Navigating the Cyber Seas with Conceal’s AI Engine: A Deep Dive into AI-Powered Browser Security
Following our exploration of the vital role of Artificial Intelligence (AI) in browser security strategies, it’s time to delve into a specific, cutting-edge solution: ConcealBrowse’s AI engine. In a world where cyber threats are increasing and becoming more sophisticated, ConcealBrowse stands as a beacon of innovation, demonstrating how AI integration in browser security is beneficial and essential.
SherpaAI: The Vanguard of AI-Driven Browser Security
ConcealBrowse exemplifies the practical application of AI in combating cyber threats. It’s not just a tool; it’s an intelligent ally in the continuous battle against cybercriminals.
The Rising Tide of Cyber Threats
In an era where digital threats are rampant, ConcealBrowse provides an answer to the increasing complexity and frequency of these threats. Traditional security systems, often reactive and rule-based, fall short against the dynamic nature of modern cyber threats. ConcealBrowse’s AI-driven approach is not just reactive but proactive, identifying and mitigating risks before they become crises.
Predictive Risk Mitigation
ConcealBrowse excels in predictive risk mitigation. By analyzing vast amounts of data, it identifies potential threats and behavioral anomalies, often alerting users before they even encounter the risk. This preemptive approach is crucial in a digital landscape where new threats emerge rapidly.
Dynamic Threat Response
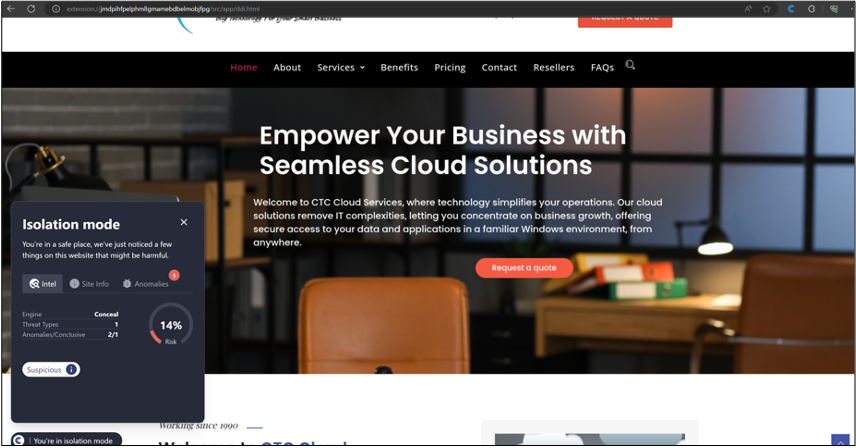
ConcealBrowse responds dynamically to threats, offering real-time protection. Its ability to analyze website behaviors and scripts instantaneously allows it to flag and isolate malicious activity effectively, ensuring users are protected at every moment of their online journey.
Enhanced Accuracy and Efficiency
One of ConcealBrowse’s standout features is its enhanced accuracy in threat detection, significantly reducing false positives. This precision strengthens security and enhances the user experience by minimizing disruptions and unnecessary isolations.
Real-World Applications: ConcealBrowse in Action
ConcealBrowse isn’t a theoretical solution; it’s a practical one. Imagine browsing online and unknowingly encountering a phishing link. With ConcealBrowse, this threat is identified and neutralized before you infect your system. Or, consider downloading a file that might be harmful. ConcealBrowse isolates and analyzes it in a secure environment, ensuring safety without hindering your workflow.
AI as a Necessity, Not a Luxury
The integration of AI into browser security, exemplified by ConcealBrowse, has transitioned from a luxury to a necessity. In the complex cyber landscape of today, the fusion of AI with traditional security measures is critical to staying ahead of threats.
Charting the Course with ConcealBrowse
As we navigate the challenging seas of cyber threats, ConcealBrowse stands as a crucial component of any robust cybersecurity strategy. It’s time for organizations and individuals to embrace ConcealBrowse as a tool and an essential ally in the ongoing battle against cyber threats. The future of browser security is here, and it’s powered by AI.