ConcealBrowse Analysis: Thwarting Advanced Cyber Threats in the Chemical Industry
Facing an ever-increasing cyber threat landscape, an integrated chemical and equipment company recognized the need for enhanced cybersecurity measures and strategically invested in ConcealBrowse. This decision proved crucial when ConcealBrowse identified a sophisticated threat that other security systems failed to detect.
ConcealBrowse in Action: Detecting and Analyzing a Complex Threat
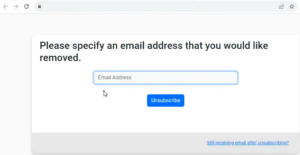
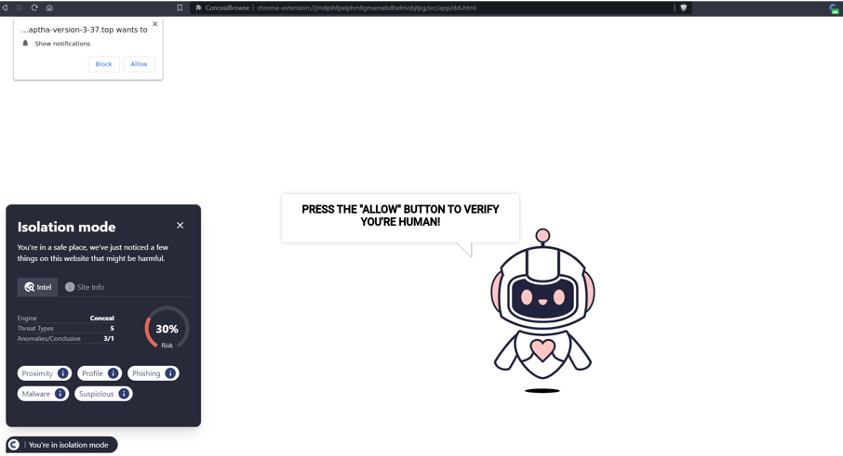
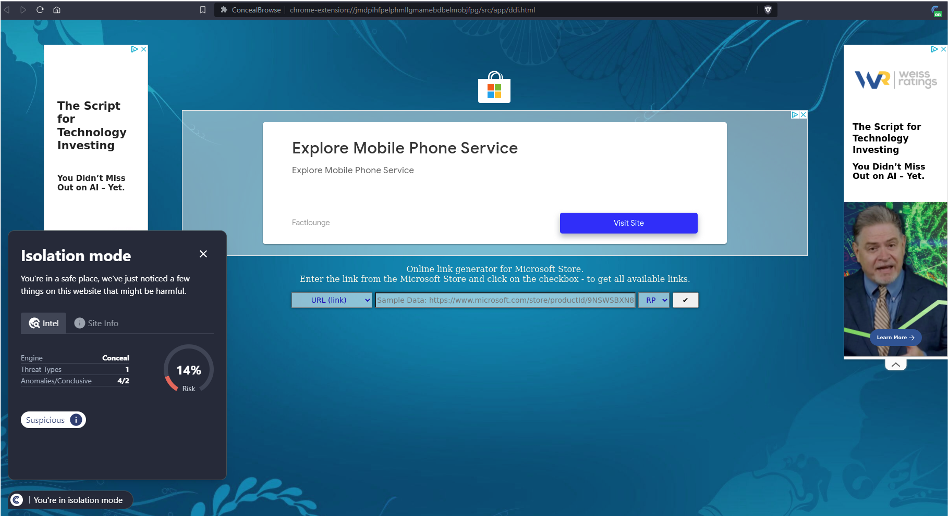
ConcealBrowse’s advanced capabilities came to the forefront when it detected a locally-hosted HTML file named “Salary-Review copy[.]htm.” This file, designed to mimic a legitimate Microsoft login page for credential harvesting, was unique in its approach, bypassing typical email-based phishing methods.
Indicators of Compromise (IOCs) Identified:
DOMAIN: ziralanded[.]xyz
IPV4: 45.93.139[.]225
SHA256 Hash: 2ae1cdc5d32960d2a985a0e3a9437428d760c680d5a6a3c1ce23f1b5470c5f1a
Deep Dive: Analysis
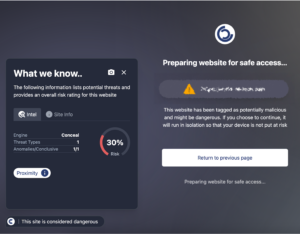
Our analysis revealed the file’s deceptive nature, utilizing local and internet-based resources. Crucially, it accessed ziralanded[.]xyz, likely controlled by attackers and hosted on infrastructure not immediately recognizable as malicious. This sophistication in avoiding detection underscores the evolving threat landscape.
Isolation at Work
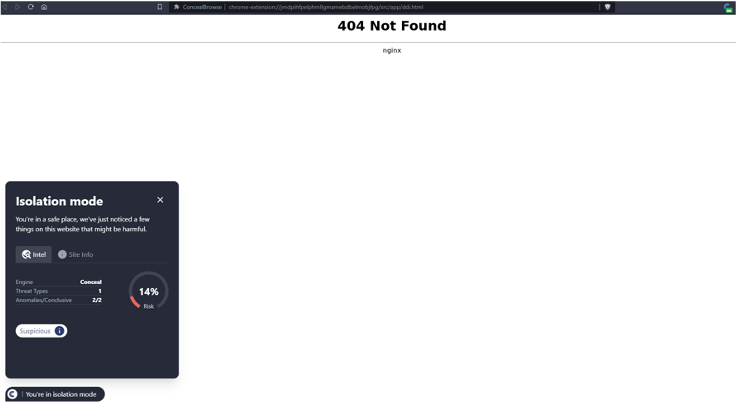
Upon detecting the file, ConcealBrowse’s isolation mechanism was activated. This feature opens potential threats in a remote, isolated session, ensuring any harmful actions are contained and the user’s actual device remains secure.
The Valuable Outcomes
This incident highlighted ConcealBrowse’s critical role in the company’s cybersecurity framework. By detecting and analyzing a sophisticated threat, ConcealBrowse not only protected the company’s network but also provided valuable insights into the tactics used by modern cyber attackers.
Conclusion
This case study underscores the importance of advanced cybersecurity solutions like ConcealBrowse in the modern digital landscape. Its ability to adapt and respond to new types of threats, including those that bypass traditional security measures, is invaluable. As the threat landscape evolves, ConcealBrowse continues to be an essential tool for organizations seeking to protect their digital assets and maintain robust cybersecurity defenses.