Conceal Threat Alert: Phishing Attack Bypasses Traditional Controls, ConcealBrowse to the Rescue
Threat actors can be downright crafty, and motivated actors tend to take their attacks to the next level. So where does this leave employees who are targets of more sophisticated attacks? Many times, they are left to their intuition and, if they are lucky, any skills they have acquired through traditional awareness training. In other words, the security of the user, their device, and the organization are reliant on recalling information from their last awareness training session. Despite increased spend on baseline cyber security tools such as email gateways, web gateways, EDR solutions and awareness training, we continue to see an increase in successful attacks such as credential theft (phishing attacks that politely ask users for their login credentials) and ransomware. By utilizing ConcealBrowse, we illustrate how a credential phishing attack that bypassed traditional security controls was successfully prevented.
Anatomy of the Attack
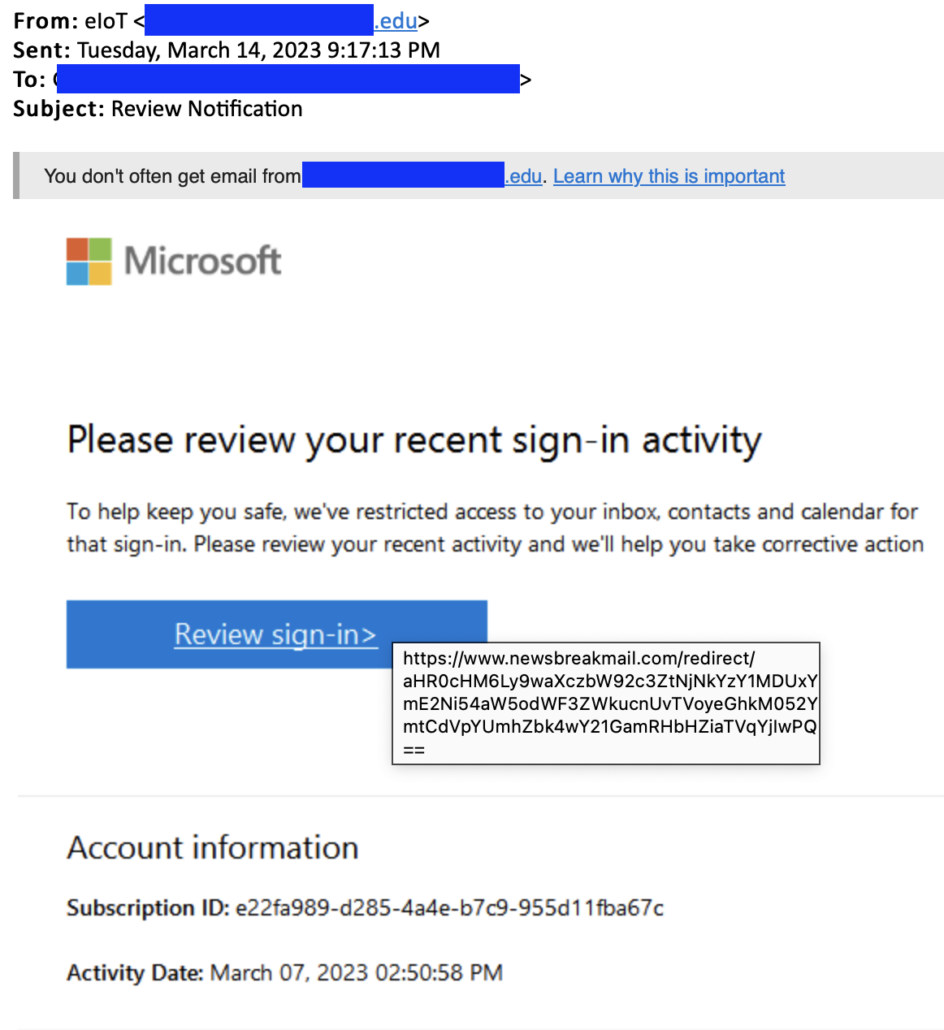
The email above was sent from a legitimate and most likely compromised email address. By sending from a real email account, the attackers evade common baseline checks such as SPF, DMARC and IP spoofing checks. Next up, they worked on the message content, including legitimate Microsoft message content, images and prompts; this part of their attack helped evade technical content controls as well as build trust with the recipient. In addition to the realistic content, the attackers also added some conversational banter at the bottom of the email (well past where normal humans would scroll!), which appears geared to improve deliverability. The rest of their tactics continue to circumvent both human and technical detection by presenting authentic-looking URLs to websites that have been recently compromised and then ultimately using the compromised first hop to redirect the user to the credential theft site, which was hosted on a recently acquired domain.
This example highlights a few of the techniques attackers use daily to evade existing controls and dupe users into action. A recent report from security firm Cofense identified that 67% of emails reported by users led to credential theft webpages. Additionally, they found that 52% of credential theft emails abuse the Microsoft brand and that 70% of reported credential theft emails bypassed secure email gateways. With these staggering statistics, it is clear that even with best-in-class controls, employees are at a stark disadvantage to the well-funded adversaries whose mission is to gain access to their credentials to advance their nefarious activities further.
Anatomy of the Prevention
When the user clicked the link in the convincing and delivered email, ConcealBrowse was poised and ready to jump into action. As a browser extension, ConcealBrowse analyzed the URL and determined that some attributes of the page had unknown risk profiles and others displayed risk indicators, but overall, the page was not yet known to be malicious. This is a perfect example of the nature of current web-based threats that crop up and disappear in a moving window of inherent risk that is simply not apparent to users and existing technical controls.
Once ConcealBrowse determined that it didn’t have a clear security posture verdict for the URL at that point in time, it seamlessly moved the webpage into isolation, instantly protecting the user from potential risk and allowing the page to be loaded and interacted with. At this stage, ConcealBrowse was able to apply secondary security posture checks which identified a user authentication (login) form, which, in turn, triggered Conceal’s Credential Guard to evaluate the page for signs of credential theft. Using AI modeling, ConcealBrowse was able to inspect the technical and visual attributes of the webpage to determine that it was a phishing webpage. At this point, ConcealBrowse protected the user session by preventing the end-user from entering data into the form and visually alerted that the page was attempting to steal their login information.
The Result
Typically, these attacks don’t end so well, and organizations spend time and money cleaning up after the incident. In this case, the user was protected by ConcealBrowse therefore, there was no incident. Instead, their security team inherited real-time telemetry about a credential theft website. Using Conceal’s integration framework, the customer was able to stream the telemetry into their SIEM and automatically update other controls to take advantage of this new information.
Regardless of how trustworthy your users think a link might be, ConcealBrowse scans every URL using state-of-the-art techniques and applies our proprietary threat identification model and computer vision to identify and block phishing attempts and malware downloads.
You can experience the power of our Zero-Trust at the Edge security model today by requesting a free ConcealBrowse trial or by scheduling a demo with our team of experienced security professionals.
Written By: Conceal Research Team





