Browser-Based Threat Alert: SVB Opportunistic Phishing Attacks
As all security professionals know, phishing attacks are a constant threat.
Cybercriminals are relentless in their efforts to deceive individuals into revealing sensitive information, and the consequences can be devastating. March 2023 witnessed a prime example of how a crisis can create a ripe environment for phishing campaigns to thrive. The collapse of Silicon Valley Bank (SVB) and the subsequent phishing attacks targeting its customers offer a cautionary tale and highlight the importance of zero-trust protection measures.
SVB, a major U.S. bank known for providing financial services to some of the largest tech investors and startups, collapsed on March 10, 2023. Federal regulators under the control of the Federal Deposit Insurance Corporation (FDIC) took over the bank after depositors rushed to withdraw billions of dollars in deposits. The financial crisis garnered worldwide attention and created an atmosphere of chaos and stress that cyber criminals naturally sought to exploit. Amid the bank’s collapse, a series of phishing campaigns impersonating SVB began to emerge. A recent article on Cybersecurity Magazine conducted an analysis of SVB-related phishing attacks and noted that the ongoing banking crisis is likely to provide more opportunities for attackers as more banks become stressed and fail.
In the context of online financial services, phishing attacks can involve fake login pages or emails that impersonate legitimate financial institutions. Unsuspecting victims may provide sensitive information, such as login credentials or financial data, to these fake websites. This information can then be used for criminal activities like identity theft or financial fraud. In fact, the credentials themselves can have tremendous value on the open market, with verified admin accounts in some cases being sold for up to $120,000. In some cases, victims are redirected to the real site, giving them the impression that they are interacting with the legitimate institution while providing their credentials to attackers.
Attackers in the SVB phishing campaign created domains that closely resembled SVB’s name, often containing minor variations and financial terms to lure individuals into clicking on malicious links. More than 90 new domains were registered for use in attacks against targets, mainly in the U.S. The report identified one Turkish attacker that began utilizing a fraudulent domain within a few hours of its registration.
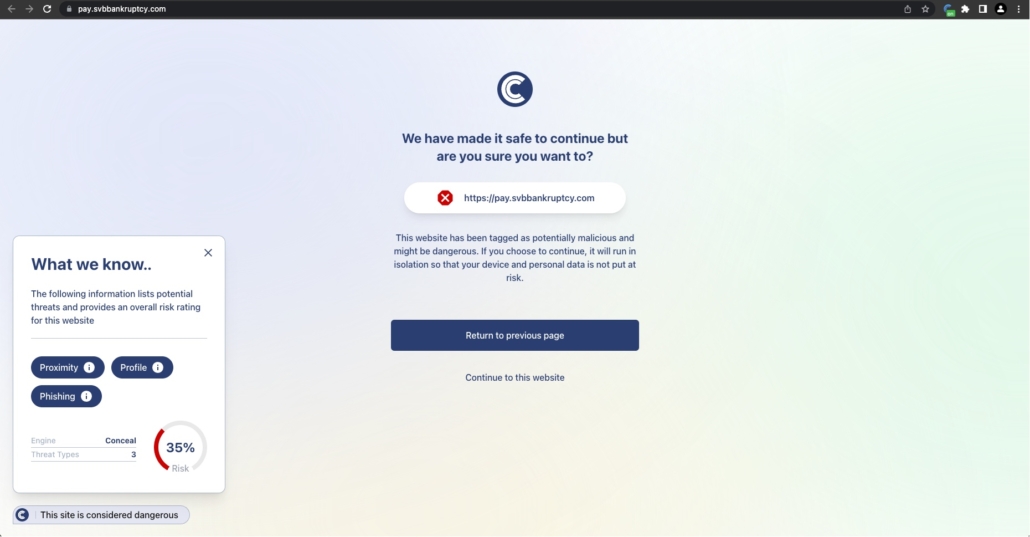
The aftermath of the SVB collapse and the ensuing phishing attacks underscore the necessity of proactive cybersecurity measures. In times of crisis, hackers often prey on fear and confusion, making it essential for individuals to remain vigilant. However, even with extreme vigilance and thorough cyber security training, crises like the SVB collapse can impair user’s judgment about messages related to the event. That is why it’s critical to remove the burden of judging risk from the user and put it in the hands of objective security tools like ConcealBrowse.
The browser-based phishing protection provided by ConcealBrowse is an indispensable tool in mitigating the risks of phishing attacks and safeguarding valuable information when end users don’t know who they can trust. The SVB phishing campaign serves as a reminder of the ever-present threat of phishing and the need for robust security measures. By utilizing tools like ConcealBrowse and staying informed about the latest cybersecurity threats, individuals and organizations can better protect themselves from falling victim to cybercriminals’ deceptive tactics.
Click here to schedule a demo of ConcealBrowse today and see how it can keep your users safe from opportunistic attacks like these.
Written By: Conceal Research Team




