any potential threats associated with the domain were contained, keeping the business secure.
Multi-layered defense: ConcealBrowse employed multiple data sources and indicators to provide robust protection against the attack, demonstrating the importance of a comprehensive approach to cybersecurity.
Indicators of Compromise:
The following indicators were observed as part of this campaign:
| TYPE | INDICATOR | NOTES |
| DOMAIN | https://office-msauth.cfd/ | Mimicked a Microsoft authentication page, customized with the Conceal logo. |
| IPV4 | 209.141.52.236 |
Conclusion
The sophisticated and targeted spear phishing attack exemplifies the evolving tactics of cybercriminals and the limitations of traditional anti-phishing tools. ConcealBrowse’s advanced protection, based on metadata analysis and multi-layered defense, effectively thwarted the attack. The fact that attackers are constantly evolving to defeat the latest defensive techniques emphasizes the need for businesses to adopt innovative security measures to safeguard sensitive information and maintain a secure environment. Click here to schedule a demo of ConcealBrowse today.




