Browser-Based Threat Alert: Increased Phishing Attacks on Collaboration Platforms Highlight the Importance of Zero-Trust Browser Protection
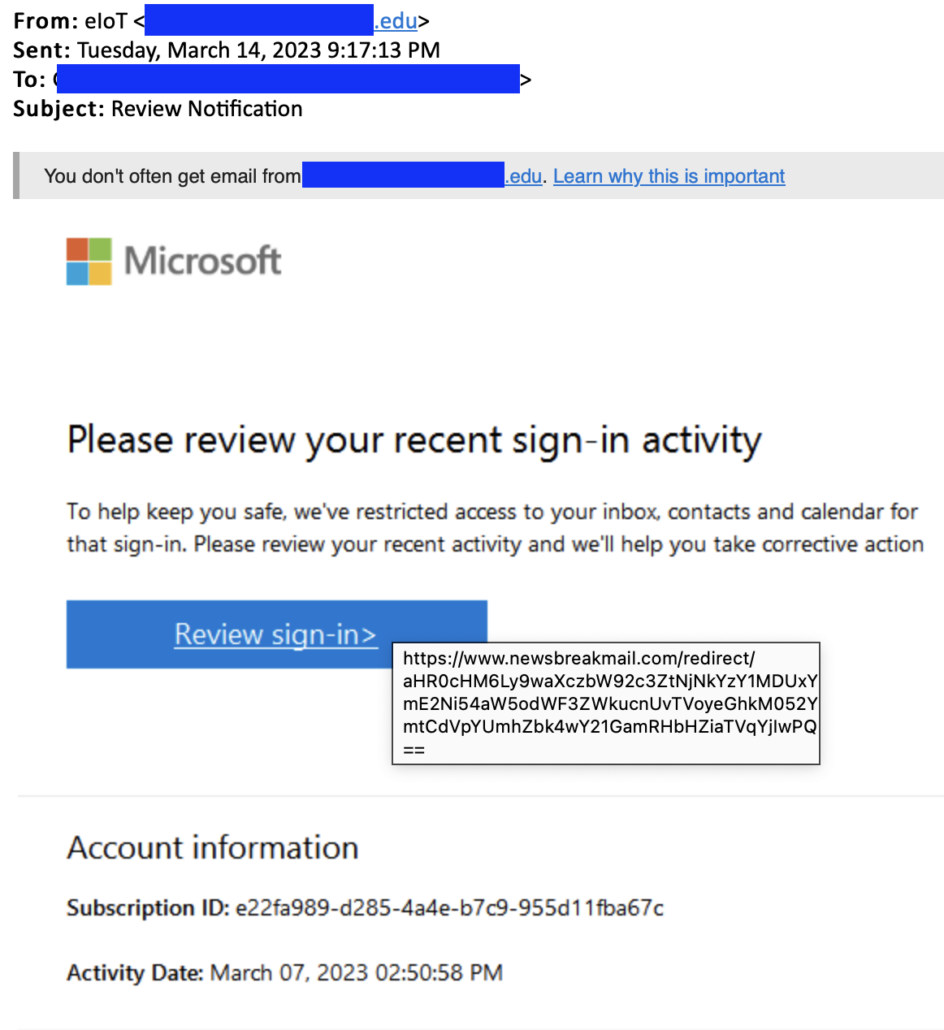
Phishing attacks have long been a serious threat to businesses, but recent reports indicate that the problem is becoming even more pervasive. Email remains a primary target, but attackers are also expanding their focus to collaboration platforms such as Slack and Microsoft Teams. With the shift to hybrid work environments, these platforms have become popular avenues for exploitation by opportunistic cybercriminals. As a result, companies are grappling with a growing threat surface, and many feel vulnerable to attacks delivered through their collaboration tools.
The Growth of Attacks from Non-Email Platforms
Traditionally, email has been the primary attack vector for phishing and other messaging-based attacks. However, recent data from the “State of Email Security” (SOES) report published by Mimecast indicates that newer collaboration technologies are also being targeted. In the past 12 months, 97% of companies surveyed experienced at least one email phishing attack, and three-quarters expected to incur significant costs from email-based attacks. Most concerning, however, is the increase in cyberattacks via collaboration platforms. Nearly three-quarters of companies surveyed feel it is likely or extremely likely that their company will suffer an attack delivered through their collaboration tools.
This threat is only exacerbated by the fact that attacks on messaging and collaboration software are a growing source of compromise. The Anti-Phishing Working Group detected 1.3 million phishing attacks in the third quarter of 2022, up from 1.1 million attacks in the second quarter. Cybercriminals are getting more sophisticated, with 19% of phishing attacks successfully bypassing platform defenses.
While email remains a key attack vector, collaboration tools provide a new and expanding threat surface for bad actors. Companies in various industries, including consumer services, energy, healthcare, and media and entertainment, are particularly susceptible to these threats. It’s crucial to implement effective security measures, including distinguishing bots with human verification tests.
Zero-Trust Web Browser Protection with ConcealBrowse
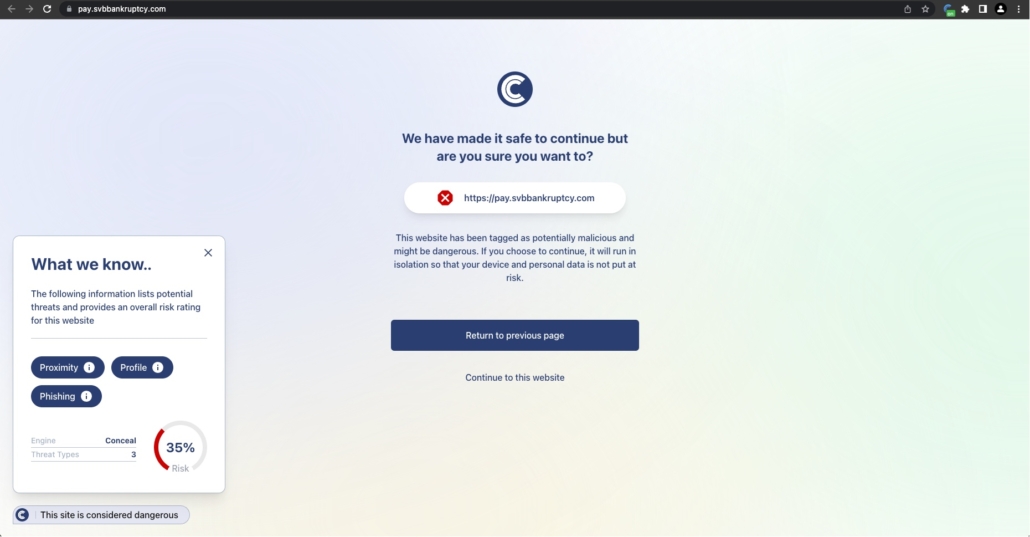
Given the evolving threat landscape, it is essential for businesses to implement zero-trust web browser protection tools like ConcealBrowse. Designed to create a worry-free user experience, ConcealBrowse detects, defends, and isolates malicious and unknown internet activity across all applications, providing robust protection for users.
ConcealBrowse proactively gauges risky internet traffic and determines one of two routes: allowing known “good” URLs to continue on their normal path, blocking it, or opening it in an isolated cloud environment where malicious files and code is not run on the user’s device. Importantly, ConcealBrowse makes proactive decisions about the security risk associated with internet use and automatically isolates risky transactions without interrupting the user experience.
By implementing ConcealBrowse, organizations can effectively defend against phishing attacks targeting not only email but also collaboration platforms. It automatically detects risky internet activity, defends and isolates network and endpoint information, and reduces expenses related to detection, prevention, and response.
Conclusion
In the era of hybrid work and digital collaboration, the threat of phishing attacks is only growing. Cybercriminals are increasingly targeting collaboration platforms, leaving businesses at risk of significant financial and reputational damage. To defend against these evolving threats, businesses must adopt zero-trust web browser protection solutions like ConcealBrowse. With its ability to proactively detect and isolate malicious activity, ConcealBrowse provides a robust line of defense that keeps enterprise users safe and preserves the integrity of their digital assets. Click here to schedule of demo of ConcealBrowse today.
Written By: Conceal Research Team