The Growing Impact of Cybersecurity on Credit Ratings: What Companies Need to Know
As cybersecurity becomes an increasingly vital aspect of a company’s operations, credit rating agencies are beginning to incorporate cybersecurity factors into their evaluations of corporate creditworthiness. This shift highlights the growing importance of strong cybersecurity practices in maintaining a company’s financial stability and reputation. In this blog post, we will discuss how credit rating agencies are now considering cybersecurity in their assessments and what companies can do to improve their cyber risk management.
Cybersecurity as a Credit Rating Factor
A recent report by The Washington Post revealed that credit rating agencies such as Moody’s, S&P Global Ratings, and Fitch Ratings are increasingly looking at a company’s cybersecurity posture when determining credit ratings. This move follows a growing trend of cyberattacks targeting corporations, which have led to significant financial losses and reputational damage for the affected businesses.
Companies that have suffered major cybersecurity incidents, such as data breaches or ransomware attacks, are now more likely to see their credit ratings downgraded. This can lead to higher borrowing costs and a reduced ability to access capital markets. On the other hand, companies with robust cybersecurity practices may receive more favorable credit ratings, potentially lowering their cost of capital and increasing their attractiveness to investors.
How can companies protect their bottom line?
To effectively incorporate cybersecurity factors into credit ratings, agencies are increasingly relying on cyber risk assessments. These assessments aim to evaluate a company’s cyber risk exposure and its ability to prevent, detect, and respond to cyber threats. Credit rating agencies may also consider the potential financial impact of a cyber incident on a company’s balance sheet, cash flow, and overall creditworthiness.
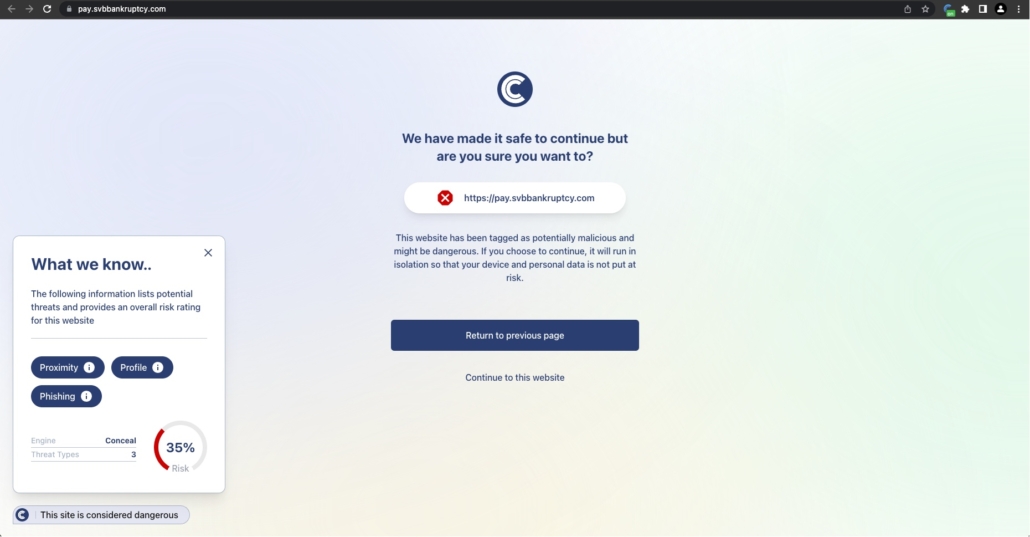
The Post report notes that small and medium sized businesses are the least likely to invest enough in cyber security measures. Tools like ConcealBrowse can provide tremendous bang for the buck, providing critical missing coverage over an entire organization at a manageable cost.
Given the growing importance of cybersecurity in credit ratings, companies must prioritize cyber risk management in their overall business strategy. Here are a few steps businesses can take to enhance their cybersecurity posture:
- Implement a comprehensive cybersecurity framework: Companies should adopt a recognized cybersecurity framework, such as the NIST Cybersecurity Framework or the ISO/IEC 27001 standard, to guide their cybersecurity policies and procedures.
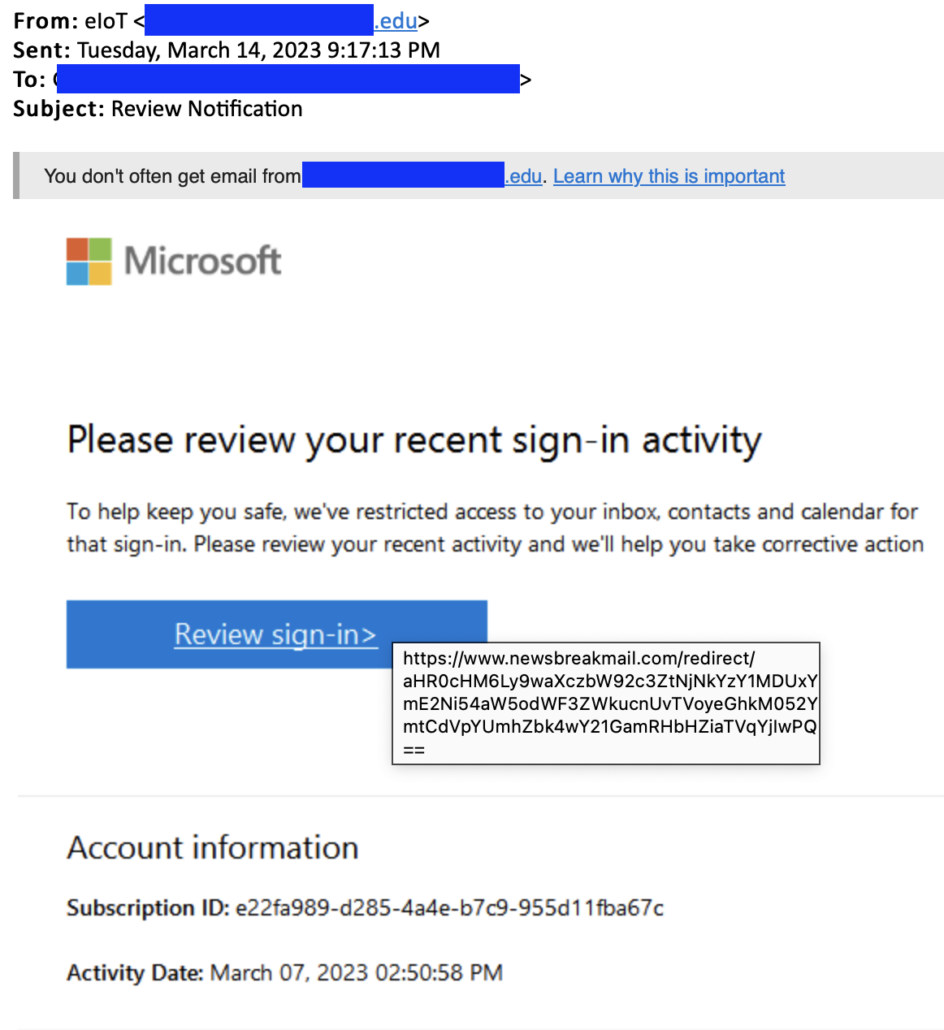
- Embrace zero-trust principles wherever possible: Employees are often the weakest link in any cybersecurity program. While training and awareness programs can reduce the chances of falling victim to phishing or other types of trust-based attacks, invest in solutions like ConcealBrowse that take decisions on trust and risk assessment out of the hands of the end user.
- Regularly assess cyber risk exposure: Conducting regular cyber risk assessments can help organizations identify vulnerabilities and gaps in their cybersecurity defenses, allowing them to take appropriate remedial actions.
- Collaborate with industry peers and government agencies: Sharing information on cyber threats and best practices with other companies and government organizations can help businesses stay ahead of emerging cyber risks.
- Engage with credit rating agencies: Companies should proactively engage with credit rating agencies to understand their cybersecurity expectations and communicate their efforts to address cyber risks.
Conclusion:
The incorporation of cybersecurity factors into credit ratings highlights the growing recognition of cyber risk as a significant business concern. Companies that prioritize cyber risk management and demonstrate robust cybersecurity practices are more likely to receive favorable credit ratings, which can have tangible benefits in terms of lower borrowing costs and increased investor confidence. By taking proactive steps to improve their cybersecurity posture, businesses can better position themselves for long-term success in an increasingly interconnected and cyber-risky world.
To find out more about how ConcealBrowse can make your business more secure and less risky to creditors and investors, click here to schedule a demo today.