Don’t Blame the User for Clicking on Links
/in Blog /by Marissa PixlerIt’s not the user’s job to provide phishing protection for your company
Finally, we have a blog from a reputable source (the UK’s NCSC) stating the true facts about users clicking on links.
“Users frequently need to click on links from unfamiliar domains to do their job and being able to spot a phish is not their job.” That is so true.
No matter how much cyber awareness training we have had or how regular it’s reinforced, most of us are time pressed, caught unawares and will click on something that merits a further look. Even the links that are scrutinised to the nth degree can hide something malicious. The best browser security solutions recognize this fact.
See below – Can you tell me which is the malicious one? Hovering over the links – both look like they point to the Computer Associates site. But clicking on the wrong one will place you at risk of being infected.
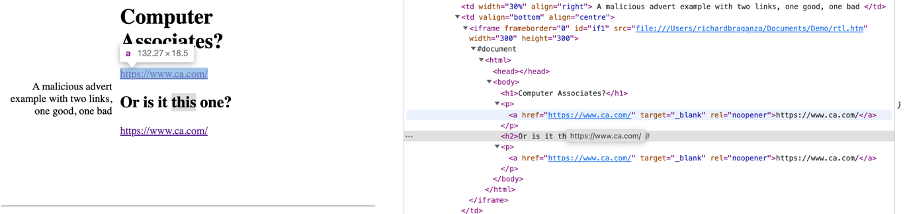
Spoiler alert: It’s the first one. Even on hover over it looks like it will take you to the genuine site. It won’t and that’s because the destination domain name’s characters are not ASCII and are Cyrillic. Humans would be hard pressed to tell them apart. The browser knows they are not the same domain and hence will take you where you did not intend to go. Good luck trying to avoid that.
Though not entirely obvious from the NCSC’s blog post, it is worth mentioning those malicious links crop up not just in emails, they can be shared over Linkedin, Slack, social media, adverts hosted on highly popular content. All the places targets are likely to access to do their jobs.
Remember for an attack to work, as pointed out in NCSC’s blog, they only need one person to click on the link in whatever form it took: Office365, Zendesk, Slack, Salesforce etc. Whatever applications your staff need to work with, the links they access can harbour a huge risk to your company.
How does ConcealBrowse take over the responsibility for phishing security?
We at Conceal looked at this problem and produced a novel solution: ConcealBrowse. It’s a browser extension that converts your browser into a secure browser. We made the same assumption as the NCSC at the outset of formulating our solution, that users will follow their noses and click to follow content as they need to, not always mindful of where that may take them.
ConcealBrowse takes away the implicit trust and makes the decision to isolate anything being accessed via any application that is known bad or unknown. For example, short links, QR codes and IP addresses which reveal nothing about where they will eventually take you. Misspelled domain names like shown above or subdomains of more trusted domains
Why does it protect you when you are using other applications like Slack, etc.? Quite simply these applications will connect the user to the Internet using the default browser. The ConcealBrowse extension is engaged. When opened with our dynamic remote browser isolation, the user can still work with the web site. The users simply see a rendering of the website as if the web page had opened locally. It has not. It has been opened in the cloud, air-gapped from the user.
Entering credentials into phishing pages and attempting to download malicious files are blocked and thus the risk from users having to access content has been managed. To be honest, most web pages that users visit have no need to be isolated – so they are not. ConcealBrowse makes the decision as to whether to isolate based on its gathered intelligence and threat intelligence feeds you may have access to. Because of this, 99% of web pages are not isolated. The experience to the user is seamless. The ConcealBrowse solution is completely independent of any other security controls and works with all common operating systems and virtual desktop environments.
You, too, can enjoy the benefits of zero trust browser protection. Just click here to sign up for a free ConcealBrowse account.
Conceal Threat Alert: Attackers Using Search Engine Ads to Beat Antiphishing Software.
/in Blog /by Marissa PixlerA recent FBI public service announcement highlights that cyber criminals are using search engine advertisement services to abuse users’ trust of brands to direct them to malicious sites that deliver ransomware and conduct credential theft. At the end of this post, we’ll explain how you can start protecting your company’s network from this threat by signing up for a free trial of our zero-trust dynamic remote browser isolation and antiphishing software, ConcealBrowse.
Falsely-branded ads as the lure
According to the announcement, attackers are creating ads using logos and similar domains of trusted brands to trick users into clicking on the ads and visiting the malicious sites. A similar technique is often used in phishing attacks utilizing email as the attack vector. Since many antiphishing services already exist to protect users inside their email clients, this tactic is designed to bypass any checks done on email entirely.
Because the ads look legitimate and are related to something the user is conducting a web search for, the user may be more likely to take the malicious action on the page they are visiting. For instance, if they received the ad by searching for a piece of software they want to download, and both the ad and the page they visit look legitimate, the likelihood the user will download the software is greater than it would be if they received an unsolicited email with the same link.
To make matters even more confusing, these ads target the same keywords as the legitimate site so these malicious ads can appear above legitimate results. This creates an extra layer of confusion for the end user and increases the likelihood they will click on the malicious link instead of the legitimate one.
How can companies protect themselves?
Most of the countermeasures suggested by the FBI revolve around educating users and asking them to take extra precautions whenever they click on ads. These suggestions aren’t enough. No matter how much training they have or how careful they think they’re being, users will always make the wrong decision at some point. ConcealBrowse provides zero trust protection against these threats, checking every link regardless of the source. ConcealBrowse makes sure untrusted sites are opened in our dynamic isolated web browsing environment where they can’t access your user’s devices or networks.
ConcealBrowse phishing protection provides an additional layer of security when sites try to mimic the logos or domains of real sites by identifying these threats with computer vision and AI and blocking them from users, even if the sites have never been seen before.
Try ConcealBrowse today
Sign up for a free trial of ConcealBrowse today and see for yourself how easy it is to protect your users from untrusted web sites and apps. If you’d like to talk to a member of our sales team and see a demo first, you can click here to do that too. We would love to show you how ConcealBrowse pushes zero-trust to the edge and protects your users where they are most vulnerable; in the browser.
Written by: Conceal Research Team
Conceal Threat Alert: New Malware Families
/in Blog /by Chad AndersonDarkReading recently summarized a Fortinet analysis of three new ransomware variants that were added to the exponentially growing list that pose a threat to businesses of all sizes. The report analyzed three new ransomware tools new in 2022: Vohuk, ScareCrow, and AESRT. While none of them introduced anything new or novel, they nevertheless contributed to the growing financial cost and reputational harm that is the hallmark of the ongoing ransomware plague.
The first, Vohuk, has primarily targeted users in Germany and India, according to Fortinet. The ransomware encrypts the user’s data and replaces their desktop background with a message pointing them to a readme.txt file. That file contains instructions for submitting a payment to unlock the data via an email message.
ScareCrow similarly encrypts user data and provides instructions in a readme file, but in this case, the contact link is via Telegram channels. This ransomware family targets users around the world, and appears to have similarities to – and substantial improvements on – the Conti ransomware that was reportedly leaked earlier this year.
The AESRT ransomware variant does essentially the same thing, but provides data-unlocking instructions via a popup menu. The similarity between each of these unrelated ransomware families is evidence that attackers have found a formula that works and is repeatable.
How can remote browser isolation and phishing protection protect your workforce?
This research doesn’t address the methods that are being used with these specific malware families, but does note that phishing is the most-used delivery vector for ransomware in general. We’ve discussed several social engineering techniques in previous Threat Alerts that are used to abuse users’ trust and get them to visit malicious sites. These types of attacks almost always take place in the browser. So, while browser-based protection isn’t a silver bullet to block every possible delivery vector, it does address the most common and the one that is best for social engineering attacks.
ConcealBrowse can play a key role in any company’s anti-ransomware security posture. With more and more of each employee’s work taking place in the browser, moving zero-trust principles to the edge of your network can have a massive impact on your organization’s overall security. While ConcealBrowse can play a key role on machines within your network, it also provides an easy-to-manage and affordable option to deploy to every member of your distributed workforce. Because ConcealBrowse works at the endpoint, it can protect your assets even from threats to devices connecting to your network and services remotely.
If you’re interested in finding out more about how ConcealBrowse can protect your organization from malware, click here to schedule a demo today.
Conceal Makes Browser Security Accessible to Organizations of Any Size
/in Press Releases /by Marissa PixlerRecently recognized as a proven Zero Trust solution, Conceal leads effort to secure web browsing through dynamic browser isolation
AUGUSTA, Ga.–(BUSINESS WIRE)–Conceal, the leader in protecting against web-based attacks, announced the release of their secure browser extension, ConcealBrowse, to the Google Chrome store. ConcealBrowse performs pre- and post-processing of code on a computer to protect against browser-borne attacks including RATs, Trojans, Worms, Ransomware, Browser Hijacking, and more.
“With the release of ConcealBrowse in the app store, we’re not only introducing the extension but are also increasing overall accessibility to our growing global MSP/MSSP partner community,” said Gordon Lawson, CEO of Conceal
“The proven success of our platform is enabling Conceal to embark on an aggressive global growth strategy,” said Gordon Lawson, CEO of Conceal. “With the release of ConcealBrowse in the app store, we’re not only introducing the extension, but are also increasing overall accessibility to our growing global MSP/MSSP partner community.”
ConcealBrowse leverages an intelligence engine that works at machine speed with near zero latency to dynamically and transparently pre-process and analyze code and move suspicious, unknown and risky code to a cloud-based isolation environment. This unique, patented approach ensures that malicious code or files never enter enterprise devices and cannot infiltrate the network. ConcealBrowse works with existing browsers and supports all popular operating systems. It integrates with Microsoft Azure Active Directory and Okta for single sign-on authentication.
For the security partner community, ConcealBrowse offers a tremendous opportunity to provide innovative solutions to their customers. ConcealBrowse is a simple, drop-in solution that can easily be added to existing security packages. It requires minimal configuration and provides advanced telemetry data that can be integrated with SIEMs and common analytical tools via integrations with Splunk and Elasticsearch. Telemetry can also be consumed in a multitude of applications via a Syslog plugin.
Visit conceal.io to learn more about this innovative solution, schedule a product demonstration or sign up for a Free Trial.
About Conceal
Conceal enables organizations to protect users from malware and ransomware at the edge. The Conceal Platform uses Zero Trust isolation technology to defend against sophisticated cyber threats. Conceal is used by organizations of all sizes globally to ensure their users and IT operations remain secure, anonymous and isolated from attacks. For more information, visit https://conceal.io/.
Contacts
Lacey Brazzell.
706-481-2642
lacey.brazzell@conceal.io
Browser-Based Threat Alert: Russian Campaign
/in Blog /by Chad AndersonLikely-Russian APT actors threaten Western governments
The Threat & Detection Research Team at Sekoia.io recently reported on a suspected Russian intrusion set that utilizes phishing campaigns to steal credentials of military and strategic research targets in mainly Western countries.
One of the most interesting characteristics of this attack was the method the attackers used to bypass traditional email-based anti-phishing tools. Instead of including the malicious link directly in the email, which likely would have been caught by most phishing protection solutions, the attackers attached a benign PDF file that included the malicious link inside. By not including any malicious code within the PDF itself, the attack further evades any endpoint protection that relies on file scanning.
This attacker also uses a devious social engineering trick – The PDF is meant to mimic an error message within the PDF rendering engine and provides a link to “open the file” elsewhere. That link leads to a web page that tries to collect the victim’s credentials using a tool called EvilGinx, which conducts a man-in-the-middle attack that can steal user credentials and session cookies from the user as they access legitimate login pages.
How can Conceal’s Internet browsing security solution protect you from similar attacks?
Because ConcealBrowse resides in the web browser, it doesn’t matter where users click on malicious links. Whether the link is directly in an email, in a social media post from another app or the browser itself, or even within a PDF like in this example, ConcealBrowse scans every URL and takes appropriate action based on its associated risk.
In this case, the links would be opened on a throwaway virtual machine in the cloud utilizing our state-of-the-art remote browser isolation engine for further analysis. Once the threat is identified as a phishing attack, ConcealBrowse’s anti-phishing technology takes the additional step of preventing users from providing credentials or other sensitive information.
Furthermore, because the site with the EvilGinx malware was opened in an isolated browser off the user’s machine, its capabilities to intercept session cookies would be rendered useless.
ConcealBrowse provides multiple levels of security, and provides protection even in cases where users’ trust is abused to cause them to take high-risk actions. Constantly working in the background, ConcealBrowse is transparent to end users, and protects them from attackers and from themselves without getting in the way of their work.
If you’d like to learn more about how your organization can easily incorporate this zero-trust web browsing, click here to set up a demo today.
Browser-Based Threat Alert: Disneyland Malware Team
/in Blog /by Chad AndersonKrebs on Security recently reported on a financial crimes group that calls itself “Disneyland Team” using a relatively uncommon phishing technique. The technique relies on a little-known feature built into most web browsers that renders domain names with non-Latin characters. Called Punycode, the feature takes a URL that uses special character strings and renders it using non-Latin characters.
The upshot is that attackers can register domain names that contain these special strings and the browser will render them in a way that can be used to deceive. All major web browsers will render these URLs with the associated characters, many of which closely resemble Latin ones. One domain used by the Disneyland Team attackers – https://xn--clientchwb-zxd5678f[.]com – will be rendered as cliẹntșchwab[.]com, which closely resembles a legitimate Charles Schwab client portal. Clicking on a link to that URL will present the user with a page that appears to be legitimate, down to the appearance of the URL if the user is attempting to use the techniques taught in standard phishing protection training.
Remote Browser Isolation and Phishing Protection to the Rescue
While this technique varies slightly from others we’ve previously posted on, at its core it still preys on users’ inherent trust of the brands and businesses they interact with every day. It’s especially dangerous, however, because it renders ineffective one of the key phishing protection measures that many users are taught: Checking the URL bar or hovering over a link to see the true URL it points at to verify that it’s legitimate. As in the case of the Charles Schwab example above, the differences between the legitimate domain and the exploitative one can be as small as a tiny dot below one of the characters.
These are the type of user trust attacks that ConcealBrowse defeats. Instead of allowing users to make decisions based on their own trust and ability to spot suspicious sites, ConcealBrowse relies on advanced phishing identification and an intelligence-fed decision engine to identify and block these attacks.
ConcealBrowse stops these deceptive domains from tricking users two ways. First, if the site contains logos for the brands the attackers are attempting to subvert, ConcealBrowse will identify the logo using AI algorithms and recognize that the domain is not legitimately tied to the company represented by the logo, blocking the user from entering their credentials. Second, if the site is not being used for phishing the URL is identified by the ConcealBrowse decision engine and opened in a remote browser isolation session. This allows users to continue to interact with the site while their identity is hidden, and all code is executed on a throw-away isolated browser instance in the cloud where it can’t affect your network.
The Best Browser Security is Zero Trust at the Edge
Let us show you how ConcealBrowse can stop attacks that abuse users’ trust. Schedule a demo today and we’ll walk you through how your business can be protected from attacks like this one.
What’s the best browser security solution? One that ignores users’ trust.
/in Blog /by Chad AndersonCompanies slow on zero-trust uptake despite skyrocketing costs of cyberattacks
A recent article from DarkReading highlights the dire situation facing companies as the number of cyberattacks increase and the cost to recover from them balloons. According to a Dell Global Data Protection index survey, the average recovery cost in 2022 is over $1 million per incident, and disrupted organizations lost on average 2TB of data and suffered 19 hours of downtime.
Despite these alarming statistics, the survey indicated that 67% of respondents lacked confidence in their security measures. Additionally, while 91% were aware of or planning to deploy zero-trust security measures, only 12% are fully deployed.
One possible culprit behind the disparity between the understanding of the problem and the actions taken to fix it: A full zero-trust network architecture is extremely expensive and difficult to manage. Combined with the shortage of cyber security experts, this can become an insurmountable challenge to all but the most well-funded IT departments.
Remote browser isolation pushes zero-trust to the edge
It is a complex task to fully implement all the zero trust principles on an enterprise network. After all, networks have been built for decades on the premise that authenticated users can be trusted, and there is a massive number of both internal and cloud-based resources that need to be addressed across the board.
Over the last several years, however, more and more work is being done via web-based apps in the browser. This has partially fueled the rapid growth in internet browsing security and antiphishing software. One key development has been the application of zero trust principles to the browser via remote browser isolation (RBI) software. These solutions open web applications on virtual machines off your network, so that any malicious code runs on throwaway cloud infrastructure that doesn’t have access to your internal network.
The main problem with RBI solutions is that, up until now, they have all been expensive and difficult to manage. Frequently requiring hours of set up and configuration to ensure that the correct traffic is isolated, existing solutions create an additional burden on already-overburdened IT departments. And because running all or most browsing sessions in the cloud is expensive and resource intensive, the existing solutions are also costly enough that it is impossible to deploy across every browser on every endpoint within an organization.
Smarter, dynamic browser isolation
In response to these problems, Conceal has drawn on our years of experience selling remote browsing and managed attribution solutions to government and Fortune 500 organizations to create a smarter, simpler, and better solution. ConcealBrowse provides enhanced protection in Google Chrome and other browsers by being smart about when to use remote browser isolation.
By scanning every URL a user attempts to access in their browser and conducting an instant risk assessment, ConcealBrowse can ensure that risky sites are opened in isolation without wasting resources isolating low risk ones. This means that employees can still get their jobs done, even when it requires the use of riskier web sites and applications. Browser security is no longer reliant on users making their own judgments on what to trust, truly pushing the concept of zero trust to the edge.
All of this is achieved with minimal cost and extremely low administrative overhead. Once ConcealBrowse is installed, it starts working immediately without any required policy or settings adjustment. It’s a true plug and play solution. One of the first things our customers say whenever we ask for feedback is “It just works – I don’t really have to think about it.”
We believe ConcealBrowse is the future of browser security, so we’ve designed it to be easy to implement and easy to integrate into your existing security stack. If you’re interested in finding out more and seeing ConcealBrowse in action, request a demo today.
Conceal Threat Alert: Aurora Malware as a Service Targets Crypto Wallets & Credentials
/in Blog /by Chad AndersonAnother week, another piece of credential-stealing malware abusing trust to infect devices via the browser. Just before Thanksgiving, cybersecurity solution provider, Sekoia released a report on a recently discovered piece of malware dubbed “Aurora” by its developer. According to the report, Aurora is advertised as a malware-as-a-service that can be hired to steal credentials for cryptocurrency wallets and sensitive websites. Criminal groups wasted no time in developing social engineering and phishing approaches to distribute the malware.
While Aurora itself does not contain a delivery vector, enterprising criminal groups have put together at least one very professional-looking website designed to mimic the Exodus Wallet website and lure victims into downloading the malware with the promise of a crypto reward. Another delivery vector used by at least one group is YouTube videos posted on compromised accounts on how to download cracked software, and then providing a link to Aurora malware on a legitimate file-sharing platform. In both cases, the Aurora software then immediately connects to a C2 server allowing the attacker to steal data from the victim.
How can you stop this abuse of trust?
The criminals who developed the social engineering pathways to move users to download the Aurora malware utilize interesting tricks to deceive users into downloading the malware. In the case of the Exodus wallet, the phishing page is built to target one of the more lucrative use cases for Aurora: its ability to steal crypto wallets. The “cracked software” infection chain targets individuals who are already showing an elevated risk tolerance by searching for information on cracked software in the first place, as such sites are notoriously prone to malware.
We have previously discussed a case where the social engineering aspect of the attack was designed to target an audience with a specific set of characteristics. In that case, Dropbox engineers were fooled into providing their GitHub credentials by an attacker that was savvy enough to know about a specific tool. By masquerading as that tool, the engineers lowered their guard and provided their credentials to the site.
In all these cases, clever attackers identified specific characteristics of their prime targets and crafted attack chains that appealed to the very characteristics they were targeting. This type of social engineering regularly overcomes the mistrust that security awareness training attempts to instill in users. No matter how good an awareness program is, it is vital to provide a software-enforced zero-trust barrier between users and the Internet.
How can a user’s trust be made irrelevant?
ConcealBrowse is one option for ensuring that no matter how good a social engineering technique is, and no matter how real a phishing website looks, a user’s decisions and actions cannot result in a successful attack on your organization’s network. ConcealBrowse works silently in the background, checking every website, app, and resource loaded in your browser to determine if it is safe, risky, or malicious. ConcealBrowse then takes the necessary steps to make sure your organization remains secure.
Set up a call with us today to find out how ConcealBrowse can keep your organization safe from phishing, ransomware, and all other types of malware delivered through the browser.
Conceal Threat Alert: Instagram Users Targeted in Phishing Attack
/in Blog /by Chad AndersonAbusing Users’ Trust
Email protection firm Armorblox recently identified a credential theft phishing attack targeting over 20,000 users at a national institution within the education industry. The attack leveraged several common techniques to convince the user that the email and linked login page were legitimately associated with Instagram. This example takes advantage of human nature in the same way as several abuse-of-trust attacks we’ve detailed previously in this blog.
The initial email sent by the attackers contained the Instagram and Meta logos and utilized URLs containing the word “Instagram” to take advantage of users’ trust of the Instagram and Meta brands as a lure for the user to log in and “secure your account”. Because the email utilized URLs that could appear legitimate, and because the lure email looked legitimate and was free of spelling and grammar errors typically used to spot phishing emails, several techniques taught by cybersecurity training programs would be ineffective at getting users to report the email as a phishing attack.
Next, the web page that the email linked to also appeared professional and legitimate, utilizing the Instagram and Facebook logos as well as several legitimate Instagram links to make the page appear credible. The technique also prayed on the user’s concern that their Instagram account had already been compromised by alerting the user that there had been an “unusual login” and that they needed to enter their old password in order to change it. Of course, this was all a ruse to capture the user’s “old” password.
How Does ConcealBrowse Stop Credential Theft by Phishing?
Fortunately, ConcealBrowse can stop this type of phishing attack in its tracks by providing multiple levels of protection. First, any links users click are scanned by Conceal’s decision engine, which is built on advanced threat intelligence and assigns risk rankings to both reported and unreported infrastructure. Any known or suspected phishing sites are blocked before they are opened.
Next, ConcealBrowse’s AI-based phishing protection can identify phishing pages by comparing logos on the page with known domain names for the displayed company. In this case, even if the phishing page had never been reported as malicious, ConcealBrowse would have identified the fact that it did not reside on valid Instagram infrastructure – despite containing the Instagram logo – and blocked the user from providing credentials.
All of this powerful functionality is delivered in a simple plug-and-play package that requires minimal setup and configuration for your IT or security teams. In addition, information derived from our intelligence engine about visited URLs is available via our advanced telemetry feeds, and can be easily integrated into the rest of your security stack.
As social engineering gets more and more advanced, it will become ever more important to have the right tools to keep your network safe from phishing and ransomware. Click here to try ConcealBrowse today.