Browser-Based Threat Report: Mar 18
Browser-Based Threat Report
Week of March 18th, 2024
ConcealBrowse is leveraged by teams across the world to combat weaponized URLs. The technology is constantly analyzing suspicious web artifacts to identify risks in the form of drive-by attacks, phishing portals, and other threats that materialize while browsing.
At Conceal, your digital safety is our utmost priority. Our weekly threat report for the week of March 18th, 2024, unveils critical insights into the ever-evolving landscape of online threats.
The following report highlights recently detected sites that were deemed suspicious:
_____________
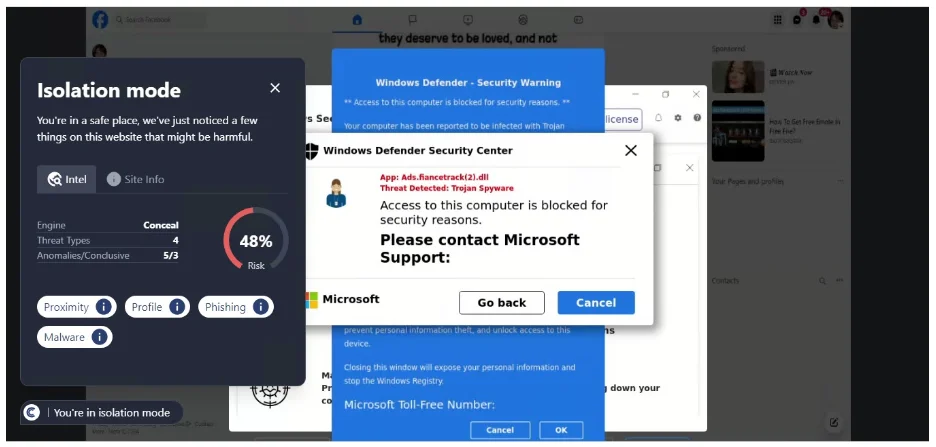
SHA-256: 8262cc68678bcc55f591816bf8021a705e6e193e6bd908599b3f0643d1a88ebc
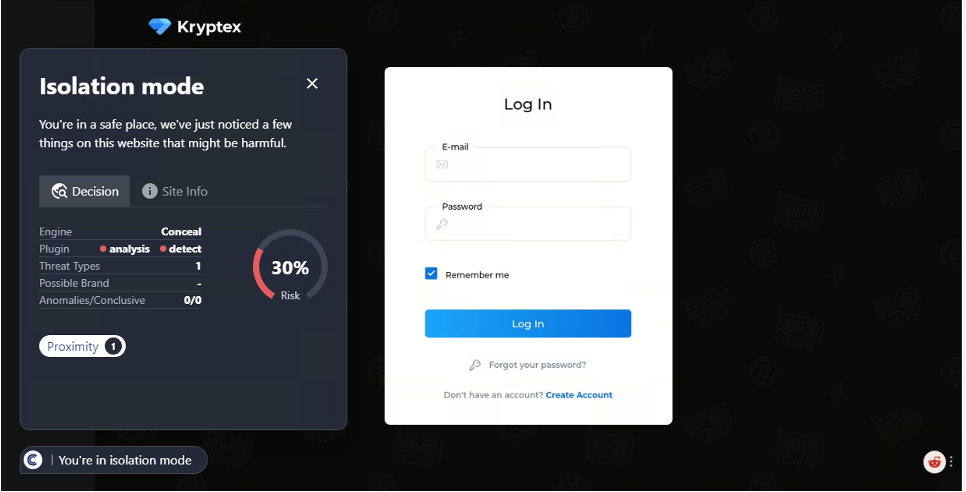
This URL was first detected by ConcealBrowse on March 14th. Later that day, one other security vendor began reporting on it and it is currently marked by six vendors for being phishing and malicious. ConcealBrowse successfully intervened with a 30% risk assessment, citing proximity, phishing, and suspicious behavior.
This page attempts to gather personal information about a user to initiate a scam. The URL appears to be directly from Facebook, and users may not view the page initially as phishing due to the form not asking for credentials. However, if the user were to enter their personal information, they’d receive a call from a number claiming to be Facebook. They may be asked for credentials or financial information to gain access to their account, but this is a scam for malicious actors to gain access instead.
Conceal Recommends: This URL should be blocked by policy. A browser security solution like ConcealBrowse is the best way to keep user information safe from these types of emerging threats.
_____________
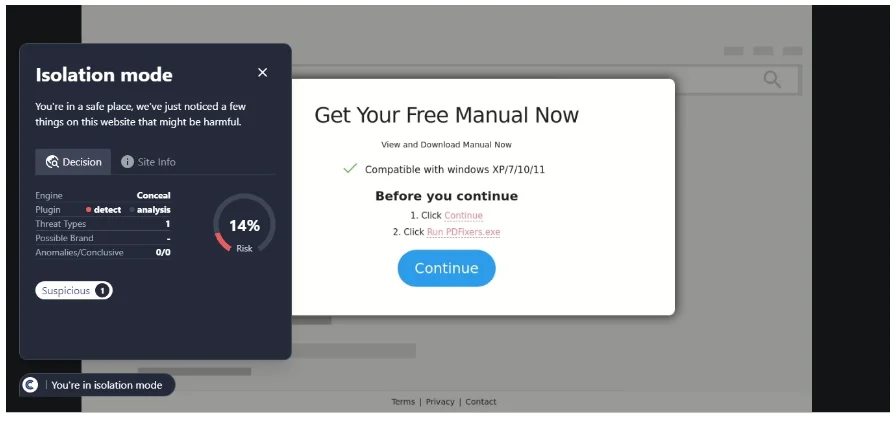
SHA-256: b576c2392256ac68bebefcc69add7b941d5cdd688b1e1b47913b33baba8c9051

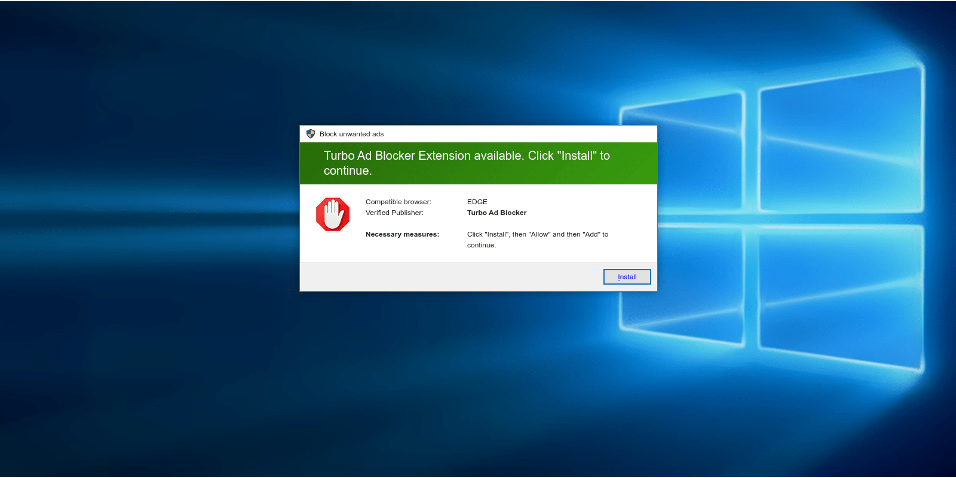
This page was first detected by ConcealBrowse on March 13th, the same day two other security vendors began flagging the URL for phishing. Currently there are 13 vendors that have identified its malicious behavior. ConcealBrowse successfully intervened on behalf of an end-user prior to the site’s removal with a 14% risk assessment.
This site hosted a common cryptocurrency scam. Cryptocurrencies scams aim to steal sensitive credential information to steal money from their victims. Users enter their personal wallet information under the belief that the site is only being used to house all their wallets in one place. However, the information will instead be used to gain access to the money and transfer it to different accounts before the user is able to react.
Conceal Recommends: This page is now removed, but the URL should still be blocked in the case that it is activated again. Cryptocurrencies carry a high risk, so consider implementing a content block on company devices and implementing an acceptable use policy regarding these sites.
_____________
SHA-256: 1ffae731284c35489567c0118c2f28f68ff75ea71ffd531b6ad113488afb081a
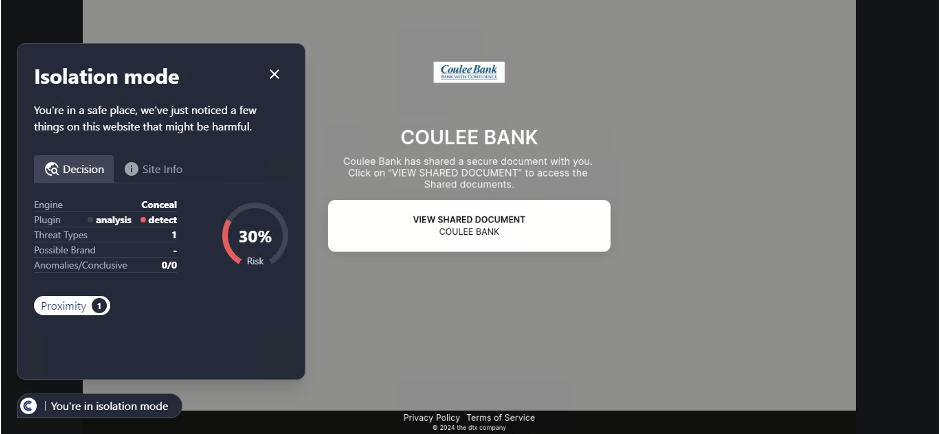
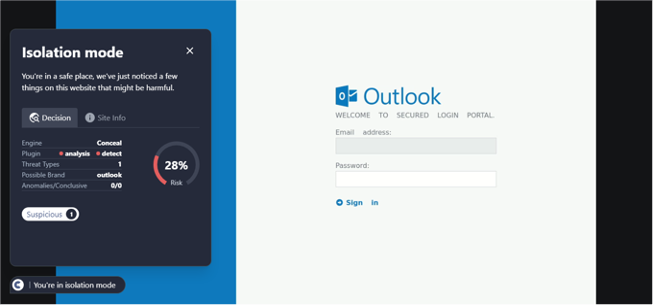
This URL was first detected by ConcealBrowse on March 18th, with five security vendors initially reporting it for phishing on March 13th. Currently, there are seven vendors flagging this URL as phishing and malicious. ConcealBrowse intervened with a 30% risk assessment, citing proximity to other malicious pages.
This page is part of a common document sharing phishing campaign. These scams are usually designed to target specific companies by sending emails to their targeted victims that appear to be from known organizations. When a user clicks on the link on the webpage, they will be redirected to the malicious site that will attempt to steal their credentials. ConcealBrowse’s intervention keeps the site in isolation even when redirects occur, keeping users from being able to enter their credentials.
Conceal Recommends: This URL should be blocked. ConcealBrowse’s use of isolation technology helps prevent users for falling for credential theft from suspicious sites.
_____________
Valuable Outcomes
As this recent threat reports exemplify, ConcealBrowse offers comprehensive protection against many sophisticated cyber threats. Our advanced threat detection capabilities have successfully flagged and quarantined malicious web pages, preventing users from falling victim to various cyber-attacks. Conceal remains dedicated to upholding the integrity of online interactions, constantly refining our detection algorithms and threat identification protocols to ensure proactive protection against emerging cyber threats. By integrating cutting-edge technology and a robust security infrastructure, we empower users to confidently navigate the digital landscape, knowing that their online activities are shielded from potential harm.
Join the Conceal Community and claim your FREE ConcealBrowse licenses!
Join the Conceal Community today and fortify your online security for free! Don’t miss the chance to benefit from our advanced threat protection and stay one step ahead of cybercriminals. Experience peace of mind while browsing the internet, knowing that ConcealBrowse is your shield against the ever-evolving threat landscape. Take the proactive step towards a safer online experience – get your free ConcealBrowse license now and join a community committed to safeguarding your digital world.
Sign up for the Conceal Community and claim your free licenses by completing the form below.