Browser-Based Threat Report: ConcealBrowse Thwarts Sophisticated Spear Phishing Attack Targeting Conceal CEO
/in Blog /by lacey.andersonConcealBrowse’s Advanced Protection Overcomes Traditional Anti-Phishing Tool Limitations
In a recent spear phishing attack, cybercriminals targeted Conceal’s CEO, Gordon Lawson, bypassing Microsoft 365’s strict anti-phishing protection. This was a highly-targeted attack utilizing advanced techniques to evade detection, but ConcealBrowse effectively protected against the threat by analyzing metadata about the URL used in the attack even though it wasn’t flagged as malicious in traditional intelligence sources.
Bypassing Anti-Phishing Protections
The attackers utilized several techniques intended to defeat common anti-phishing protections:
1. The phishing email contained a screenshot of a typical Microsoft sharing screen linked to an obfuscated URL, operated by a legitimate company, Constant Contact, with a strong reputation.
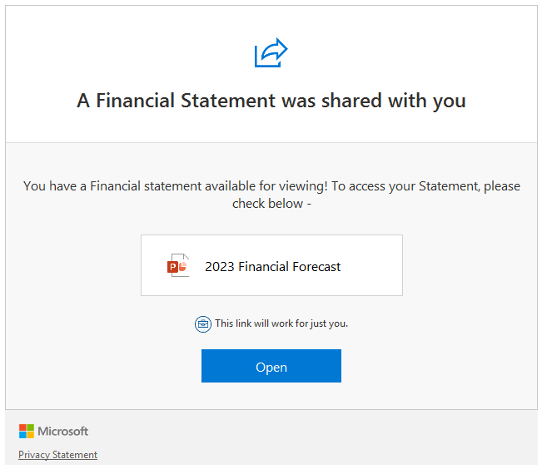
2. The email body contained significant whitespace followed by seemingly legitimate content, which helped it defeat the email-based phishing detection algorithms.
3. The threat actor passed encoded metadata and a URL through a redirect page, which behaved differently on the first visit vs. Subsequent ones. In some cases after the first visit, the victim would be redirected a legitimate Microsoft login page. To defeat sandboxing and similar protections, a captcha was used on the first visit. These steps were aimed at reducing the chances of the malicious site being detected and flagged by automated analytical tools.
Targeted Attack Characteristics
Several indicators suggest this was a targeted attack:
- Compromised sender account: The sender’s reputation, as determined by DKIM, SPF, and Composite authentication, was associated with Microsoft. However, the display name and recipient address raised suspicions, implying the attack originated from a compromised email account.
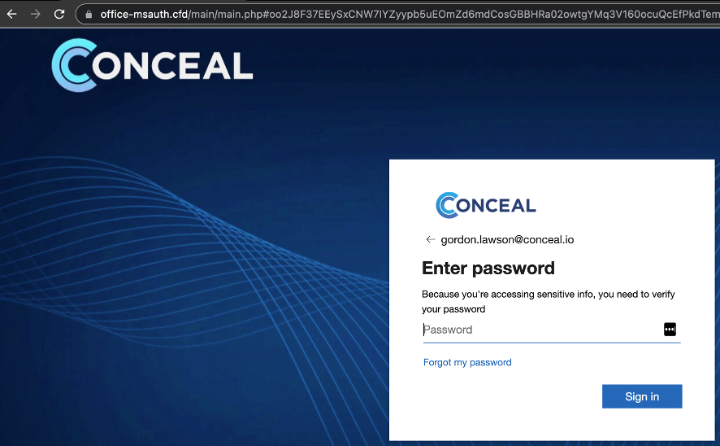
- Customized login page: The phishing email redirected users to a convincing Microsoft login prompt that included the Conceal logo and almost exactly mimicked the real Microsoft authorization page.
ConcealBrowse’s Protection Against the Attack
ConcealBrowse’s advanced security measures effectively protected against the spear phishing attack by focusing on metadata analysis of the URL used in the attack. Even though traditional intelligence sources had not flagged the URL as malicious, ConcealBrowse identified potential risks based on the following indicators:
Domain registration: The recently registered domain prompted ConcealBrowse to isolate the session to protect users. This proactive approach ensured that any potential threats associated with the domain were contained, keeping the business secure.
Multi-layered defense: ConcealBrowse employed multiple data sources and indicators to provide robust protection against the attack, demonstrating the importance of a comprehensive approach to cybersecurity.
Indicators of Compromise:
The following indicators were observed as part of this campaign:
| TYPE | INDICATOR | NOTES |
| DOMAIN | https://office-msauth.cfd/ | Mimicked a Microsoft authentication page, customized with the Conceal logo. |
| IPV4 | 209.141.52.236 |
Conclusion
The sophisticated and targeted spear phishing attack exemplifies the evolving tactics of cybercriminals and the limitations of traditional anti-phishing tools. ConcealBrowse’s advanced protection, based on metadata analysis and multi-layered defense, effectively thwarted the attack. The fact that attackers are constantly evolving to defeat the latest defensive techniques emphasizes the need for businesses to adopt innovative security measures to safeguard sensitive information and maintain a secure environment. Click here to schedule a demo of ConcealBrowse today.
Browser-Based Threat Report: The Tax Day Tangle – Cybercriminals’ Taking Advantage of Stressful Season to Deliver Malware
/in Blog /by lacey.andersonAs the April 18 tax deadline approaches in the United States, accountants and finance professionals are under immense pressure to file tax returns for their clients. Unfortunately, cybercriminals have been taking advantage of this time-sensitive and stressful period to launch a targeted phishing campaign with the goal of gaining unauthorized access to sensitive personal information. According to research done by Microsoft and covered in a recent DarkReading report, cybercriminals are utilizing well-crafted phishing emails and multiple URL redirections to bypass traditional security measures.
The attacks begin with a carefully crafted phishing email sent to Certified Public Accountants (CPAs), accounting firms, and related companies handling tax information. In these emails, the attackers masquerade as existing clients, using subtle social engineering techniques to appear more legitimate. For example, some emails include lines like “I apologize for not responding sooner” and the subject line “Re: 2022,” implying an ongoing correspondence. The inclusion of a password-protected link labeled as “confidential” adds an air of security to the message, making it more believable.
To evade detection by traditional cybersecurity tools, the phishing email contained a link that redirected the recipient through multiple legitimate services. The first redirection leads to an Amazon Web Services click-tracking service, followed by redirection to an ordinary file-hosting site. These layers of redirection serve to evade potential anti-malware detection. Ultimately, the link leads to a .ZIP file containing malicious files designed to trigger the download of the Remcos remote access Trojan (RAT), a malware capable of granting attackers the same level of privileges over the victim’s computer as the victim.
Obviously, the timing of this attack is no coincidence. Cybercriminals strategically initiated the campaign in February, coinciding with the busiest time of year for accountants and finance professionals. They recognized that professionals working long hours and responding to numerous emails late at night might be more susceptible to making mistakes or clicking on malicious links.
Fortunately, Conceal’s secure browser extension, ConcealBrowse, can play a vital role in protecting users. ConcealBrowse acts as a proactive security layer, making real-time decisions about the security risk associated with internet use and automatically isolating risky transactions without interrupting the user. It opens risky sites in an isolated environment, ensuring that no malicious code or files are ever executed on the user’s device. Multiple browser redirect strategies like the one implemented in this attack cannot evade detection by ConcealBrowse, as every URL loaded into the browser is checked in real-time. So, even if the first malicious URL is the third in a series of redirects, ConcealBrowse will identify the URL as malicious and take appropriate action.
The Remcos RAT phishing campaign serves as yet another reminder of the evolving tactics used by cybercriminals to exploit vulnerabilities in human behavior. With the use of social engineering and multiple URL redirections, attackers can bypass traditional security measures. However, ConcealBrowse can provide a robust extra layer of defense against such attacks. As Tax Day approaches, we urge individuals and organizations to exercise caution and utilize tools like ConcealBrowse to mitigate the risk of falling victim to cyber-attacks. Click here to sign up for a live demo of ConcealBrowse and see how it can help protect your organization today.
Tech Spotlight: ConcealBrowse Dashboard – Enhancing Visibility and Security Control
/in Blog /by Chad AndersonIn today’s digital landscape, organizations are continuously exposed to threats that can bypass traditional security controls. ConcealBrowse offers a comprehensive solution that provides security to malicious activity that may go undetected by other security measures. Additionally, the corresponding dashboard provides enhanced visibility and insights into activities that may go unnoticed by other tools. In this tech spotlight blog, we’ll explore the features of the ConcealBrowse Dashboard and discuss how it can help organizations improve their security posture.
ConcealBrowse Dashboard Features
The ConcealBrowse Dashboard offers a range of reports and graphs that provide valuable insights into isolated sessions and user behavior. Some of these include:
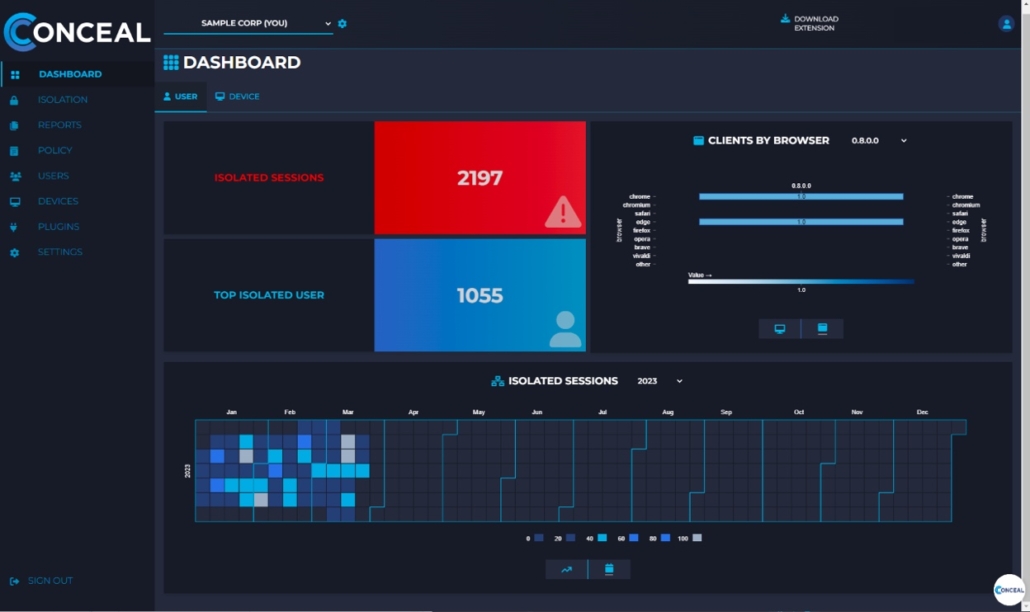
Isolated Sessions: This report displays a detailed view of all isolated sessions, allowing security teams to monitor and assess potential threats effectively.
Top Isolated Entities: This report highlights the most frequently isolated URLs, enabling organizations to identify high-risk areas and prioritize corresponding remediation efforts.
Highest Isolated Sessions: This report ranks users or devices based on their number of isolated sessions, helping security teams identify targeted individuals or those who may require additional training.
Visualizing Security Data
The ConcealBrowse Dashboard offers various graphs that enable organizations to visualize and analyze security trends effectively. Some key visualizations include:
Trend of Isolated Sessions: This graph displays the overall trend of isolated sessions over time, helping organizations identify patterns and respond proactively to emerging threats.
Number of Isolated Sessions: This visualization provides a clear overview of the total number of isolated sessions, allowing security teams to gauge the effectiveness of their security measures.
Isolated Sessions per Day: This graph shows the daily count of isolated sessions, enabling organizations to track and manage security incidents more effectively.
OS and Browsers Hooked Up: This visualization offers insights into the operating systems and browsers connected to the ConcealBrowse platform, helping organizations tailor their security strategies according to the specific technologies in use.
Enhancing Security Through Visibility
The ConcealBrowse Dashboard provides organizations with the visibility needed to identify and respond to security threats that might bypass conventional security controls. By offering comprehensive insights into isolated sessions and user behavior, the dashboard enables organizations to optimize their security measures, identify targeted individuals, and provide additional training where necessary.
Conclusion
In an increasingly complex threat landscape, organizations must remain vigilant and adopt security solutions that provide comprehensive visibility into their digital environments. The ConcealBrowse Dashboard offers a powerful solution to help organizations stay ahead of potential threats and maintain a robust security posture. By leveraging the dashboard’s advanced features and visualizations, security teams can make informed decisions and protect their organizations from emerging risks.
Browser-Based Threat Alert: Increased Phishing Attacks on Collaboration Platforms Highlight the Importance of Zero-Trust Browser Protection
/in Blog /by Chad AndersonPhishing attacks have long been a serious threat to businesses, but recent reports indicate that the problem is becoming even more pervasive. Email remains a primary target, but attackers are also expanding their focus to collaboration platforms such as Slack and Microsoft Teams. With the shift to hybrid work environments, these platforms have become popular avenues for exploitation by opportunistic cybercriminals. As a result, companies are grappling with a growing threat surface, and many feel vulnerable to attacks delivered through their collaboration tools.
The Growth of Attacks from Non-Email Platforms
Traditionally, email has been the primary attack vector for phishing and other messaging-based attacks. However, recent data from the “State of Email Security” (SOES) report published by Mimecast indicates that newer collaboration technologies are also being targeted. In the past 12 months, 97% of companies surveyed experienced at least one email phishing attack, and three-quarters expected to incur significant costs from email-based attacks. Most concerning, however, is the increase in cyberattacks via collaboration platforms. Nearly three-quarters of companies surveyed feel it is likely or extremely likely that their company will suffer an attack delivered through their collaboration tools.
This threat is only exacerbated by the fact that attacks on messaging and collaboration software are a growing source of compromise. The Anti-Phishing Working Group detected 1.3 million phishing attacks in the third quarter of 2022, up from 1.1 million attacks in the second quarter. Cybercriminals are getting more sophisticated, with 19% of phishing attacks successfully bypassing platform defenses.
While email remains a key attack vector, collaboration tools provide a new and expanding threat surface for bad actors. Companies in various industries, including consumer services, energy, healthcare, and media and entertainment, are particularly susceptible to these threats. It’s crucial to implement effective security measures, including distinguishing bots with human verification tests.
Zero-Trust Web Browser Protection with ConcealBrowse
Given the evolving threat landscape, it is essential for businesses to implement zero-trust web browser protection tools like ConcealBrowse. Designed to create a worry-free user experience, ConcealBrowse detects, defends, and isolates malicious and unknown internet activity across all applications, providing robust protection for users.
ConcealBrowse proactively gauges risky internet traffic and determines one of two routes: allowing known “good” URLs to continue on their normal path, blocking it, or opening it in an isolated cloud environment where malicious files and code is not run on the user’s device. Importantly, ConcealBrowse makes proactive decisions about the security risk associated with internet use and automatically isolates risky transactions without interrupting the user experience.
By implementing ConcealBrowse, organizations can effectively defend against phishing attacks targeting not only email but also collaboration platforms. It automatically detects risky internet activity, defends and isolates network and endpoint information, and reduces expenses related to detection, prevention, and response.
Conclusion
In the era of hybrid work and digital collaboration, the threat of phishing attacks is only growing. Cybercriminals are increasingly targeting collaboration platforms, leaving businesses at risk of significant financial and reputational damage. To defend against these evolving threats, businesses must adopt zero-trust web browser protection solutions like ConcealBrowse. With its ability to proactively detect and isolate malicious activity, ConcealBrowse provides a robust line of defense that keeps enterprise users safe and preserves the integrity of their digital assets. Click here to schedule of demo of ConcealBrowse today.
Written By: Conceal Research Team
The Growing Impact of Cybersecurity on Credit Ratings: What Companies Need to Know
/in Blog /by Chad AndersonAs cybersecurity becomes an increasingly vital aspect of a company’s operations, credit rating agencies are beginning to incorporate cybersecurity factors into their evaluations of corporate creditworthiness. This shift highlights the growing importance of strong cybersecurity practices in maintaining a company’s financial stability and reputation. In this blog post, we will discuss how credit rating agencies are now considering cybersecurity in their assessments and what companies can do to improve their cyber risk management.
Cybersecurity as a Credit Rating Factor
A recent report by The Washington Post revealed that credit rating agencies such as Moody’s, S&P Global Ratings, and Fitch Ratings are increasingly looking at a company’s cybersecurity posture when determining credit ratings. This move follows a growing trend of cyberattacks targeting corporations, which have led to significant financial losses and reputational damage for the affected businesses.
Companies that have suffered major cybersecurity incidents, such as data breaches or ransomware attacks, are now more likely to see their credit ratings downgraded. This can lead to higher borrowing costs and a reduced ability to access capital markets. On the other hand, companies with robust cybersecurity practices may receive more favorable credit ratings, potentially lowering their cost of capital and increasing their attractiveness to investors.
How can companies protect their bottom line?
To effectively incorporate cybersecurity factors into credit ratings, agencies are increasingly relying on cyber risk assessments. These assessments aim to evaluate a company’s cyber risk exposure and its ability to prevent, detect, and respond to cyber threats. Credit rating agencies may also consider the potential financial impact of a cyber incident on a company’s balance sheet, cash flow, and overall creditworthiness.
The Post report notes that small and medium sized businesses are the least likely to invest enough in cyber security measures. Tools like ConcealBrowse can provide tremendous bang for the buck, providing critical missing coverage over an entire organization at a manageable cost.
Given the growing importance of cybersecurity in credit ratings, companies must prioritize cyber risk management in their overall business strategy. Here are a few steps businesses can take to enhance their cybersecurity posture:
- Implement a comprehensive cybersecurity framework: Companies should adopt a recognized cybersecurity framework, such as the NIST Cybersecurity Framework or the ISO/IEC 27001 standard, to guide their cybersecurity policies and procedures.
- Embrace zero-trust principles wherever possible: Employees are often the weakest link in any cybersecurity program. While training and awareness programs can reduce the chances of falling victim to phishing or other types of trust-based attacks, invest in solutions like ConcealBrowse that take decisions on trust and risk assessment out of the hands of the end user.
- Regularly assess cyber risk exposure: Conducting regular cyber risk assessments can help organizations identify vulnerabilities and gaps in their cybersecurity defenses, allowing them to take appropriate remedial actions.
- Collaborate with industry peers and government agencies: Sharing information on cyber threats and best practices with other companies and government organizations can help businesses stay ahead of emerging cyber risks.
- Engage with credit rating agencies: Companies should proactively engage with credit rating agencies to understand their cybersecurity expectations and communicate their efforts to address cyber risks.
Conclusion:
The incorporation of cybersecurity factors into credit ratings highlights the growing recognition of cyber risk as a significant business concern. Companies that prioritize cyber risk management and demonstrate robust cybersecurity practices are more likely to receive favorable credit ratings, which can have tangible benefits in terms of lower borrowing costs and increased investor confidence. By taking proactive steps to improve their cybersecurity posture, businesses can better position themselves for long-term success in an increasingly interconnected and cyber-risky world.
To find out more about how ConcealBrowse can make your business more secure and less risky to creditors and investors, click here to schedule a demo today.
Browser-Based Threat Alert: SVB Opportunistic Phishing Attacks
/in Blog /by Chad AndersonAs all security professionals know, phishing attacks are a constant threat.
Cybercriminals are relentless in their efforts to deceive individuals into revealing sensitive information, and the consequences can be devastating. March 2023 witnessed a prime example of how a crisis can create a ripe environment for phishing campaigns to thrive. The collapse of Silicon Valley Bank (SVB) and the subsequent phishing attacks targeting its customers offer a cautionary tale and highlight the importance of zero-trust protection measures.
SVB, a major U.S. bank known for providing financial services to some of the largest tech investors and startups, collapsed on March 10, 2023. Federal regulators under the control of the Federal Deposit Insurance Corporation (FDIC) took over the bank after depositors rushed to withdraw billions of dollars in deposits. The financial crisis garnered worldwide attention and created an atmosphere of chaos and stress that cyber criminals naturally sought to exploit. Amid the bank’s collapse, a series of phishing campaigns impersonating SVB began to emerge. A recent article on Cybersecurity Magazine conducted an analysis of SVB-related phishing attacks and noted that the ongoing banking crisis is likely to provide more opportunities for attackers as more banks become stressed and fail.
In the context of online financial services, phishing attacks can involve fake login pages or emails that impersonate legitimate financial institutions. Unsuspecting victims may provide sensitive information, such as login credentials or financial data, to these fake websites. This information can then be used for criminal activities like identity theft or financial fraud. In fact, the credentials themselves can have tremendous value on the open market, with verified admin accounts in some cases being sold for up to $120,000. In some cases, victims are redirected to the real site, giving them the impression that they are interacting with the legitimate institution while providing their credentials to attackers.
Attackers in the SVB phishing campaign created domains that closely resembled SVB’s name, often containing minor variations and financial terms to lure individuals into clicking on malicious links. More than 90 new domains were registered for use in attacks against targets, mainly in the U.S. The report identified one Turkish attacker that began utilizing a fraudulent domain within a few hours of its registration.
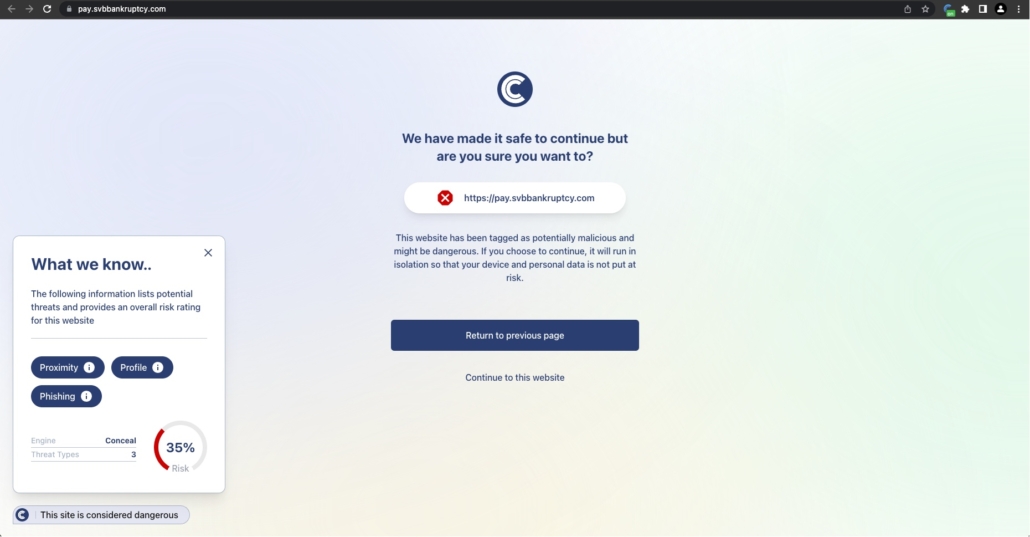
The aftermath of the SVB collapse and the ensuing phishing attacks underscore the necessity of proactive cybersecurity measures. In times of crisis, hackers often prey on fear and confusion, making it essential for individuals to remain vigilant. However, even with extreme vigilance and thorough cyber security training, crises like the SVB collapse can impair user’s judgment about messages related to the event. That is why it’s critical to remove the burden of judging risk from the user and put it in the hands of objective security tools like ConcealBrowse.
The browser-based phishing protection provided by ConcealBrowse is an indispensable tool in mitigating the risks of phishing attacks and safeguarding valuable information when end users don’t know who they can trust. The SVB phishing campaign serves as a reminder of the ever-present threat of phishing and the need for robust security measures. By utilizing tools like ConcealBrowse and staying informed about the latest cybersecurity threats, individuals and organizations can better protect themselves from falling victim to cybercriminals’ deceptive tactics.
Click here to schedule a demo of ConcealBrowse today and see how it can keep your users safe from opportunistic attacks like these.
Written By: Conceal Research Team
How to Increase Your Profitability as an MSP
/in Blog /by Chad AndersonMaintain MSP Profitability in an Era of Economic Uncertainty
We know that as a managed service provider increased profitability is key to growth and success in the industry. As a MSP first company, here are some strategies that we have seen increase profitability as an MSP:
Recurring Revenue
Maximize on opportunities where you can offer services that generate revenue that is recurring. Examples of such services include managed security services. This approach helps reduce the need to strategize on one-time product work with a customer and rather lets you focus on a stable revenue stream.
Effective Operations
Effective operations come down to the tools and processes being leveraged to provide your services to a customer. When effective, these operations can increase productivity while reducing costs and minimizing errors. Manners by which effective operations can be achieved is through automation as well as through the standardization of processes and procedures and effective project management.
Competitive Pricing
If you are able to develop an optimized pricing model, you can maximize revenue while remaining competitive in the MSP market. A common mechanism for competitive pricing requires the MSP to leverage value-based pricing so that you can charge based on the value the service you are providing brings to the customer.
Service Expansion
Continuously invest in offering development so that you are offering the services that meet the needs of your customers. We see MSPs breaking into the security market, a relatively untapped market by MSPs to date. This allows an increase in revenue streams and provides the opportunity to both upsell and cross-sell to customers.
Strategic Partnerships
Investing in partners that complement the offerings, solutions and missions of your organization is key to expanding your service offering even further. As mentioned above, continuous offering development is key to ensuring you have the offerings your customers need. By investing in strategic partnerships, you can provide you customers with a more comprehensive solution.
Cost Management
To increase profitability, MSP’s must manage and minimize costs. Determining unnecessary expenses and managing costs effectively are key to improving profitability. This optimization can be done by revisiting staffing levels, implementing cost-saving technology and ensuring the most beneficial vendor contracts.
Your Next Strategic Partner
Here at Conceal, we are invested in helping you implement a strategy that includes maximizing profitability. A strategic partnership with Conceal allows you, as an MSP, to expand your services while streamlining effective operations and investing in services that result in recurring revenue. Additionally, ConcealBrowse enhances your ability to manage cost by minimizing the need for user interaction. The lightweight implementation and operation of the browser plugin allows you to best protect your customers at the edge while also minimizing the resourcing needed to address alerts from the browser in the SOC.
ConcealBrowse offers a tremendous opportunity to provide innovative solutions that address the top two cyber threats affecting small and midsize companies: ransomware and credential theft. A simple, drop-in solution, ConcealBrowse can be easily added to existing security packages or be a stand-alone solution for companies that lack protection, allowing them to instantly add a security control that may have seemed out of reach with their existing security budget.
Position yourself for long-term growth and success by investing in a strategy that increases your overall profitability. Become a Conceal Partner today to start maximizing your profitability and expand your services to secure the edge.