ConcealBrowse: A Frontline Defense in Isolating a Threat That Outsmarted Edge Controls
As cyber threats become increasingly sophisticated, the need for advanced protective measures grows more urgent. Recognizing this, a forward-thinking state government organization recently invested in our cybersecurity solution: ConcealBrowse. This advanced tool proved crucial when a subtle threat slipped past all the organization’s other proactive controls at the edge.
The Role of ConcealBrowse in Identifying Threats
When the URL https://oneettinlive[.]com/ was detected on one of the organization’s endpoints, ConcealBrowse was on the case, swiftly isolating it for further investigation. Our analysts examined this URL, unearthing several Indicators of Compromise (IOCs) directly and indirectly related to it. These IOCs were linked to several domains, including:
- oneettinlive[.]com
- waterdumb[.]link
- watchlisten[.]fit
- sleepyreturn[.]link
- getlift[.]world
- go0lgle[.]xyz
- costperform[.]link
- profitdraw.casa
The Analysis: How ConcealBrowse Works
Our intelligence sources flagged the URL as suspicious, triggering the ConcealBrowse decision engine to isolate the website. Upon further investigation, we discovered the site employed basic social engineering to deceive users into enabling browser alerts. These alerts could then be used to distribute spam advertising or redirect users to other malicious websites or malware.
More alarmingly, our investigation revealed that the site shared an ad tracking ID with at least 11 other malicious websites, suggesting that they are all likely owned and operated by the same threat group.
The Power of Isolation
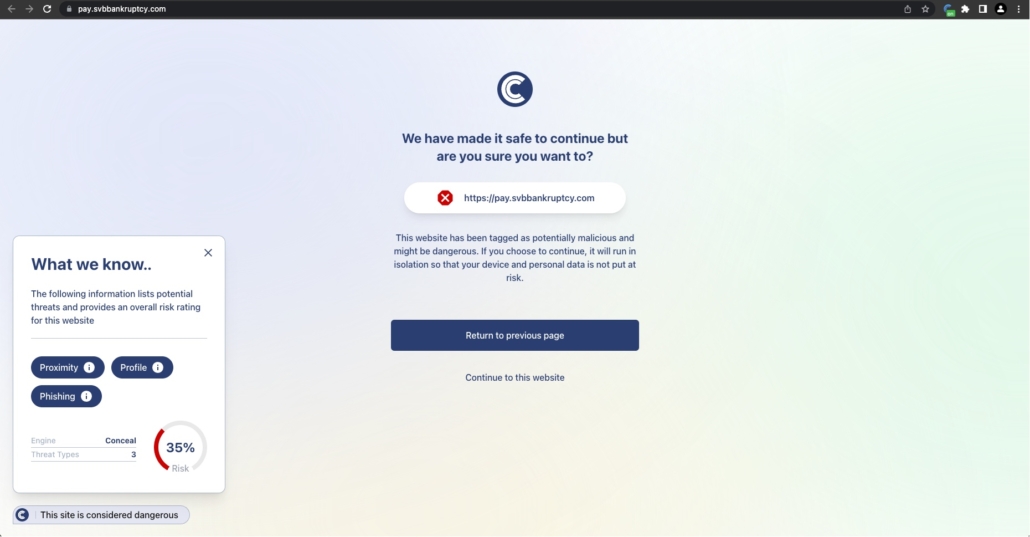
So, how does ConcealBrowse’s isolation process work? The answer lies in its pioneering approach to cyber defense. When confronted with a potentially harmful site, ConcealBrowse opens the site in a remote, isolated session. Any permissions requested by the site only apply to this isolated environment, not the user’s actual browser.
This means that even if a user is tricked into clicking “Allow” on a malicious alert, the threat remains contained within the isolated session and doesn’t affect the actual browser. Importantly, these malicious alerts won’t be displayed once the isolated session ends, keeping the user’s browsing environment secure.
Valuable Outcomes
This incident underscores the importance of our product’s innovative isolation technology. Not only did ConcealBrowse detect and contain a threat that slipped past other edge controls, but it also protected the organization’s endpoints from being compromised.
Further, our analysis provided a deeper understanding of the threat, including the tactics and strategies used by the attackers. This valuable insight allows the organization to bolster its security measures, making it better equipped to handle similar threats in the future.
Conclusion
The recent victory of ConcealBrowse over a stealthy cyber threat underlines the importance of investing in advanced cybersecurity tools. The innovative isolation technology of ConcealBrowse ensures threats are effectively contained, securing your digital environment from increasingly sophisticated cyber-attacks. Our commitment to delivering robust security solutions continues to protect and empower organizations in the face of evolving cyber threats.