Conceal appoints cybersecurity leaders Brian NeSmith and Diane Honda to its Board, strengthening its strategic direction and growth in browser security innovation.
June 5, 2024, 11:08 AM Eastern Daylight Time
AUGUSTA, Ga.–(BUSINESS WIRE)–Conceal, the leader in cutting-edge browser security, announces the addition of Brian NeSmith and Diane Honda to its Board of Directors. Both bring extensive expertise and leadership in cybersecurity and business transformation, further strengthening Conceal’s strategic direction and growth.
Brian NeSmith, an internationally recognized business leader, has over 30 years of cybersecurity leadership experience. As the founder of Arctic Wolf and the former CEO of Blue Coat Systems, Brian has a proven track record of driving revenue growth and scaling organizations globally. His expertise in security services, enterprise software, and cloud transformation has established new market categories and raised the bar for enterprise solutions. Brian graduated from the Massachusetts Institute of Technology with a Bachelor of Science in Electrical Engineering.
“Brian commented, “Conceal is revolutionizing the security landscape by addressing the largest and most destructive threats at the browser level. I am thrilled to join the board and support the company’s innovative approach to cybersecurity.”
Diane Honda, former Chief Administrative Officer, General Counsel, and Secretary of Barracuda Networks, brings a wealth of experience in global legal, human resources, compliance, operations, and enterprise risk management. Having led Barracuda through significant acquisitions and sales, Diane has been instrumental in operational and business transformations, mergers and acquisitions, leadership development, and corporate governance enhancement. She holds a JD from Santa Clara University School of Law and a Bachelor of Science in Applied Math/Computer Science and Industrial Management from Carnegie Mellon. Diane currently serves on the Board and Compensation Committee of The Hillman Group (Nasdaq: HLMN), and on the Board and Audit Committee of LucidWorks, Inc., a provider of next-generation AI-powered search applications.
“Conceal’s purpose-built MSP capabilities are unmatched in the industry. I am excited to join the board and contribute to the company’s mission of enhancing browser security for these critical companies tasked with defending the most vulnerable businesses,” said Diane Honda.
“I’m ecstatic to have two individuals of this caliber join Conceal’s Board of Directors,” said Spencer Tall, Managing Director of AllegisCyber. “Brian NeSmith and Diane Honda bring unparalleled expertise and leadership in cybersecurity and business transformation, which will undoubtedly strengthen Conceal’s strategic direction and growth.”
Gordon Lawson, CEO of Conceal, stated, “It’s a great honor to add these two cybersecurity titans to the Conceal Board. Both Diane and Brian will help take Conceal’s explosive growth to the next level, and I’m delighted to welcome them to our team.”
About Conceal
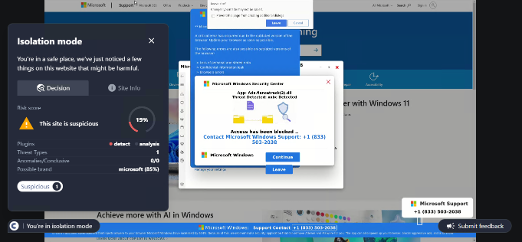
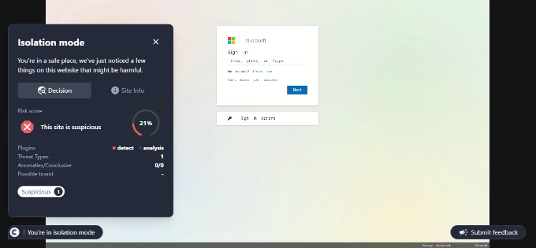
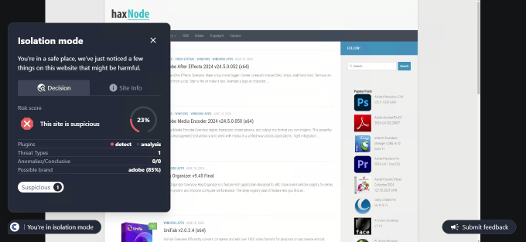
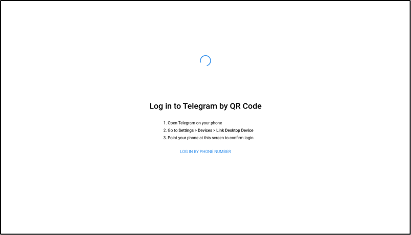
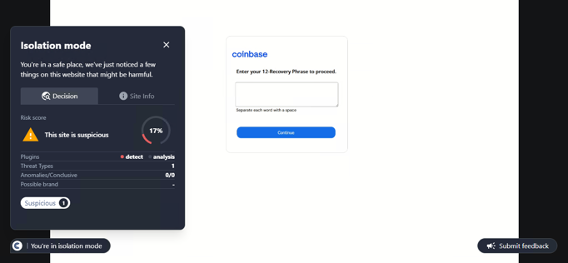
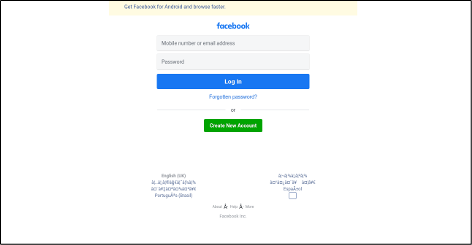
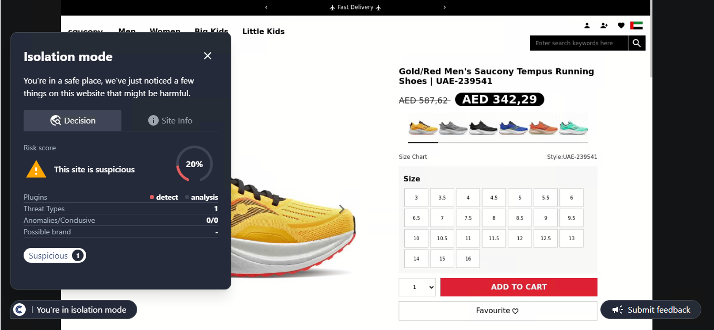
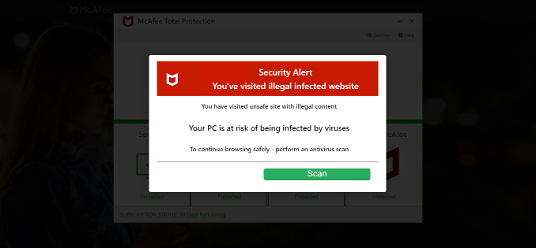
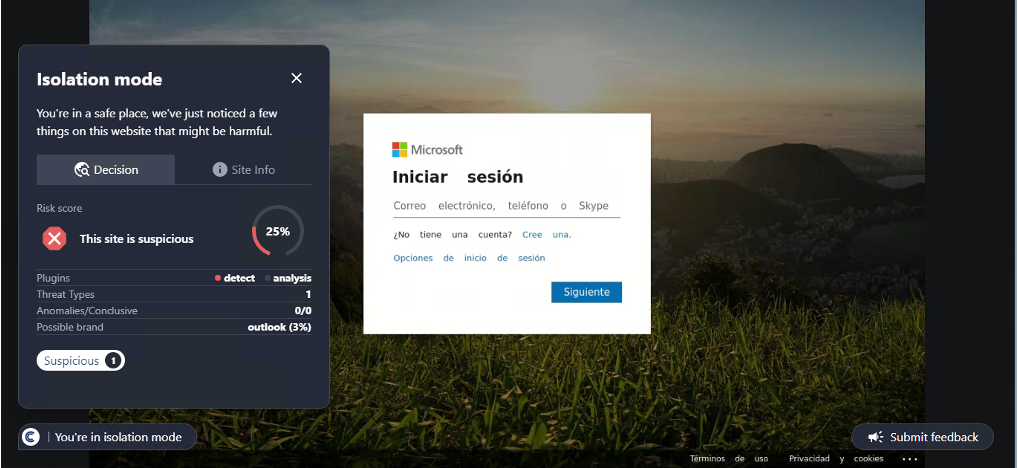
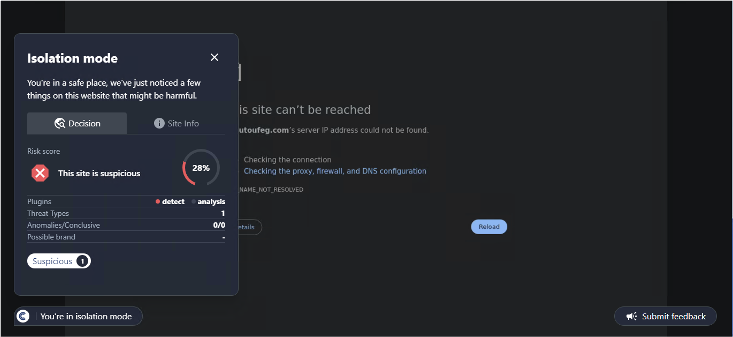
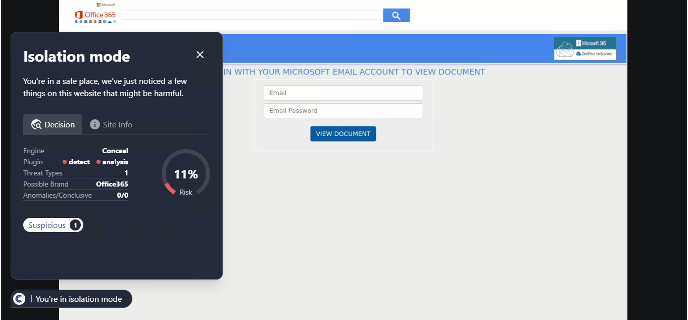
Conceal is dedicated to protecting organizations from web-based threats with its innovative solution, ConcealBrowse. An AI-powered browser extension, ConcealBrowse offers a private, lightweight, and easy-to-deploy defense against ever-evolving phishing, credential theft, and sophisticated social engineering attacks. By safeguarding the most vulnerable element of any organization—the human using a web browser—ConcealBrowse significantly mitigates the risk of destructive and costly cyber-attacks. For more information, visit https://conceal.io/conceal-browse/.