Browser Based-Threat Alert: Bumblebee Malware Campaign – When Malicious Ads Meet Compromised Websites
/in Blog /by LaceyThe threat landscape is continuously evolving, and cybercriminals are employing new and sophisticated tactics to target their victims. We have previously written about attacks utilizing “Search Engine Optimization (SEO) poisoning” on Google Ads to link to malware delivery sites. In SEO poisoning attacks, actors purchase Google Ads on targeted search terms to cause Google to serve malicious links in ads that are crafted to look like legitimate trusted web sites.
One such campaign was recently observed by Secureworks’ Counter Threat Unit (CTU) researchers. It involves the distribution of Bumblebee malware via trojanized installers for popular software, such as Zoom, Cisco AnyConnect, ChatGPT, and Citrix Workspace. Bumblebee, a modular loader, has historically been delivered through phishing and is commonly associated with ransomware deployments. The current campaign, however, leverages malicious Google Ads and compromised WordPress sites as the initial attack vectors to infect victims’ systems.
The researchers analyzed one of the Bumblebee samples and found that the infection chain began with a malicious Google Ad that redirected users to a fake download page for Cisco AnyConnect Secure Mobility Client. The fake page was hosted on the domain “appcisco[.]com,” which was created by the threat actor on or around February 16, 2023. This malicious redirection occurred via a compromised WordPress site. Once on the fake page, victims would download the trojanized installer, which contained an MSI file that executed two files when run. The first file was a legitimate installer for the Cisco AnyConnect VPN application, while the second was a malicious PowerShell script with an encoded Bumblebee malware payload.
The campaign’s success relied on the effective use of malicious Google Ads and the compromise of WordPress sites. By combining these tactics, the attacker was able to redirect victims to fake download pages that appeared legitimate, enticing them to download and run the trojanized installers. The attacker’s objective, as observed in one compromised environment, was to deploy ransomware. However, in this particular case, network defenders detected and disrupted the attacker’s activity before they could achieve their goal.
Fortunately, ConcealBrowse can defeat SEO poisoning attacks like this one. Because ConcealBrowse brings zero trust principles to the browser, even the most convincing ads can quickly be detected and blocked, preventing users from downloading malicious files or providing their sensitive information, even if they don’t realize the site is fake and malicious.
The Bumblebee malware campaign serves as a cautionary tale of how cybercriminals can exploit online advertising platforms and compromised websites to distribute malware. Organizations must remain vigilant and adopt solutions like ConcealBrowse to proactively detect and isolate threats and safeguard their digital assets. Click here to try ConcealBrowse for free today.
Enhancing Cybersecurity at Community College
/in Resources /by LaceyA mid-size community college with approximately 3,000 faculty and staff and 70,000 students was experiencing high susceptibility among its users to phishing attacks, resulting in the execution of malware payloads and loss of credentials. Despite performing security awareness training for years, the college found that users in any group were susceptible to a range of scam techniques, and they operate on a limited budget.
Browser-Based Threat Report: ConcealBrowse Thwarts Sophisticated Spear Phishing Attack Targeting Conceal CEO
/in Blog /by LaceyConcealBrowse’s Advanced Protection Overcomes Traditional Anti-Phishing Tool Limitations
In a recent spear phishing attack, cybercriminals targeted Conceal’s CEO, Gordon Lawson, bypassing Microsoft 365’s strict anti-phishing protection. This was a highly-targeted attack utilizing advanced techniques to evade detection, but ConcealBrowse effectively protected against the threat by analyzing metadata about the URL used in the attack even though it wasn’t flagged as malicious in traditional intelligence sources.
Bypassing Anti-Phishing Protections
The attackers utilized several techniques intended to defeat common anti-phishing protections:
1. The phishing email contained a screenshot of a typical Microsoft sharing screen linked to an obfuscated URL, operated by a legitimate company, Constant Contact, with a strong reputation.
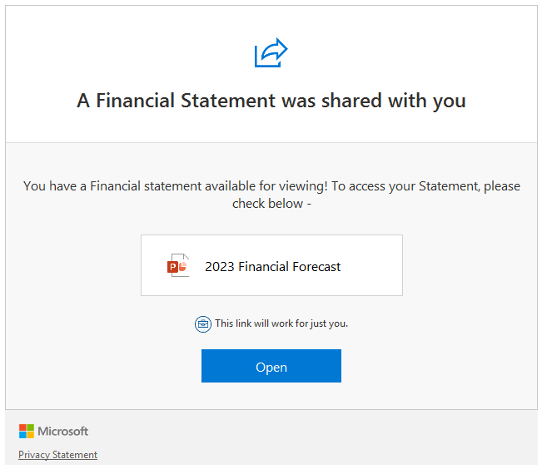
2. The email body contained significant whitespace followed by seemingly legitimate content, which helped it defeat the email-based phishing detection algorithms.
3. The threat actor passed encoded metadata and a URL through a redirect page, which behaved differently on the first visit vs. Subsequent ones. In some cases after the first visit, the victim would be redirected a legitimate Microsoft login page. To defeat sandboxing and similar protections, a captcha was used on the first visit. These steps were aimed at reducing the chances of the malicious site being detected and flagged by automated analytical tools.
Targeted Attack Characteristics
Several indicators suggest this was a targeted attack:
- Compromised sender account: The sender’s reputation, as determined by DKIM, SPF, and Composite authentication, was associated with Microsoft. However, the display name and recipient address raised suspicions, implying the attack originated from a compromised email account.
- Customized login page: The phishing email redirected users to a convincing Microsoft login prompt that included the Conceal logo and almost exactly mimicked the real Microsoft authorization page.
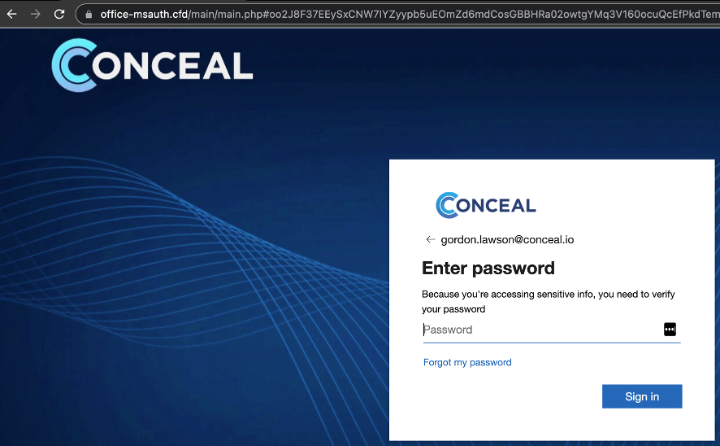
ConcealBrowse’s Protection Against the Attack
ConcealBrowse’s advanced security measures effectively protected against the spear phishing attack by focusing on metadata analysis of the URL used in the attack. Even though traditional intelligence sources had not flagged the URL as malicious, ConcealBrowse identified potential risks based on the following indicators:
Domain registration: The recently registered domain prompted ConcealBrowse to isolate the session to protect users. This proactive approach ensured that any potential threats associated with the domain were contained, keeping the business secure.
Multi-layered defense: ConcealBrowse employed multiple data sources and indicators to provide robust protection against the attack, demonstrating the importance of a comprehensive approach to cybersecurity.
Indicators of Compromise:
The following indicators were observed as part of this campaign:
| TYPE | INDICATOR | NOTES |
| DOMAIN | https://office-msauth.cfd/ | Mimicked a Microsoft authentication page, customized with the Conceal logo. |
| IPV4 | 209.141.52.236 |
Conclusion
The sophisticated and targeted spear phishing attack exemplifies the evolving tactics of cybercriminals and the limitations of traditional anti-phishing tools. ConcealBrowse’s advanced protection, based on metadata analysis and multi-layered defense, effectively thwarted the attack. The fact that attackers are constantly evolving to defeat the latest defensive techniques emphasizes the need for businesses to adopt innovative security measures to safeguard sensitive information and maintain a secure environment. Click here to schedule a demo of ConcealBrowse today.
Browser-Based Threat Report: The Tax Day Tangle – Cybercriminals’ Taking Advantage of Stressful Season to Deliver Malware
/in Blog /by LaceyAs the April 18 tax deadline approaches in the United States, accountants and finance professionals are under immense pressure to file tax returns for their clients. Unfortunately, cybercriminals have been taking advantage of this time-sensitive and stressful period to launch a targeted phishing campaign with the goal of gaining unauthorized access to sensitive personal information. According to research done by Microsoft and covered in a recent DarkReading report, cybercriminals are utilizing well-crafted phishing emails and multiple URL redirections to bypass traditional security measures.
The attacks begin with a carefully crafted phishing email sent to Certified Public Accountants (CPAs), accounting firms, and related companies handling tax information. In these emails, the attackers masquerade as existing clients, using subtle social engineering techniques to appear more legitimate. For example, some emails include lines like “I apologize for not responding sooner” and the subject line “Re: 2022,” implying an ongoing correspondence. The inclusion of a password-protected link labeled as “confidential” adds an air of security to the message, making it more believable.
To evade detection by traditional cybersecurity tools, the phishing email contained a link that redirected the recipient through multiple legitimate services. The first redirection leads to an Amazon Web Services click-tracking service, followed by redirection to an ordinary file-hosting site. These layers of redirection serve to evade potential anti-malware detection. Ultimately, the link leads to a .ZIP file containing malicious files designed to trigger the download of the Remcos remote access Trojan (RAT), a malware capable of granting attackers the same level of privileges over the victim’s computer as the victim.
Obviously, the timing of this attack is no coincidence. Cybercriminals strategically initiated the campaign in February, coinciding with the busiest time of year for accountants and finance professionals. They recognized that professionals working long hours and responding to numerous emails late at night might be more susceptible to making mistakes or clicking on malicious links.
Fortunately, Conceal’s secure browser extension, ConcealBrowse, can play a vital role in protecting users. ConcealBrowse acts as a proactive security layer, making real-time decisions about the security risk associated with internet use and automatically isolating risky transactions without interrupting the user. It opens risky sites in an isolated environment, ensuring that no malicious code or files are ever executed on the user’s device. Multiple browser redirect strategies like the one implemented in this attack cannot evade detection by ConcealBrowse, as every URL loaded into the browser is checked in real-time. So, even if the first malicious URL is the third in a series of redirects, ConcealBrowse will identify the URL as malicious and take appropriate action.
The Remcos RAT phishing campaign serves as yet another reminder of the evolving tactics used by cybercriminals to exploit vulnerabilities in human behavior. With the use of social engineering and multiple URL redirections, attackers can bypass traditional security measures. However, ConcealBrowse can provide a robust extra layer of defense against such attacks. As Tax Day approaches, we urge individuals and organizations to exercise caution and utilize tools like ConcealBrowse to mitigate the risk of falling victim to cyber-attacks. Click here to sign up for a live demo of ConcealBrowse and see how it can help protect your organization today.
Tech Spotlight: ConcealBrowse Dashboard – Enhancing Visibility and Security Control
/in Blog /by Chad AndersonIn today’s digital landscape, organizations are continuously exposed to threats that can bypass traditional security controls. ConcealBrowse offers a comprehensive solution that provides security to malicious activity that may go undetected by other security measures. Additionally, the corresponding dashboard provides enhanced visibility and insights into activities that may go unnoticed by other tools. In this tech spotlight blog, we’ll explore the features of the ConcealBrowse Dashboard and discuss how it can help organizations improve their security posture.
ConcealBrowse Dashboard Features
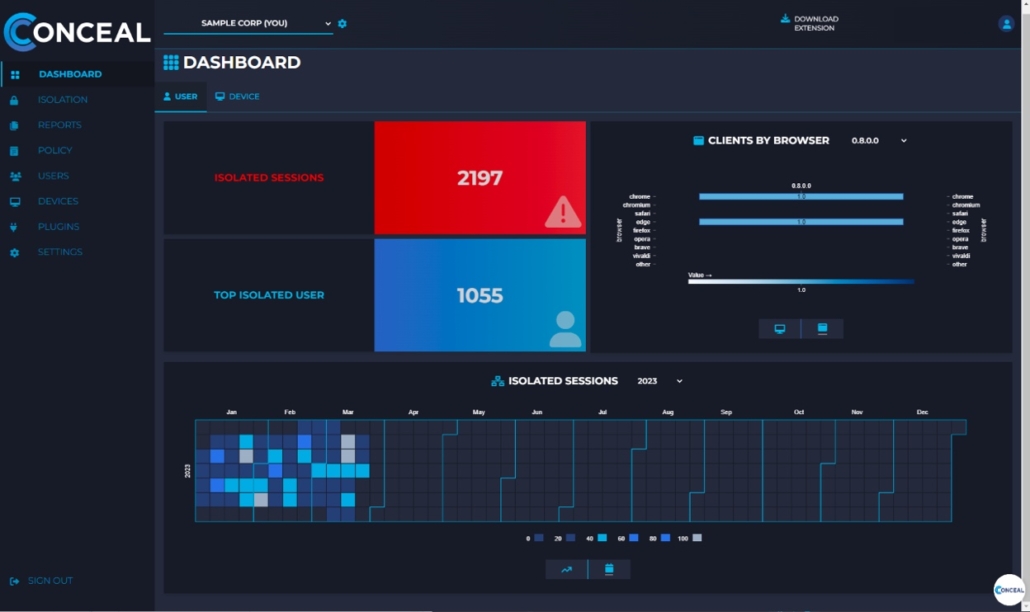
The ConcealBrowse Dashboard offers a range of reports and graphs that provide valuable insights into isolated sessions and user behavior. Some of these include:
Isolated Sessions: This report displays a detailed view of all isolated sessions, allowing security teams to monitor and assess potential threats effectively.
Top Isolated Entities: This report highlights the most frequently isolated URLs, enabling organizations to identify high-risk areas and prioritize corresponding remediation efforts.
Highest Isolated Sessions: This report ranks users or devices based on their number of isolated sessions, helping security teams identify targeted individuals or those who may require additional training.
Visualizing Security Data
The ConcealBrowse Dashboard offers various graphs that enable organizations to visualize and analyze security trends effectively. Some key visualizations include:
Trend of Isolated Sessions: This graph displays the overall trend of isolated sessions over time, helping organizations identify patterns and respond proactively to emerging threats.
Number of Isolated Sessions: This visualization provides a clear overview of the total number of isolated sessions, allowing security teams to gauge the effectiveness of their security measures.
Isolated Sessions per Day: This graph shows the daily count of isolated sessions, enabling organizations to track and manage security incidents more effectively.
OS and Browsers Hooked Up: This visualization offers insights into the operating systems and browsers connected to the ConcealBrowse platform, helping organizations tailor their security strategies according to the specific technologies in use.
Enhancing Security Through Visibility
The ConcealBrowse Dashboard provides organizations with the visibility needed to identify and respond to security threats that might bypass conventional security controls. By offering comprehensive insights into isolated sessions and user behavior, the dashboard enables organizations to optimize their security measures, identify targeted individuals, and provide additional training where necessary.
Conclusion
In an increasingly complex threat landscape, organizations must remain vigilant and adopt security solutions that provide comprehensive visibility into their digital environments. The ConcealBrowse Dashboard offers a powerful solution to help organizations stay ahead of potential threats and maintain a robust security posture. By leveraging the dashboard’s advanced features and visualizations, security teams can make informed decisions and protect their organizations from emerging risks.







