Browser-Based Threat Report: Feb 5
Browser-Based Threat Report
Week of February 5th, 2024
ConcealBrowse is leveraged by teams across the world to combat weaponized URLs. The technology is constantly analyzing suspicious web artifacts to identify risks in the form of drive-by attacks, phishing portals, and other threats that materialize while browsing.
At Conceal, your digital safety is our utmost priority. Our weekly threat report for the week of February 5th, 2024, unveils critical insights into the ever-evolving landscape of online threats.
The following report highlights recently detected sites that were deemed suspicious:
_____________
SHA-256:575e16e99fc8d3ac02f853c6bed65238f23bd6013a7e2321b4c260a171ad5047
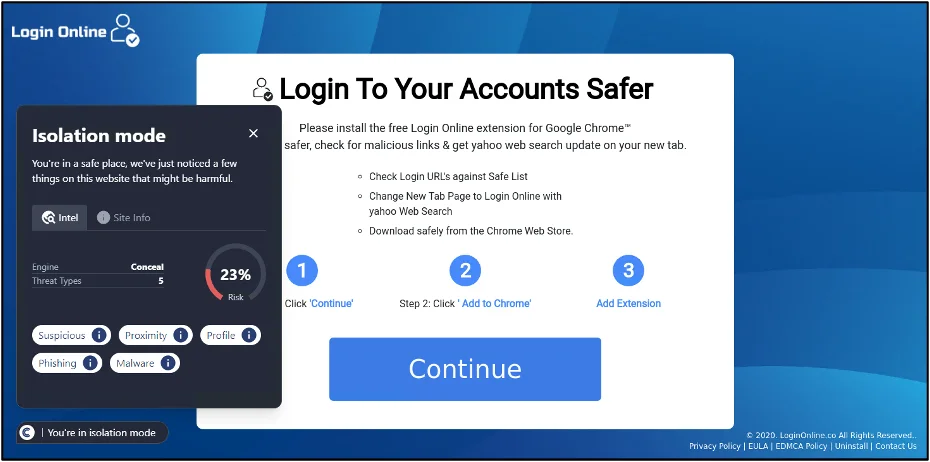
screenshot of homepage for a browser extension that was flagged by security vendors for malware, likely due to browser hijacking
This URL was detected by ConcealBrowse on February 2nd, 2024. It was flagged by four security vendors on December 4th and is still currently flagged by four vendors. ConcealBrowse intervened, assigning the page a 23% risk score due to potential malware.
This is the homepage for a browser extension that was flagged by security vendors for malware, likely due to browser hijacking. Browser hijacking occurs when software changes how your web browser interacts with websites. For example, it may change your home screen to a different search engine or redirect you to malicious websites. While in most cases it is more of a nuisance than nefarious, these types of extensions could easily redirect you to sites that could do more damage or steal your credentials.
Conceal recommendation: This URL and IP should be blocked with ConcealBrowse’s policies and by your other security tools.
_____________
SHA-256: c81549a6aa1a44d1858feaab9d01060950658b929e39c257b9d2854dd76b1387
This URL was detected by ConcealBrowse on February 1st, 2024. It was originally detected by 4 security vendors the same day, and that number has not changed. ConcealBrowse intervened, assigning the page a 14% risk score due to suspicion.
Although the page has since been removed by Microsoft, this site hosted a tech support scam. Tech support scams will claim that the user’s computer contains malicious software or viruses and prompt them to call a number to remove them. These numbers will pretend to be Microsoft support, but their goal is to steal personal information and money from victims. Sometimes, these scams will go as far as to tell the user to download malware onto their machine so that they can be exploited again in the future.
Conceal recommendation: Although links may originate from legitimate organizations like Microsoft, they can redirect you to unofficial or malicious sites. Unless users verify that the final domain is the one that they intended to visit, they may be unaware of the attack. Solutions, such as ConcealBrowse, that analyze the final destination web page, are crucial in detecting and defending against threats that hide through redirects.

screenshot of tech support scam URL detected by ConcealBrowse
_____________
SHA-256: 5b9542b700f786e8c7913aae5cef1696bf888ccc555de8ff1be809f4ed4b5363
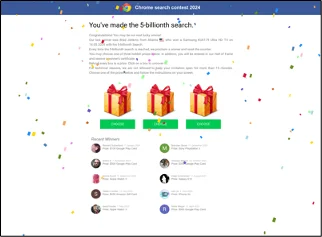
Screenshot of a similar page hosted by the same server
This URL was detected by ConcealBrowse on January 30th, 2024. It was first detected by one security vendor on December 29th and is currently detected by 14. ConcealBrowse successfully intervened, assigning the page a 39% risk score.
While the current page no longer exists, it is hosted by a server that contains multiple phishing URLs. The proximity to the malicious IP address allowed ConcealBrowse to detect the page regardless of content. In the past, these sites were used to host gift card scams. Gift card scams trick the user into believing they’ve won a monetary prize, only to redirect them to a malicious website that will steal their personal information and credit card.
Conceal recommendation: Sites like these change their content frequently but often use the same high-risk IP addresses. Blocking all access to this IP with ConcealBrowse , along with your firewall or other perimeter security solution, makes it less likely for users to encounter them.
_____________
Valuable Outcomes
As this recent threat reports exemplify, ConcealBrowse offers comprehensive protection against many sophisticated cyber threats. Our advanced threat detection capabilities have successfully flagged and quarantined malicious web pages, preventing users from falling victim to various cyber-attacks. Conceal remains dedicated to upholding the integrity of online interactions, constantly refining our detection algorithms and threat identification protocols to ensure proactive protection against emerging cyber threats. By integrating cutting-edge technology and a robust security infrastructure, we empower users to confidently navigate the digital landscape, knowing that their online activities are shielded from potential harm.
Join the Conceal Community and claim your FREE ConcealBrowse licenses!
Join the Conceal Community today and fortify your online security for free! Don’t miss the chance to benefit from our advanced threat protection and stay one step ahead of cybercriminals. Experience peace of mind while browsing the internet, knowing that ConcealBrowse is your shield against the ever-evolving threat landscape. Take the proactive step towards a safer online experience – get your free ConcealBrowse license now and join a community committed to safeguarding your digital world.
Sign up for the Conceal Community and claim your free licenses by completing the form below.







































