Don’t Blame the User for Clicking on Links
It’s not the user’s job to provide phishing protection for your company
Finally, we have a blog from a reputable source (the UK’s NCSC) stating the true facts about users clicking on links.
“Users frequently need to click on links from unfamiliar domains to do their job and being able to spot a phish is not their job.” That is so true.
No matter how much cyber awareness training we have had or how regular it’s reinforced, most of us are time pressed, caught unawares and will click on something that merits a further look. Even the links that are scrutinised to the nth degree can hide something malicious. The best browser security solutions recognize this fact.
See below – Can you tell me which is the malicious one? Hovering over the links – both look like they point to the Computer Associates site. But clicking on the wrong one will place you at risk of being infected.
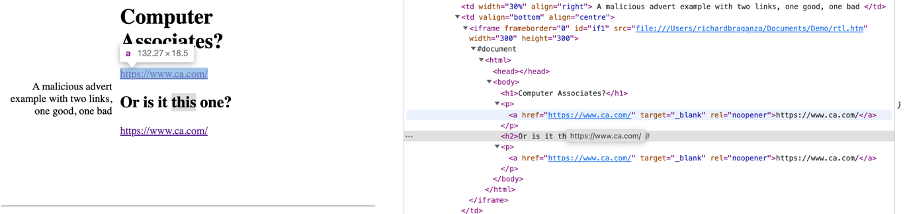
Spoiler alert: It’s the first one. Even on hover over it looks like it will take you to the genuine site. It won’t and that’s because the destination domain name’s characters are not ASCII and are Cyrillic. Humans would be hard pressed to tell them apart. The browser knows they are not the same domain and hence will take you where you did not intend to go. Good luck trying to avoid that.
Though not entirely obvious from the NCSC’s blog post, it is worth mentioning those malicious links crop up not just in emails, they can be shared over Linkedin, Slack, social media, adverts hosted on highly popular content. All the places targets are likely to access to do their jobs.
Remember for an attack to work, as pointed out in NCSC’s blog, they only need one person to click on the link in whatever form it took: Office365, Zendesk, Slack, Salesforce etc. Whatever applications your staff need to work with, the links they access can harbour a huge risk to your company.
How does ConcealBrowse take over the responsibility for phishing security?
We at Conceal looked at this problem and produced a novel solution: ConcealBrowse. It’s a browser extension that converts your browser into a secure browser. We made the same assumption as the NCSC at the outset of formulating our solution, that users will follow their noses and click to follow content as they need to, not always mindful of where that may take them.
ConcealBrowse takes away the implicit trust and makes the decision to isolate anything being accessed via any application that is known bad or unknown. For example, short links, QR codes and IP addresses which reveal nothing about where they will eventually take you. Misspelled domain names like shown above or subdomains of more trusted domains
Why does it protect you when you are using other applications like Slack, etc.? Quite simply these applications will connect the user to the Internet using the default browser. The ConcealBrowse extension is engaged. When opened with our dynamic remote browser isolation, the user can still work with the web site. The users simply see a rendering of the website as if the web page had opened locally. It has not. It has been opened in the cloud, air-gapped from the user.
Entering credentials into phishing pages and attempting to download malicious files are blocked and thus the risk from users having to access content has been managed. To be honest, most web pages that users visit have no need to be isolated – so they are not. ConcealBrowse makes the decision as to whether to isolate based on its gathered intelligence and threat intelligence feeds you may have access to. Because of this, 99% of web pages are not isolated. The experience to the user is seamless. The ConcealBrowse solution is completely independent of any other security controls and works with all common operating systems and virtual desktop environments.
You, too, can enjoy the benefits of zero trust browser protection. Just click here to sign up for a free ConcealBrowse account.